https://github.com/qeeqbox/authorization-bypass
A threat actor may access the user's account using a stolen or leaked valid (existing) session identifier
https://github.com/qeeqbox/authorization-bypass
authorization bypass example infosecsimplified metadata qeeqbox vulnerability
Last synced: 11 months ago
JSON representation
A threat actor may access the user's account using a stolen or leaked valid (existing) session identifier
- Host: GitHub
- URL: https://github.com/qeeqbox/authorization-bypass
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-26T04:25:40.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:08:03.000Z (almost 2 years ago)
- Last Synced: 2025-01-16T05:55:52.250Z (about 1 year ago)
- Topics: authorization, bypass, example, infosecsimplified, metadata, qeeqbox, vulnerability
- Homepage:
- Size: 132 KB
- Stars: 2
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
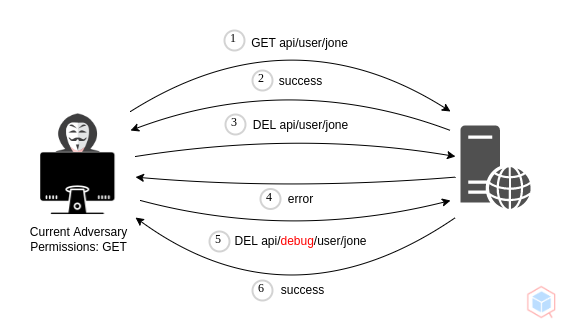
A threat actor may perform unauthorized functions by bypassing or abusing the target authorization mechanism
## Example #1
1. Developer forgets to remove an in-house debugging mechanism associated with user-agent
2. A threat actor finds out changing the user-agent header to debug grants different or higher privileges
## Impact
Vary
## Risk
- read & modify data
- execute commands
## Redemption
- validate access control
## ID
91f9b046-b802-425a-b71b-64c21c6b1c0f
## References
- [mitre](https://cwe.mitre.org/data/definitions/639.html