https://github.com/mikevoronov/libp2p-dissector
Project for ETHBerlin hackaton bounty: https://github.com/ethberlinzwei/Bounties/issues/20
https://github.com/mikevoronov/libp2p-dissector
libp2p lua secio wireshark wireshark-dissector
Last synced: 6 months ago
JSON representation
Project for ETHBerlin hackaton bounty: https://github.com/ethberlinzwei/Bounties/issues/20
- Host: GitHub
- URL: https://github.com/mikevoronov/libp2p-dissector
- Owner: mikevoronov
- Created: 2019-08-25T05:17:59.000Z (about 6 years ago)
- Default Branch: master
- Last Pushed: 2019-09-12T06:29:36.000Z (about 6 years ago)
- Last Synced: 2025-03-24T00:51:22.194Z (7 months ago)
- Topics: libp2p, lua, secio, wireshark, wireshark-dissector
- Language: Lua
- Homepage:
- Size: 2.49 MB
- Stars: 16
- Watchers: 1
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# Libp2p dissector
A Wireshark Lua plugin to dissect several libp2p protocols with support of SECIO decryption. This plugin indended to run with go-libp2p-secio [fork](https://github.com/michaelvoronov/go-libp2p-secio) since it supports dumping secret symmetric keys.
## Usage:
Copy the whole directory into your Wireshark `Personal Plugins` folder. To find out where it is located, open Wireshark and go to **Help->About Wireshark** and it will be listed in the **Folders** tab. You may need to create the folder the first time.
