https://github.com/nextcloud/end_to_end_encryption
:closed_lock_with_key: Server API to support End-to-End Encryption
https://github.com/nextcloud/end_to_end_encryption
encryption end-to-end-encryption security
Last synced: 9 months ago
JSON representation
:closed_lock_with_key: Server API to support End-to-End Encryption
- Host: GitHub
- URL: https://github.com/nextcloud/end_to_end_encryption
- Owner: nextcloud
- License: agpl-3.0
- Created: 2017-09-27T10:54:14.000Z (over 8 years ago)
- Default Branch: master
- Last Pushed: 2025-05-11T04:23:45.000Z (9 months ago)
- Last Synced: 2025-05-12T23:40:23.669Z (9 months ago)
- Topics: encryption, end-to-end-encryption, security
- Language: JavaScript
- Homepage: https://apps.nextcloud.com/apps/end_to_end_encryption
- Size: 85 MB
- Stars: 291
- Watchers: 16
- Forks: 35
- Open Issues: 36
-
Metadata Files:
- Readme: README.md
- Changelog: CHANGELOG.md
- License: LICENSE
- Codeowners: .github/CODEOWNERS
- Security: SECURITY.md
- Authors: AUTHORS.md
Awesome Lists containing this project
- awesome-starred - nextcloud/end_to_end_encryption - :closed_lock_with_key: Server API to support End-to-End Encryption (security)
README
# End-to-End Encryption App
[](https://api.reuse.software/info/github.com/nextcloud/end_to_end_encryption)
This app provides all the necessary APIs to implement End-to-End encryption
on the client side. Additionally it makes sure that End-to-End encrypted
files are not accessible with the web interface and other WebDAV clients.
## Screenshots
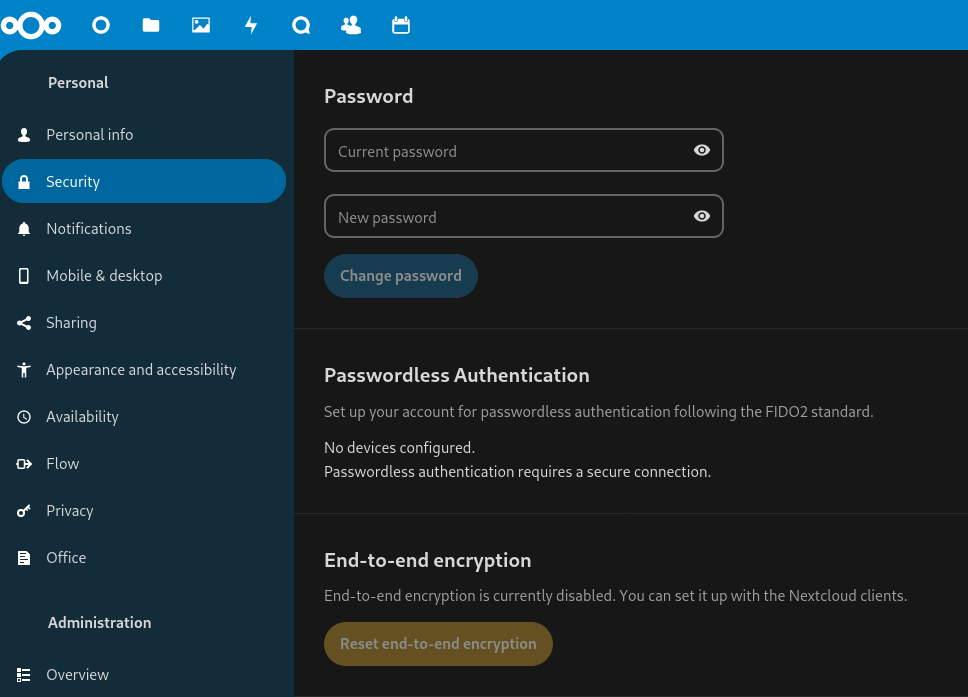
### Nextcloud Web
Found under *Personal settings -> Security*:
### Nextcloud Android App
When the E2EE server app has been successfully enabled and the client app awaits initial setup:

