https://github.com/lutfumertceylan/top25-parameter
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon. 🛡️⚔️🧙
https://github.com/lutfumertceylan/top25-parameter
bugbounty bugbountytips infosec pentest-tool pentesting security vulnerability-detection vulnerability-research xss-detection
Last synced: 3 months ago
JSON representation
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon. 🛡️⚔️🧙
- Host: GitHub
- URL: https://github.com/lutfumertceylan/top25-parameter
- Owner: lutfumertceylan
- License: other
- Created: 2020-04-27T20:40:09.000Z (almost 6 years ago)
- Default Branch: master
- Last Pushed: 2024-06-09T23:36:24.000Z (over 1 year ago)
- Last Synced: 2025-01-30T00:42:47.312Z (12 months ago)
- Topics: bugbounty, bugbountytips, infosec, pentest-tool, pentesting, security, vulnerability-detection, vulnerability-research, xss-detection
- Homepage: https://owasp.org/www-project-top-25-parameters/
- Size: 355 KB
- Stars: 1,724
- Watchers: 44
- Forks: 270
- Open Issues: 2
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - lutfumertceylan/top25-parameter - For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon. 🛡️⚔️🧙 (Others)
README
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon
---
## What is the OWASP Top 25 Parameters 🧙⚔️
For basic researches, top 25 vulnerable parameters based on frequency of use with reference to various articles. These parameters can be used for automation tools or manual recon. Although the prevalence percentages of these parameters cannot be proven precisely.
Data sources include numerous articles, blogs, and other resources obtained via OSINT and other open-source projects including work similar to that of Jason Haddix and HUNT.
This repo contains common parameters of the following vulnerabilities:
```
- Cross-Site Scripting (XSS)
