https://github.com/philippanda/securos
SecurOS is a secure Arch based Linux distribution that comes pre-installed with the most popular pen-test and cyber-security tools.
https://github.com/philippanda/securos
arch-linux archlinux cyber-security cybersecurity linux linux-distribution operating-system os pentesting
Last synced: 5 months ago
JSON representation
SecurOS is a secure Arch based Linux distribution that comes pre-installed with the most popular pen-test and cyber-security tools.
- Host: GitHub
- URL: https://github.com/philippanda/securos
- Owner: PhilipPanda
- License: mit
- Created: 2023-10-07T18:15:48.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2024-04-08T09:05:27.000Z (almost 2 years ago)
- Last Synced: 2025-03-12T06:14:47.275Z (11 months ago)
- Topics: arch-linux, archlinux, cyber-security, cybersecurity, linux, linux-distribution, operating-system, os, pentesting
- Language: CSS
- Homepage: https://securos.org
- Size: 24.3 MB
- Stars: 3
- Watchers: 2
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
SecurOS Secure Arch Linux Operating System

Website | Company | Install
-----
**
Keep in mind this Operating System is currently in development.
**
For Virtual Machines
- You need Virtual Box / VMWare / Qemu.
- Download the ISO,
- Create a new Arch 64-bit VM.
- Recommended 16 core processor & 8 gb of ram
For Flashing On PC
- You need a usb stick "preferably 4gb".
- Download the ISO File.
- Flash the ISO File using Belena Etcher / Rufus on your usb stick.
- Recommended 16 core processor & 6 gb of ram
-----
Default User Information
- Default username: securos
- Default password: securos
-----
Info
SecurOS is an advanced operating system built upon the Arch platform, specifically designed and optimized for the fields of penetration testing (pentesting) and cybersecurity. This specialized operating system is tailored to meet the unique needs and demands of security professionals and ethical hackers who are tasked with identifying vulnerabilities, assessing the robustness of systems, and ensuring the protection of sensitive data.
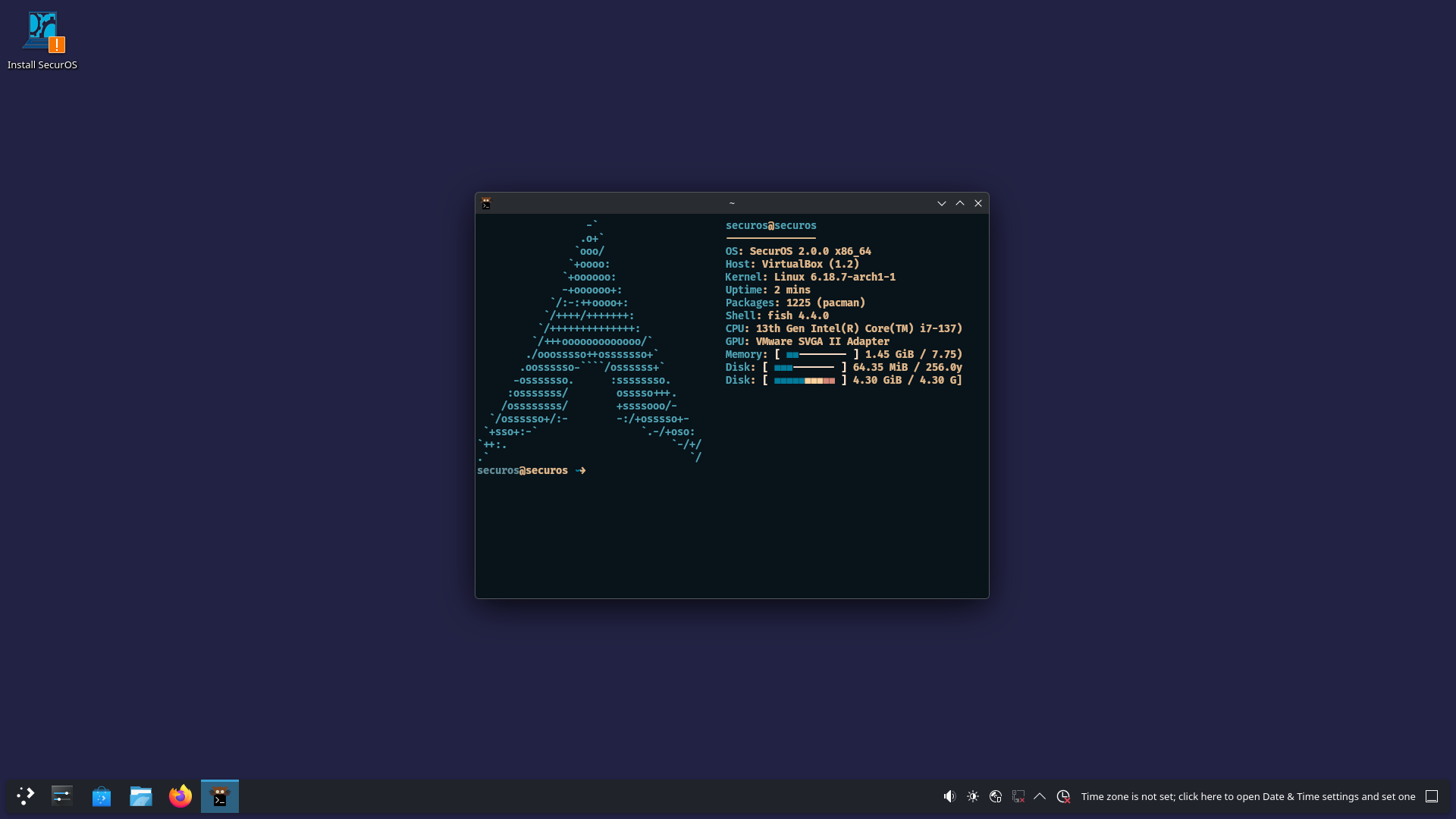
Showcase
Expand to see images.