## Documentation
### Client API
Here you can find the [API documentation](https://github.com/nextcloud/end_to_end_encryption/blob/master/doc/api.md). Also some [typical client operations and how to use the API to perform them](https://github.com/nextcloud/end_to_end_encryption/blob/master/doc/api-usage.md) are documented too.
### Specification (RFC)
The end-to-end encryption implemented by the Nextcloud sync and mobile clients, as well as the functionality provided by this app to faciliate it, is based on the approach documented in the [RFC repository](https://github.com/nextcloud/end_to_end_encryption_rfc/).
### Installing
1. Make sure the Server-Side Encryption app is disabled (or uninstalled)
2. Install then enable the End-to-End Encryption app on your server. No configuration is required on the server other than this.
### Configuring
1. Trigger the "Setup end-to-end encryption" under settings within your favorite client app (all official clients support E2EE).
2. *Carefully* note your mnemonic (encryption passphrase) generated by your first client. The mnemonic is needed to: recover access to your data (i.e. if your device is lost or you need to reinstall the app) as well as to setup additional clients.
> [!CAUTION]
> The mnenomnic is *not* recoverable by a server administrator. If you lose your mnemonic you *will* lose access to your encrypted data.
### Using
#### Establishing a folder to encrypt
1. Within your favorite client app, create a dedicated folder - or folders - that you wish to have be encrypted.
2. Place the data (including other folders which will be encrypted)
#### Troubleshooting
##### General
- Since all encryption is handled by the clients, it is important that all client versions in-use be kept relatively aligned (in terms of release version/period) to maintain end-to-end compatibility.
- Since most operations are performed by the clients, in most cases potential bugs will need to be addressed in the clients (though sometimes in coordination with development occurring here with the server app).
- Be careful not to configure different mnemonics across your devices. They must all share the same mnemonic (created on the first device you provision E2EE on) or undefined behavior will occur.
- Keep in mind that using end-to-end encryption has trade-offs. Some functions will never be supported because they are inherently incompatible with the threat model of E2EE. In other cases, functionality may not yet be implemented in your favorite client (in this case you're encouraged to visit the Issues of your respective client and upvote the existing enhancement idea and/or submit your own where one does not already exist).
- E2EE files are inaccessible (by design) from the Nextcloud Web UI (client) in order to minimize needing to trust the server.
##### Data not being encrypted
- E2EE focuses on protecting your file-based data, but not other application data (e.g. calendars).
##### User agent configuraiton
The default user agent configuration is reasonable for all current official stable client releases, but sometimes needs to be adjusted when running custom or development client builds.
```php
// config/config.php
...,
// Allow to configure which client are supported (e.g. custom clients)
'end_to_end_encryption.supported-user-agents' => [
'/^Mozilla\/5\.0 \(Android\) Nextcloud\-android\/(?(0|[1-9]\d*)\.(0|[1-9]\d*)\.(0|[1-9]\d*)).*$/' => '3.13.0',
'/^Mozilla\/5\.0 \([A-Za-z ]+\) (mirall|csyncoC)\/(?(0|[1-9]\d*)\.(0|[1-9]\d*)\.(0|[1-9]\d*)).*$/' => '3.0.0',
'/^Mozilla\/5\.0 \(iOS\) Nextcloud\-iOS\/(?(0|[1-9]\d*)\.(0|[1-9]\d*)\.(0|[1-9]\d*)).*$/' => '3.0.5',
]
```
##### Recovery
There are various recovery scenarios where it may be useful to access (decrypt) your files independent of your Nextcloud installation. A separate set of tools called the [`encryption-recovery-tools`](https://github.com/nextcloud/encryption-recovery-tools) can be used for this.
## Additional Screenshots
### Nextcloud Web
*Personal -> Security*

### Nextcloud Web
*Admininistration settings -> Security*

### Nextcloud Desktop Client
