https://github.com/processust/unhookingdll
This script is used to bypass DLL Hooking using a fresh mapped copy of ntdll file, patch the ETW and trigger a shellcode with process hollowing
https://github.com/processust/unhookingdll
bypass dll-unhooking edr etw process-hollowing shellcode
Last synced: 3 months ago
JSON representation
This script is used to bypass DLL Hooking using a fresh mapped copy of ntdll file, patch the ETW and trigger a shellcode with process hollowing
- Host: GitHub
- URL: https://github.com/processust/unhookingdll
- Owner: ProcessusT
- Created: 2023-02-20T21:55:19.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-02-11T18:12:34.000Z (almost 2 years ago)
- Last Synced: 2025-03-28T19:07:25.278Z (10 months ago)
- Topics: bypass, dll-unhooking, edr, etw, process-hollowing, shellcode
- Language: C++
- Homepage:
- Size: 44.9 KB
- Stars: 68
- Watchers: 4
- Forks: 12
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
C++ template for DLL Unhooking + ETW patching
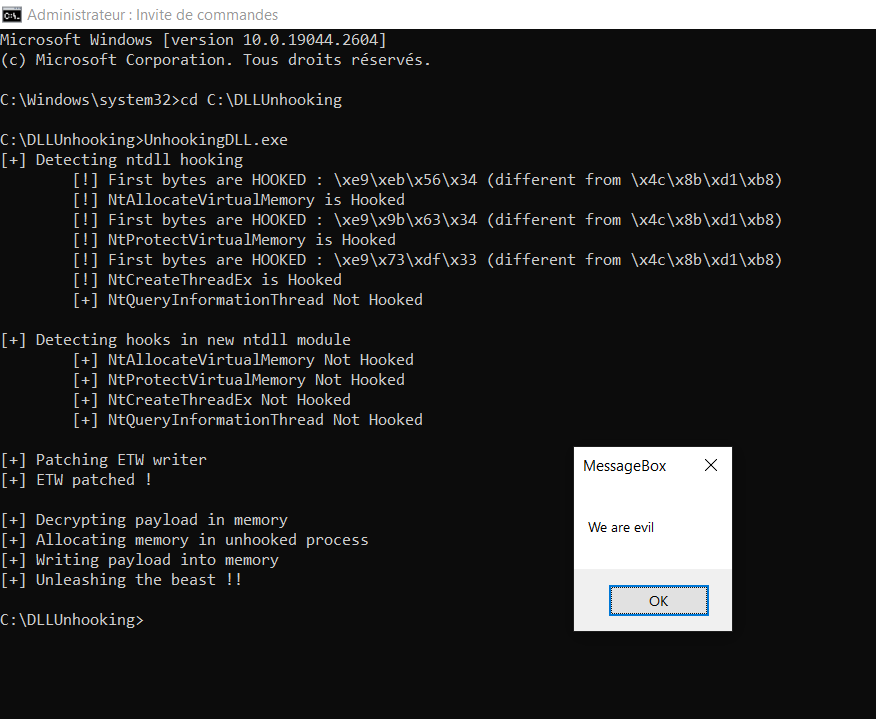
This script is used to bypass DLL Hooking using a fresh mapped copy of ntdll file, patch the ETW and trigger a shellcode with process hollowing
Stolen from :
- https://github.com/TheD1rkMtr
- https://www.ired.team/offensive-security/defense-evasion/how-to-unhook-a-dll-using-c++
- https://github.com/Hagrid29/RemotePatcher/blob/main/RemotePatcher/RemotePatcher.cpp