https://github.com/qeeqbox/captcha-bypass
A threat actor may bypass the Completely Automated Public Turing test to tell Computers and Humans Apart (captcha) by breaking the solving logic, human-assisted solving services, or utilizing automated technology
https://github.com/qeeqbox/captcha-bypass
bypass captcha example infosecsimplified metadata qeeqbox visulization vulnerability
Last synced: 8 days ago
JSON representation
A threat actor may bypass the Completely Automated Public Turing test to tell Computers and Humans Apart (captcha) by breaking the solving logic, human-assisted solving services, or utilizing automated technology
- Host: GitHub
- URL: https://github.com/qeeqbox/captcha-bypass
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-20T20:37:25.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:04:06.000Z (about 2 years ago)
- Last Synced: 2025-05-26T21:42:22.479Z (8 months ago)
- Topics: bypass, captcha, example, infosecsimplified, metadata, qeeqbox, visulization, vulnerability
- Homepage:
- Size: 210 KB
- Stars: 2
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
A threat actor may bypass the Completely Automated Public Turing test to tell Computers and Humans Apart (captcha) by breaking the solving logic, human-assisted solving services, or utilizing automated technology.
## Example #1
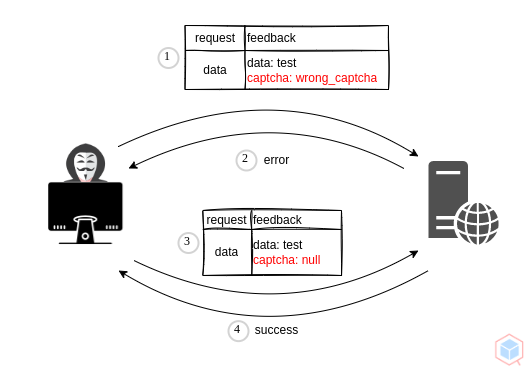
1. Threat actor fills up a feedback form with the wrong captcha
2. Server sends a request to answer the captcha correctly
3. Threat actor fills up a feedback form with null
4. Sever does not handle null properly and continues to process the request
## Impact
Vary
## Risk
- Perform unauthorized action
## Redemption
- Different captcha
- Device fingerprinting
## ID
d9d7a4e5-dfa6-4d7a-a5c2-65799113437d
## References
- [perimeterx](https://www.perimeterx.com/resources/blog/2020/captchas-hard-for-humans-easy-for-bots/")