- Server-Side Request Forgery (SSRF)
- Local File Inclusion (LFI)
- SQL Injection (SQLi)
- Remote Code Execution (RCE) - [for GET and POST methods]
- Open Redirect
```
## ToC
- [Cross-Site Scripting](#top-25-cross-site-scripting-xss-parameters-for-trbughunters-openbugbounty)
- [Server-Side Request Forgery](#top-25-server-side-request-forgery-ssrf-parameters-for-trbughunters)
- [Local File Inclusion](#top-25-local-file-inclusion-lfi-parameters-for-trbughunters)
- [SQL Injection](#top-25-sql-injection-parameters-for-trbughunters)
- [Remote Code Execution](#top-25-remote-code-execution-rce-parameters-get-based-for-trbughunters)
- [Open Redirect](#top-25-open-redirect-parameters-for-lutfumertceylan)
---
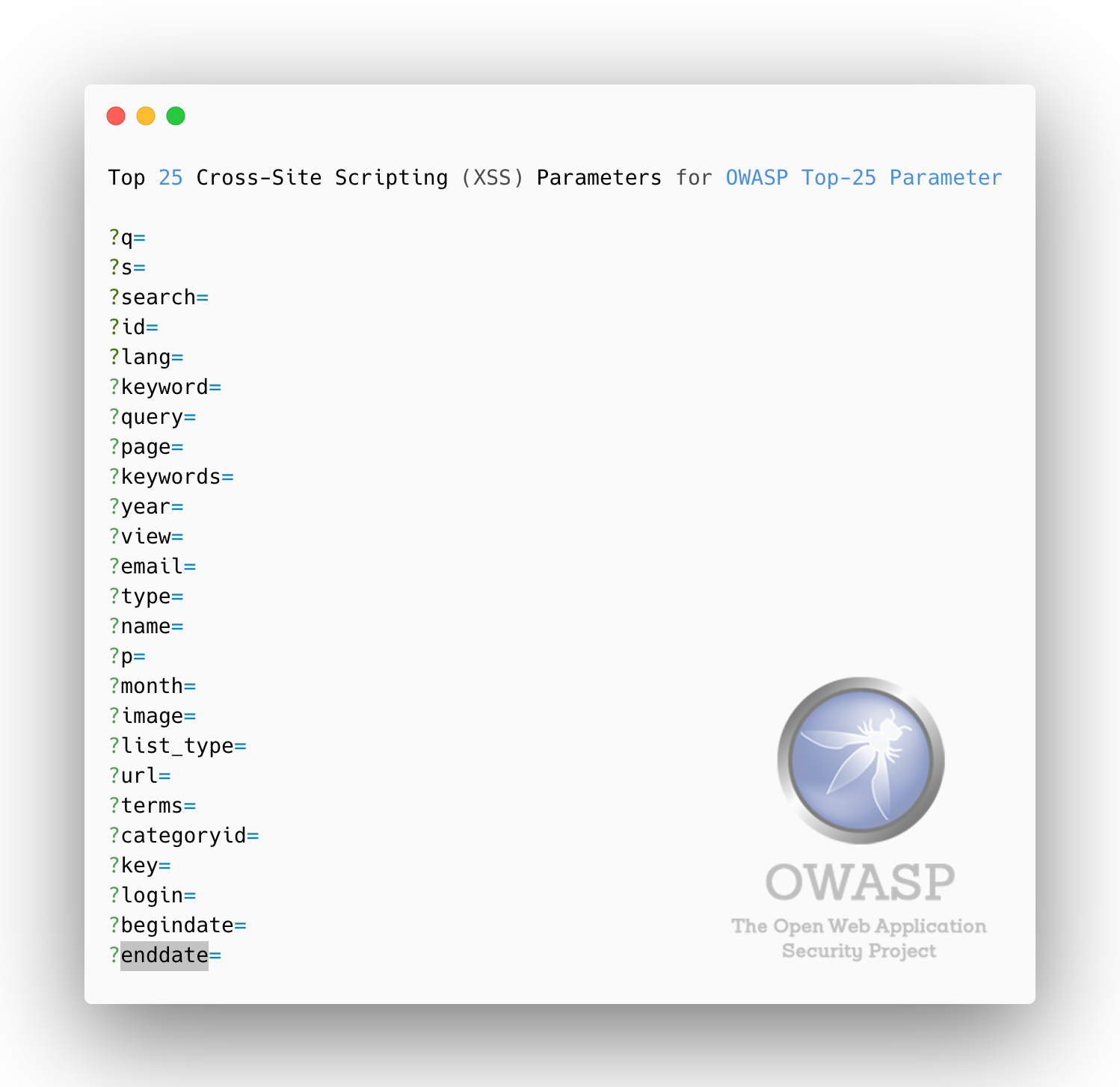
### Top 25 **Cross-Site Scripting (XSS)** Parameters
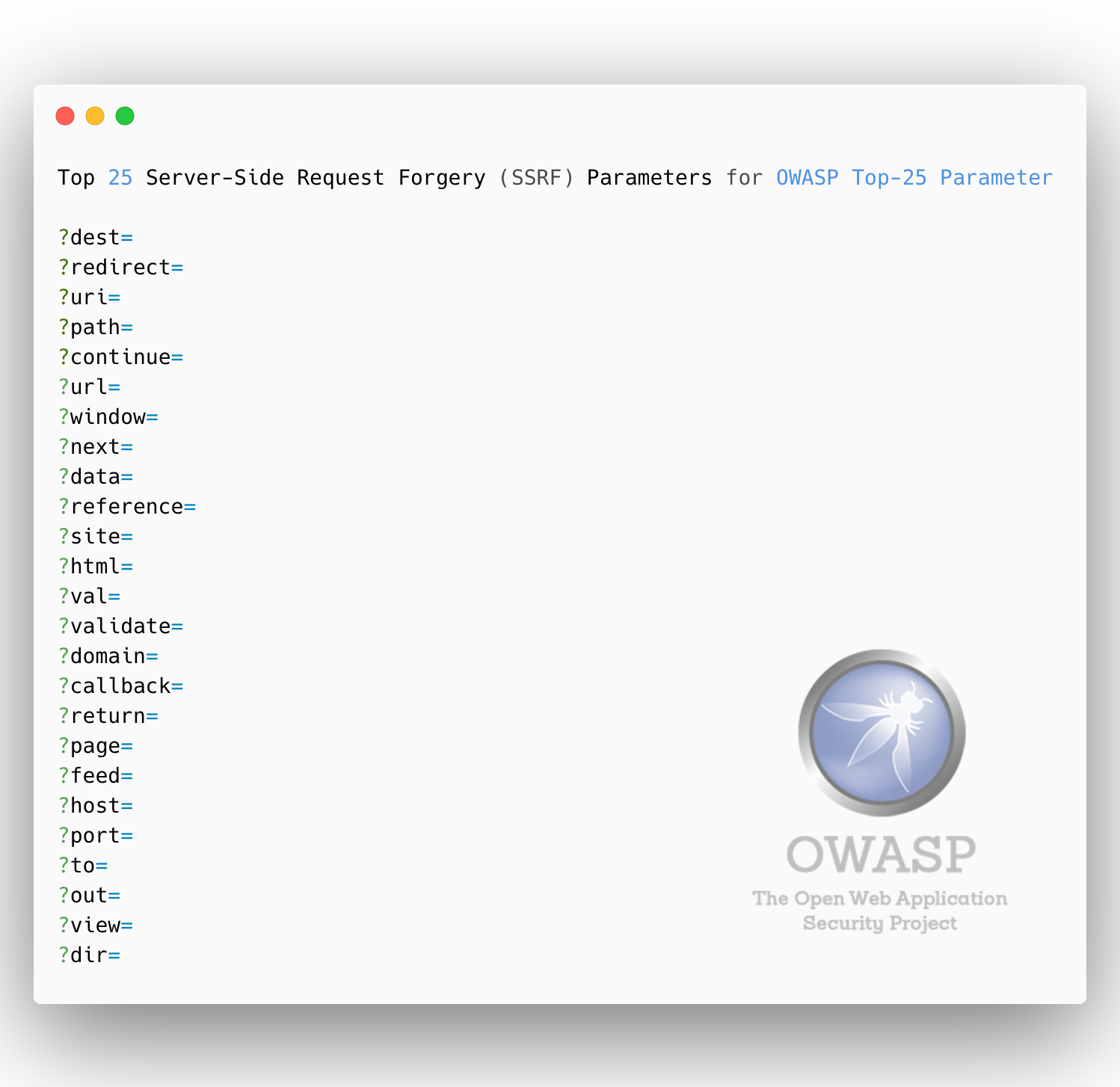
### Top 25 **Server-Side Request Forgery (SSRF)** Parameters
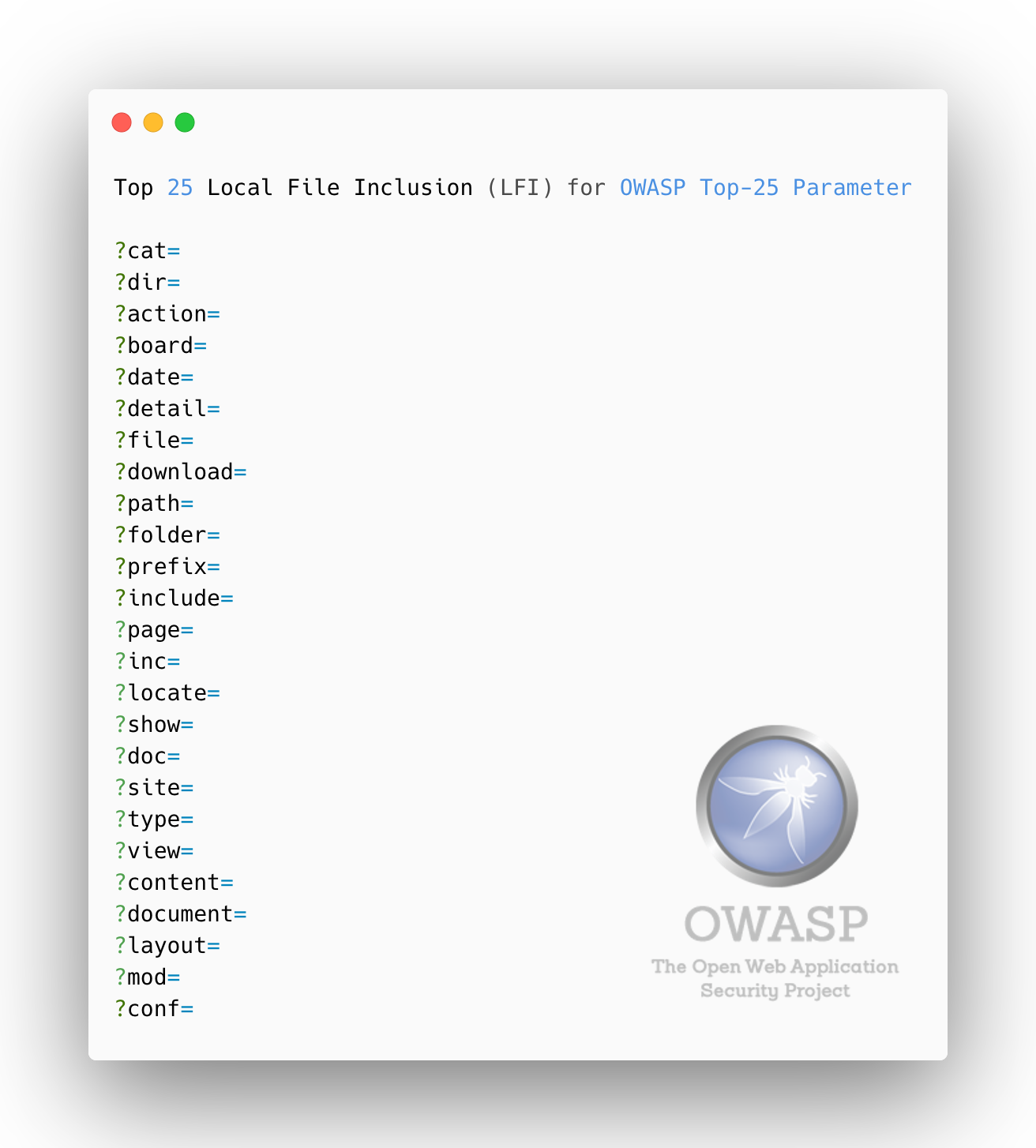
### Top 25 **Local File Inclusion (LFI)** Parameters
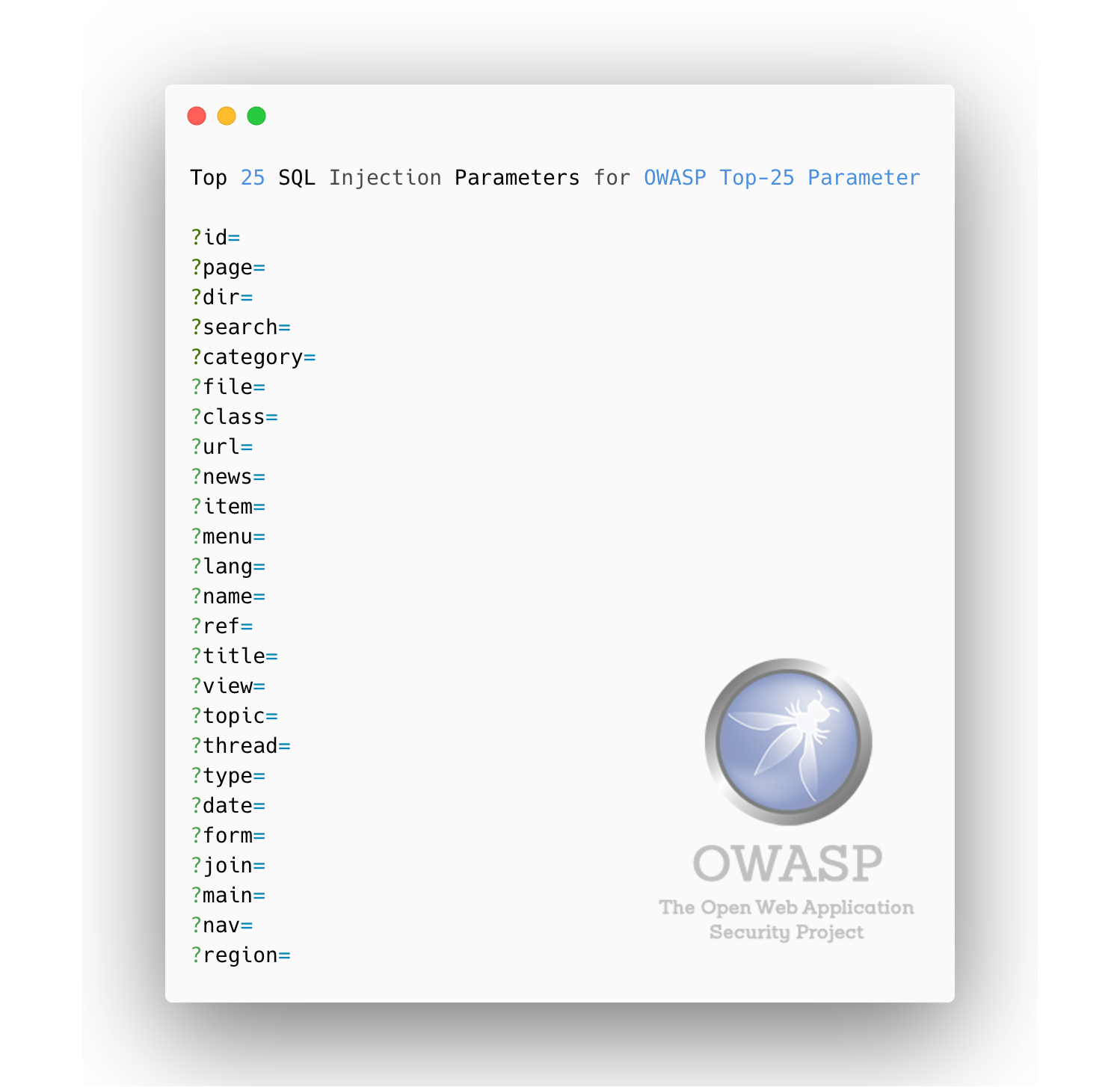
### Top 25 **SQL Injection** Parameters
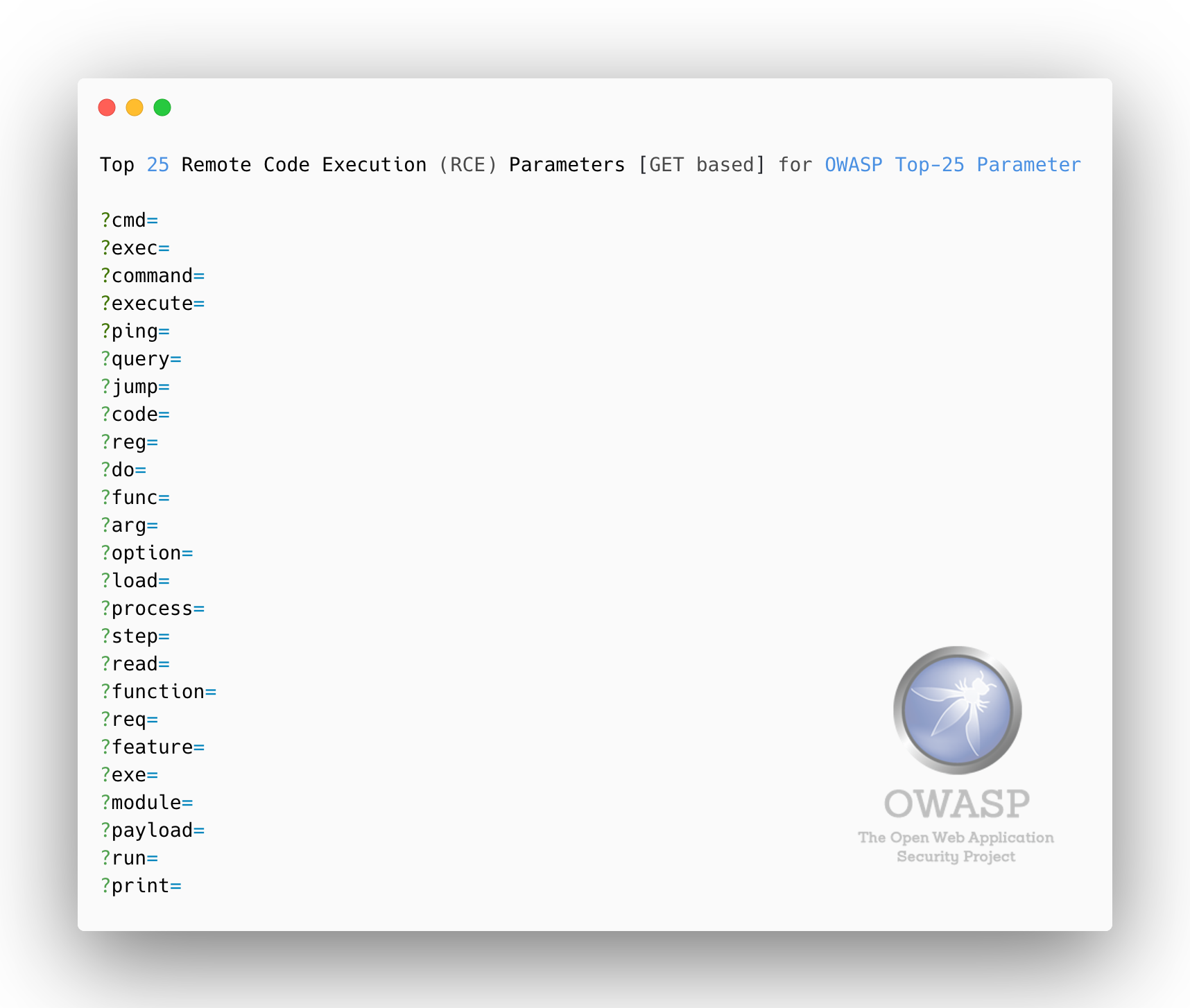
### Top 25 **Remote Code Execution (RCE)** Parameters [GET based]
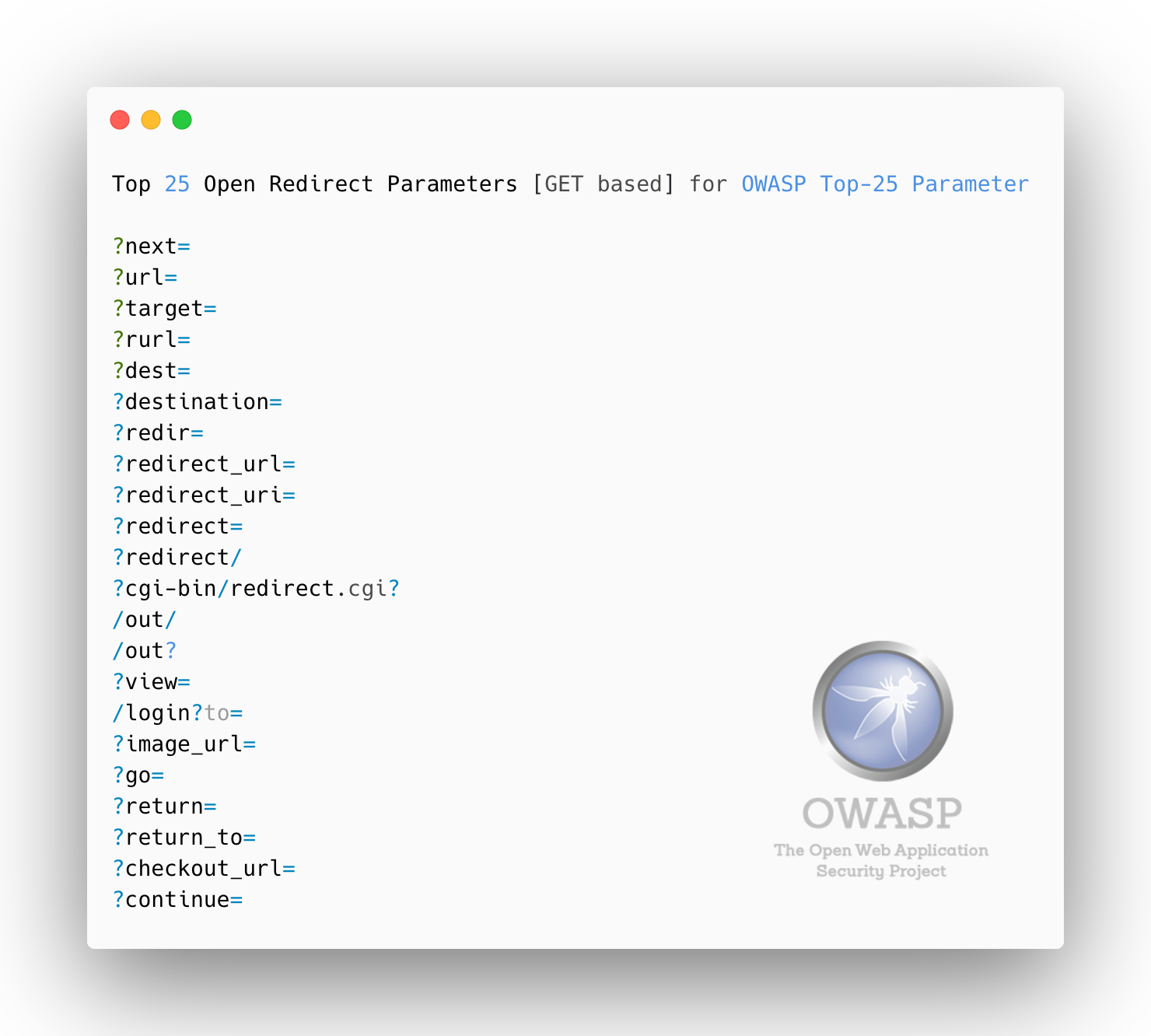
### Top 25 **Open Redirect** Parameters [GET based]
## How can I contact you?
To report issues or make suggestions for the Top-25 Parameters, please use [GitHub Issues](https://github.com/OWASP/www-project-top-25-parameters/issues).
For everything else, we're easy to answer your e-mail :
1. Send an e-mail to [lutfu.mertceylan[at]owasp.org](mailto:lutfu.mertceylan[at]owasp.org)
2. Send an e-mail to [info[at]lutfumertceylan.com.tr](mailto:info@lutfumertceylan.com.tr)
You can @ us on Twitter [@lutfumertceylan](https://twitter.com/lutfumertceylan).