Another prerequisite is to define environment variable `LIBP2P_SECIO_KEYLOG` that should be pointer to the file with secret keys.
To run plugin you need to open Wireshark, sniff (or load from a dump) network traffic and then activate plugin via **Help->About Wireshark**.
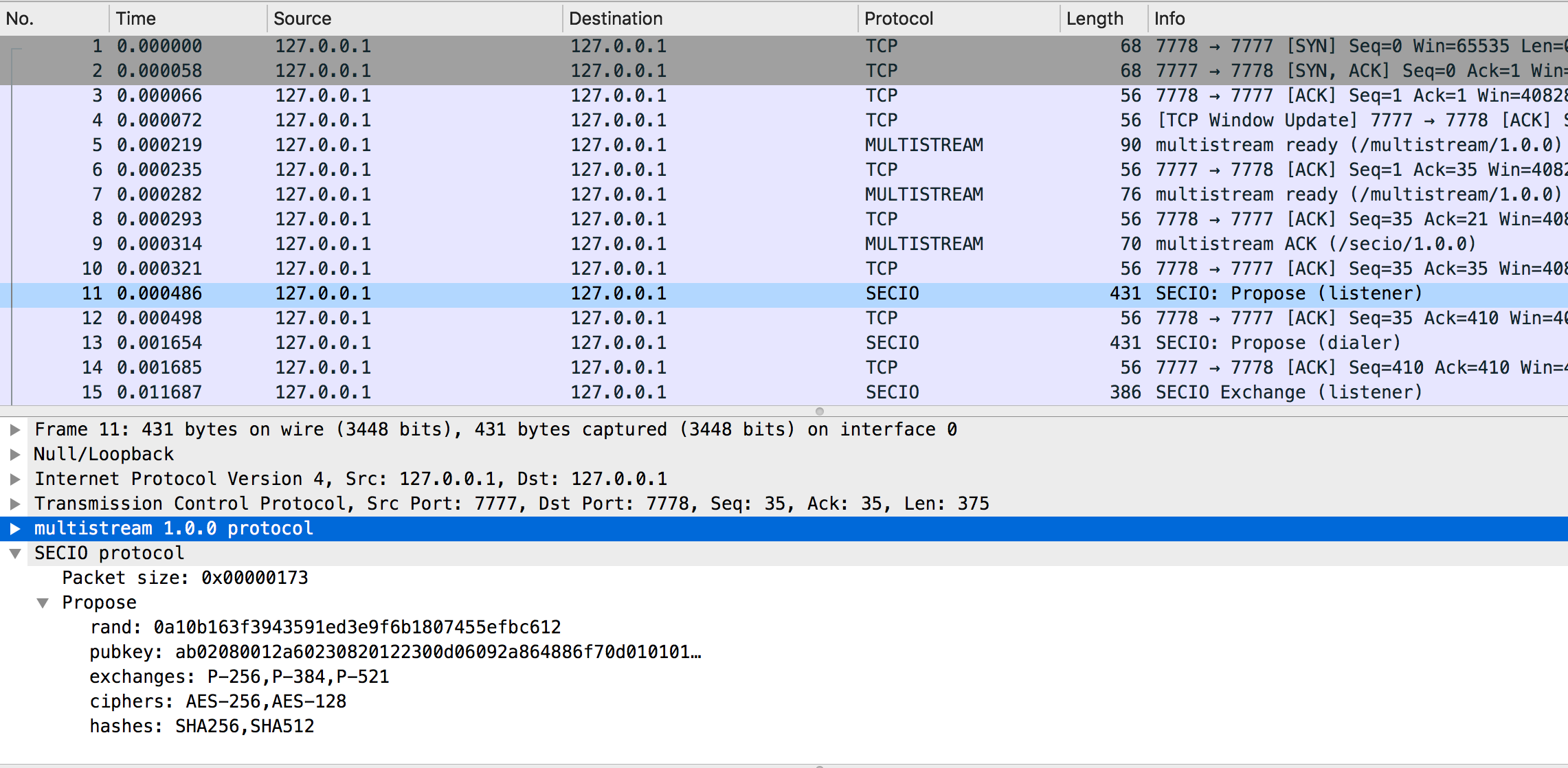
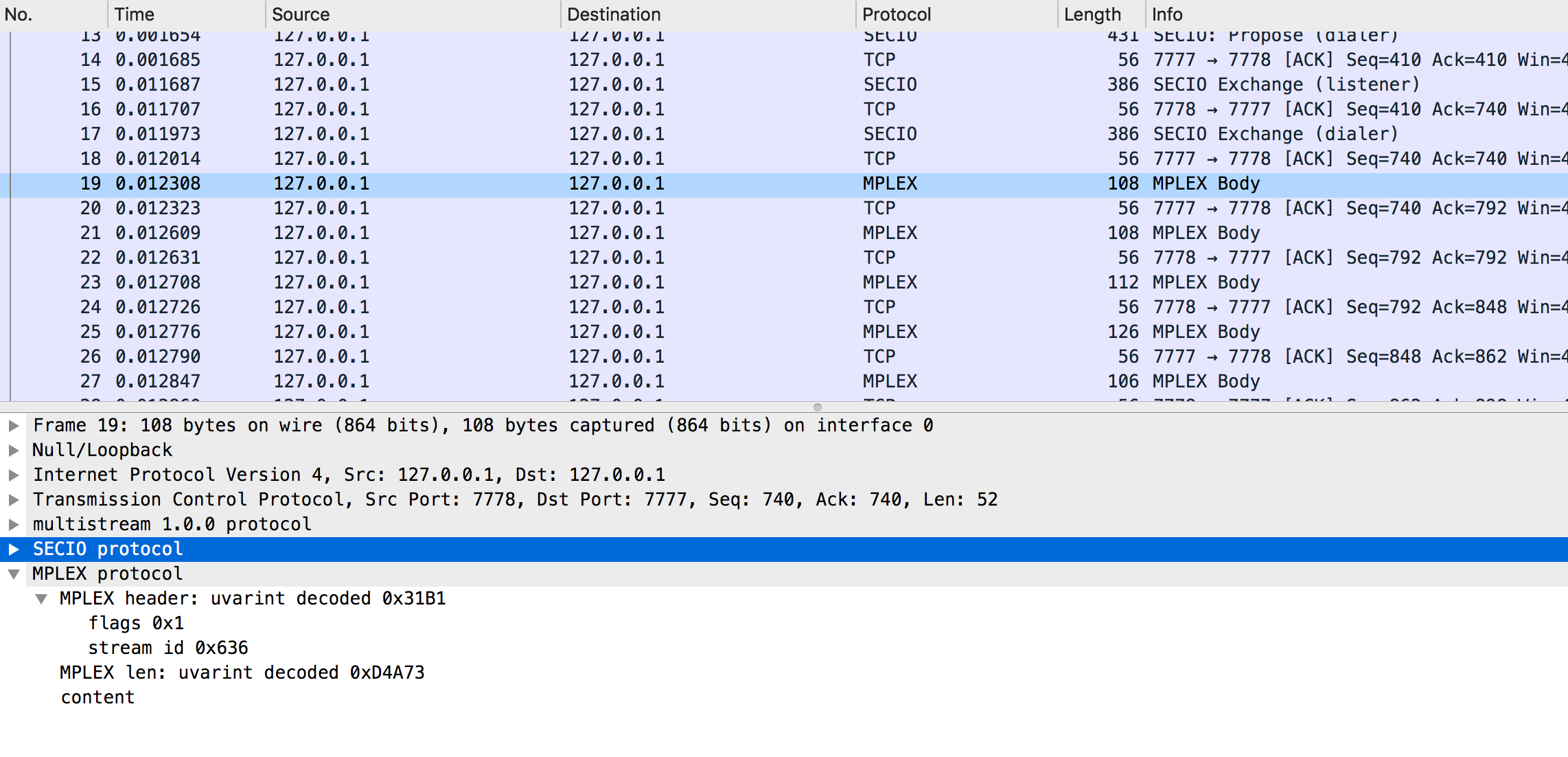
## Prerequisites
You need some lua packets installed:
- ffi (`luarocks install --server=http://luarocks.org/dev luaffi`)
- pb (`luarocks install lua-protobuf`)
- protoc (`luarocks install protoc`)
- lua (`luarocks install csv`)
- base64 (`luarocks install lbase64`)
Please be sure, that Wireshark has access to these plugins on your setup.
## Supported protocols
- [X] multistream 1.0.0
- [X] secio 1.0.0
- [X] mplex 1.0.0
- [ ] yamux
- [ ] spdy
- [ ] ipfs
## High-level dissecting algorithm overview
1. At first, multistream dissector is registred as the heuristic dissector
2. This dissecctor looks for the "/multistream/1.0.0" string in traffic, then parses multistream handshaked packets and, finally, calls secio dissector.
3. In its turn, secio dissector waits for Propose and Excahnge packets. And after receiving the last Exchange packet will try to open config file and try to find the last record for corresponding in/out ip:port. It is expected that after the last Exchange packet keys are already dumped.
4. And, finally, dissect mplex.