https://github.com/mvondracek/wifimitm
Wi-Fi Machine-in-the-Middle: Automation of MitM Attack on Wi-Fi Networks
https://github.com/mvondracek/wifimitm
accessing-secured-wireless-networks dictionary-personalization impersonation man-in-the-middle-attack password-cracking phishing tampering-network-topology wep wlan wpa wpa2
Last synced: 7 months ago
JSON representation
Wi-Fi Machine-in-the-Middle: Automation of MitM Attack on Wi-Fi Networks
- Host: GitHub
- URL: https://github.com/mvondracek/wifimitm
- Owner: mvondracek
- License: mit
- Created: 2017-04-23T20:00:36.000Z (about 8 years ago)
- Default Branch: dev
- Last Pushed: 2018-05-06T17:43:33.000Z (about 7 years ago)
- Last Synced: 2024-08-04T09:06:32.374Z (11 months ago)
- Topics: accessing-secured-wireless-networks, dictionary-personalization, impersonation, man-in-the-middle-attack, password-cracking, phishing, tampering-network-topology, wep, wlan, wpa, wpa2
- Language: Python
- Homepage: http://mvondracek.github.io/wifimitm/
- Size: 16.4 MB
- Stars: 52
- Watchers: 8
- Forks: 12
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-network-stuff - **28**星 - Fi Networks (<a id="42f9e068b6511bcbb47d6b2b273097da"></a>未分类 / <a id="3bd67ee9f322e2c85854991c85ed6da0"></a>投毒&&Poisoning)
README
## Wi-Fi Machine-in-the-Middle: Automation of MitM Attack on Wi-Fi Networks
[](https://www.archlinux.org/)
[](https://www.python.org/)
[](http://makeapullrequest.com)
* [Author](https://mvondracek.github.io/wifimitm/author/)
* [Videos](http://mvondracek.github.io/wifimitm/videos/)
* [Slides](http://mvondracek.github.io/wifimitm/slides/)
* [Manual](http://mvondracek.github.io/wifimitm/manual/)
* [Poster (cz)](http://mvondracek.github.io/wifimitm/assets/wifimitm-poster-cz.pdf)
* [Bachelor's thesis](http://www.fit.vutbr.cz/study/DP/BP.php.en?id=18596)
* [Software product in NES@FIT research group](http://www.fit.vutbr.cz/research/prod/index.php.en?id=487)
### Abstract
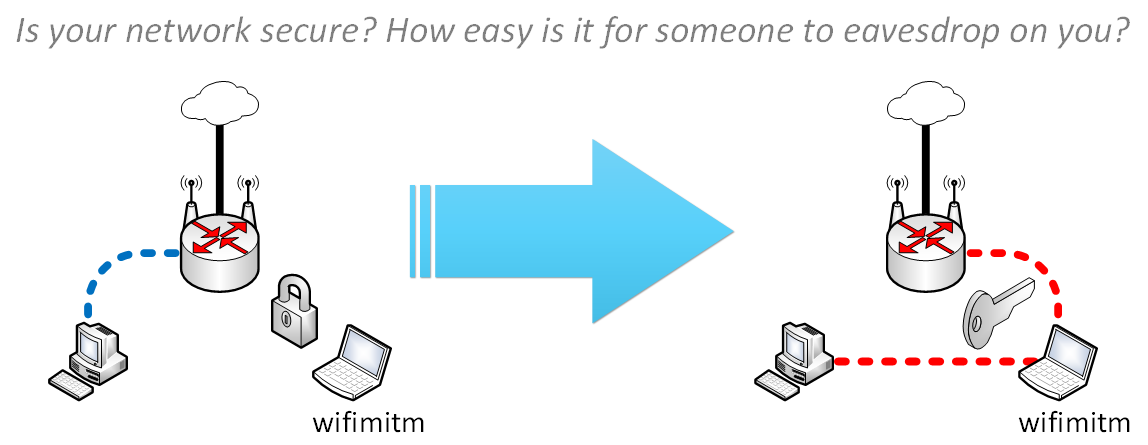
Widely used network technologies and principles of wireless security suffer weaknesses that can be exploited to perform the Man-in-the-Middle attack, allowing to eavesdrop or to spoof the network communication. The work focuses on possibilities of automation of the attack with a utilization of available specialized tools. The outcome of the research is the wifimitm package and the wifimitmcli CLI tool, both implemented in Python. The emphasis was placed on possibilities of further incorporation of the developed tool. The package provides functionality for automated MitM attack and can be used by other software. The wifimitmcli tool is capable of performing a successful fully automated attack without any intervention from an attacker.
This research can be used for automated penetration testing and forensic investigation. Finally, a popularization of the fact that such severe attacks can be successfully automated should be used to raise the public awareness about the information security. In these days, this issue involves almost every one of us.
