https://github.com/nim4/DBShield
Database firewall written in Go
https://github.com/nim4/DBShield
database db2 golang mariadb mysql oracle postgresql sql-injection
Last synced: 10 months ago
JSON representation
Database firewall written in Go
- Host: GitHub
- URL: https://github.com/nim4/DBShield
- Owner: nim4
- License: mit
- Created: 2016-09-20T12:26:30.000Z (over 9 years ago)
- Default Branch: master
- Last Pushed: 2017-09-24T20:01:16.000Z (over 8 years ago)
- Last Synced: 2025-04-05T06:06:31.798Z (11 months ago)
- Topics: database, db2, golang, mariadb, mysql, oracle, postgresql, sql-injection
- Language: Go
- Homepage: http://nim4.github.io/DBShield/
- Size: 4.55 MB
- Stars: 682
- Watchers: 53
- Forks: 163
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
- Contributing: CONTRIBUTING.md
- License: LICENSE
- Code of conduct: CODE_OF_CONDUCT.md
Awesome Lists containing this project
- awesome - DBShield - Database firewall written in Go (Go)
- awesome-rainmana - nim4/DBShield - Database firewall written in Go (Go)
README
[](https://travis-ci.org/nim4/DBShield)
[](https://ci.appveyor.com/project/nim4/DBShield/branch/master)
[](https://goreportcard.com/report/github.com/nim4/DBShield)
[](https://codecov.io/gh/nim4/DBShield)
[](https://gitter.im/DBShield/Lobby)
[](https://godoc.org/github.com/nim4/DBShield)
[](https://raw.githubusercontent.com/nim4/DBShield/master/LICENSE)
# DBShield
Protects your data by inspecting incoming queries from your application server and rejecting abnormal ones.
---
## How it works?
For example, this is how web server normally interacts with database server:
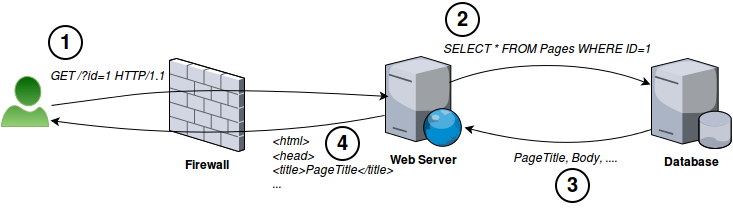
By adding DBShield in front of database server we can protect it against abnormal queries. To detect abnormal queries we first run DBShield in learning mode. Learning mode lets any query pass but it records information about it (pattern, username, time and source) into the internal database.
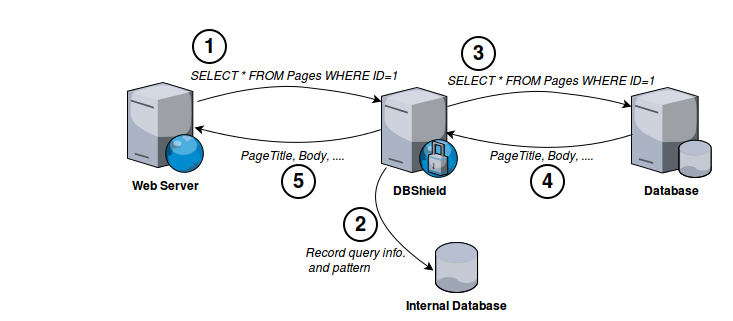
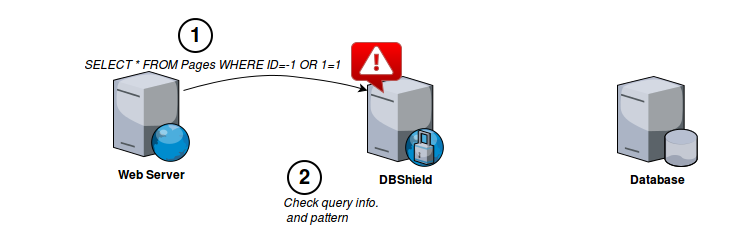
After collecting enough patterns we can run DBShield in protect mode. Protect mode can distinguish abnormal query pattern, user and source and take action based on configurations.
---
## Demo
For demo, we are using [sqlmap](https://github.com/sqlmapproject/sqlmap)(automatic SQL injection and database takeover tool) to exploit the SQL injection vulnerability at `user.php`
In the first scenario, the sqlmap successfully exploits the SQL injection when web application connected directly to the database(MySQL), In the second scenario, we modify the `user.php` so DBShield gets between the web application and database which will drop the injection attempt and make sqlmap fail.

