https://github.com/m6a-UdS/dvca
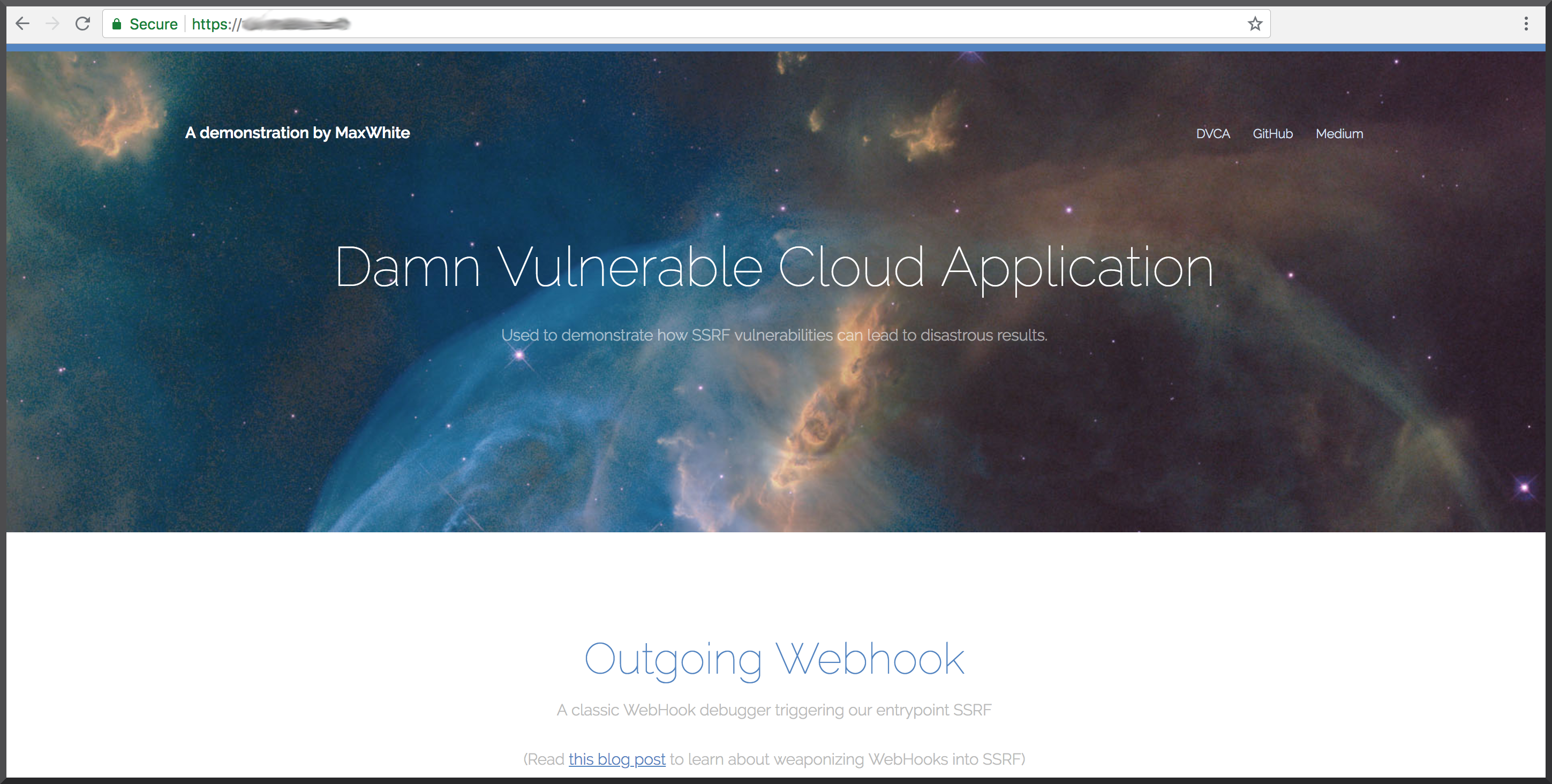
Damn Vulnerable Cloud Application
https://github.com/m6a-UdS/dvca
Last synced: 2 months ago
JSON representation
Damn Vulnerable Cloud Application
- Host: GitHub
- URL: https://github.com/m6a-UdS/dvca
- Owner: m6a-UdS
- Created: 2018-08-17T22:06:01.000Z (almost 7 years ago)
- Default Branch: master
- Last Pushed: 2018-09-12T18:58:37.000Z (almost 7 years ago)
- Last Synced: 2024-02-20T14:07:07.425Z (over 1 year ago)
- Language: CSS
- Homepage:
- Size: 3.72 MB
- Stars: 164
- Watchers: 9
- Forks: 48
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- Awesome-CloudSec-Labs - DVCA - hosted demo lab | [Maxime Leblanc](https://medium.com/@mleblanc_82306) | Deploy a Damn Vulnerable Cloud Application in your own AWS account to practice privilege escalation | (Sorted by Technology and Category)
- awesome-sec-challenges - Damn Vulnerable Cloud Application - an intentionally vulnerable cloud application to teach privilege escalation on Amazon Web Services (AWS). (Capture The Flag / Cloud-Focused)
README
# Damn Vulnerable Cloud Application
This is a demonstration project to show how to do privilege escalation on AWS. DO NOT deploy this on an AWS account unless you know very well what you are doing!
## Implemented Cloud Providers & Vulnerabilities
More details about how to use it are available on my [blog](https://medium.com/poka-techblog/privilege-escalation-in-the-cloud-from-ssrf-to-global-account-administrator-fd943cf5a2f6). For now, it's very AWS-centric, but the frontend is completely agnostic to the backend's technology, so if you want to contribute with a backend using other Cloud providers, I gladly accept PRs.
## Prerequisites
- A domain name managed by AWS
- The ACM Certificate ID associated to this domain
- A Wildcard Certificate associated to this domain
- The Hosted Zone ID associated to this domain
## Deployment
_In theory_, you should be able to deploy the Damn Vulnerable Cloud Application with a simple command:
```
make all DOMAIN_NAME= \
ROOT_CERTIFICATE= \
CERTIFICATE= \
HOSTED_ZONE=
```
But the project is modular, so you could also deploy it in multiple steps. Typical `make` resources would be: prerequisites, frontend and a backend of your choice
```
make prerequisites DOMAIN_NAME= \
CERTIFICATE= \
HOSTED_ZONE=
make frontend DOMAIN_NAME= \
ROOT_CERTIFICATE= \
HOSTED_ZONE=
make fargate DOMAIN_NAME= \
CERTIFICATE= \
HOSTED_ZONE=
```
Just be careful: The frontend needs your root domain Certificate ID for the CloudFront distribution, while the rest just needs your wildcard Certificate ID
In the end, you should end-up with something like this :-)