https://github.com/pwnosec/minimalisticwaf
A Lightweight and Minimalist Web Application Firewall Designed for Node.js Servers.
https://github.com/pwnosec/minimalisticwaf
Last synced: 3 months ago
JSON representation
A Lightweight and Minimalist Web Application Firewall Designed for Node.js Servers.
- Host: GitHub
- URL: https://github.com/pwnosec/minimalisticwaf
- Owner: pwnosec
- License: mit
- Created: 2024-11-23T07:51:58.000Z (8 months ago)
- Default Branch: main
- Last Pushed: 2024-11-23T08:26:22.000Z (8 months ago)
- Last Synced: 2025-02-10T01:29:42.876Z (5 months ago)
- Language: JavaScript
- Size: 3.88 MB
- Stars: 0
- Watchers: 0
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
## Getting started into Mini-WAF!
A Minimalistic Web Application Firewall for your purposes in NodeJS servers. It will protect your servers against XSS, XSRF, DOS, LFI, SQL Injection, Unauthorized Remote Access, Unhandled Exceptions and Botnets attacks. Mini-WAF is a Minimalistic Web Application Firewall that avoid and block several attacks in HTTP and HTTPS protocols with a great support to IPv4 and IPv6.
## First use of Mini-WAF with Express
After install Mini-WAF and it's dependencies you need load our middleware with an initialized object that contains all rules, callbacks and properties necessary to protect your application. By default, you can load our own waf config in wafrules module.
```javascript
const express = require("express");
const app = express();
const Waf = require('mini-waf/wafbase');
const wafrules = require('mini-waf/wafrules');
//Register the middleware of Mini-WAF with standard rules.
app.use(Waf.WafMiddleware(wafrules.DefaultSettings));
//Create your routes in your way!
app.use((req, res) => {
//Do your work in anywhere.
res.send('Some data...');
res.end();
});
app.listen(55100, function () {
console.log("Running server on port 55100!");
});
```
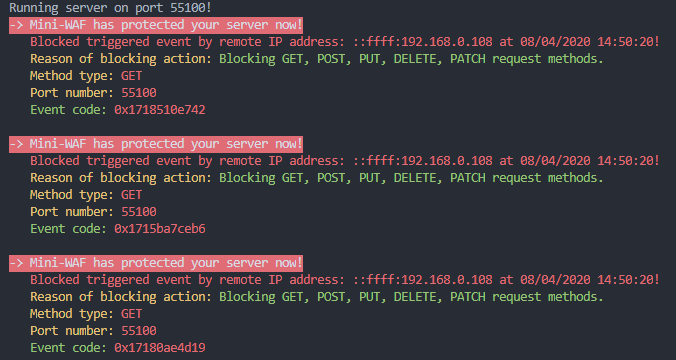
## Mini-WAF blocking Denial of Service attacks
With custom rules we can block specified methods for specific IPs or User-Agents, and also for specific routes just creating a simple DACL object and adding it to our rule.
```javascript
Dacls: [
{
NetworkLayers: Waf.WAF_NETWORK_LAYER.PROTOCOL_IPV4,
MatchTypes: Waf.WAF_MATCH_TYPE.MATCH_METHOD_TYPE,
ManageType: Waf.WAF_MANAGE_TYPE.BLOCK,
Directions: Waf.WAF_RULE_DIRECTION.INBOUND,
MethodTypes: "GET|POST|PUT|DELETE|PATCH",
Description: 'Blocking GET, POST, PUT, DELETE, PATCH request methods.'
}
]
```
Also, block unauthorized access is very easy.
```javascript
Dacls: [
{
NetworkLayers: Waf.WAF_NETWORK_LAYER.PROTOCOL_IPV4,
MatchTypes: Waf.WAF_MATCH_TYPE.MATCH_IP,
ManageType: Waf.WAF_MANAGE_TYPE.BLOCK,
Directions: Waf.WAF_RULE_DIRECTION.INBOUND,
Ipv4Address: '206.189.180.4',
Description: 'Blocking a specific IP address.'
}
]
```
## Log of attacks