---
## Sample Outputs
**CLI**
```
$ go run main.go
2016/10/15 16:25:31 [INFO] Config file: /etc/dbshield.yml
2016/10/15 16:25:31 [INFO] Internal DB: /tmp/model/10.0.0.21_postgres.db
2016/10/15 16:25:31 [INFO] Listening: 0.0.0.0:5000
2016/10/15 16:25:31 [INFO] Backend: postgres (10.0.0.21:5432)
2016/10/15 16:25:31 [INFO] Protect: true
2016/10/15 16:25:31 [INFO] Web interface on https://127.0.0.1:8070/
2016/10/15 16:25:33 [INFO] Connected from: 10.0.0.20:35910
2016/10/15 16:25:33 [INFO] Connected to: 10.0.0.21:5432
2016/10/15 16:25:33 [INFO] SSL connection
2016/10/15 16:25:34 [DEBUG] Client handshake done
2016/10/15 16:25:34 [DEBUG] Server handshake done
2016/10/15 16:25:34 [INFO] User: postgres
2016/10/15 16:25:34 [INFO] Database: test
2016/10/15 16:25:34 [INFO] Query: SELECT * FROM stocks where id=-1 or 1=1
2016/10/15 16:25:34 [WARN] Pattern not found: [53 55 51 52 55 52 50 53 55 51 53 49 115 116 111 99 107 115 53 55 51 53 50 105 100 54 49 52 53 53 55 51 55 57 53 55 52 48 52 53 55 51 55 57 54 49 53 55 51 55 57] (SELECT * FROM stocks where id=-1 or 1=1)
2016/10/15 16:25:34 [WARN] Dropping connection
```
**Web Interface**
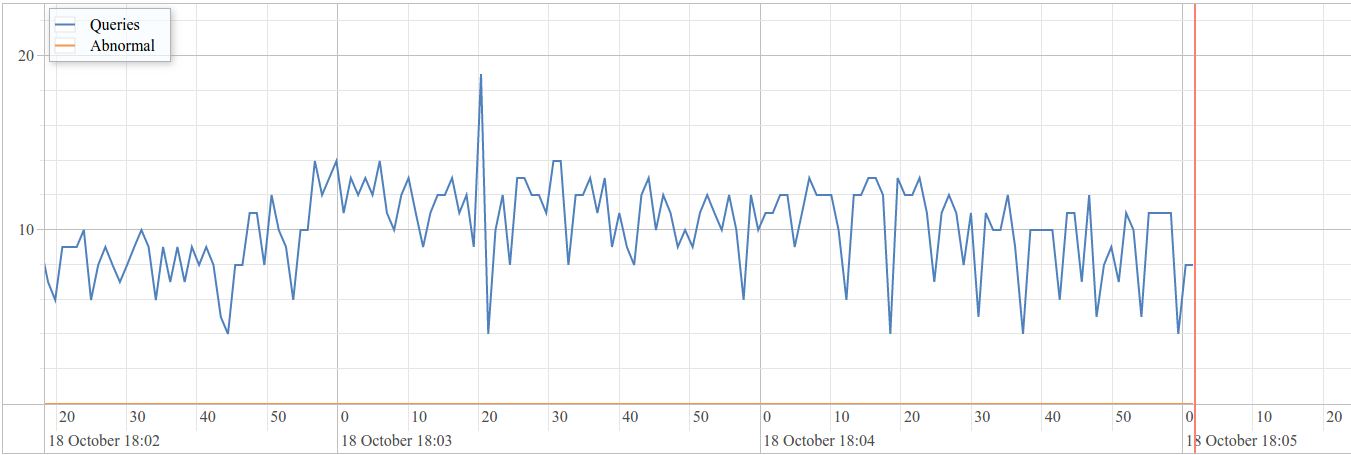
---
## Installation
Get it
```
$ go get -u github.com/nim4/DBShield
```
Then you can see help using "-h" argument:
```
$ $GOPATH/bin/DBShield -h
DBShield 1.0.0-beta3
Usage of DBShield:
-a get list of abnormal queries
-c file
config file (default "/etc/dbshield.yml")
-h show help
-k show parsed config and exit
-l get list of captured patterns
-version
show version
```
and run it with your configuration, like:
```
$ $GOPATH/bin/DBShield -c config.yml
```
see [sample configuration file](https://github.com/nim4/DBShield/blob/master/conf/dbshield.yml)
>:warning: **WARNING:**
> Do NOT use default certificates in production environments!
---
## Supports:
| Database | Protect | SSL |
|:------------:|:-------:|:---:|
| **DB2** | ![Yes][YesImg] | ![No][NoImg] |
| **MariaDB** | ![Yes][YesImg] | ![Yes][YesImg] |
| **MySQL** | ![Yes][YesImg] | ![Yes][YesImg] |
| **Oracle** | ![Yes][YesImg] | ![No][NoImg] |
| **Postgres** | ![Yes][YesImg] | ![Yes][YesImg] |
---
## To Do
(Sorted by priority)
- Improve documentation
- Add Microsoft SQL Server
- Add more command-line arguments
- Get 90% test coverage
- Support Oracle SSL
[YesImg]: https://raw.githubusercontent.com/nim4/DBShield/master/misc/yes.png
[NoImg]: https://raw.githubusercontent.com/nim4/DBShield/master/misc/no.png