https://github.com/qeeqbox/client-side-template-injection
A threat actor may trick a victim into executing native template syntax on a vulnerable target
https://github.com/qeeqbox/client-side-template-injection
client infosecsimplified injection qeeqbox side template vulnerability
Last synced: 8 months ago
JSON representation
A threat actor may trick a victim into executing native template syntax on a vulnerable target
- Host: GitHub
- URL: https://github.com/qeeqbox/client-side-template-injection
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-12-25T20:03:25.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:03:28.000Z (almost 2 years ago)
- Last Synced: 2025-01-16T05:55:52.536Z (10 months ago)
- Topics: client, infosecsimplified, injection, qeeqbox, side, template, vulnerability
- Homepage:
- Size: 129 KB
- Stars: 3
- Watchers: 2
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
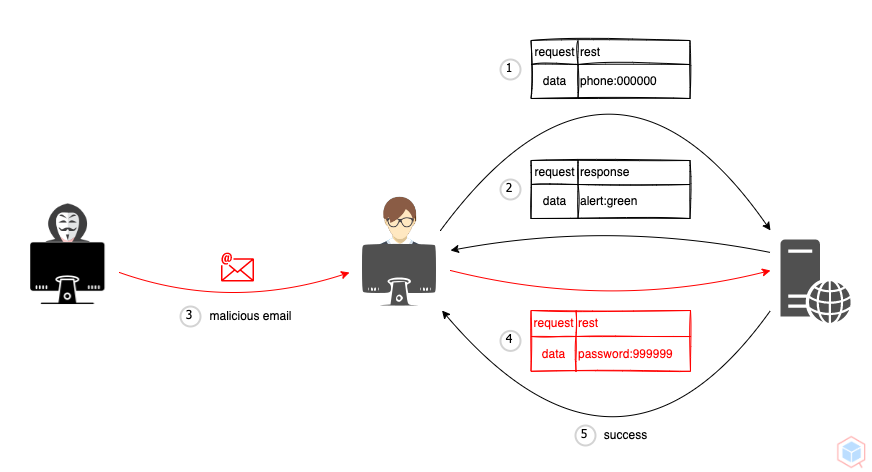
A threat actor may trick a victim into executing native template syntax on a vulnerable target (This is similar SSTI but happens on the client side)
## Example #1
1. Threat actor crafts an exploit URL
2. Bob logs in to the vulnerable website
3. Threat actor tricks Bob into clicking on the exploit URL
4. Bob clicks on the exploit URL, and the browser executes the exploit
## Code
#### Target-Logic
```html
var url = new URL(window.location);
var alert = url.searchParams.get("alert");
document.getElementById('alert').innerHTML = alert
document.body.style.backgroundColor = alert
```
#### Target-In
```
/?alert=
```
#### Target-Output
```
alert box: test
```
## Impact
Vary
## Risk
- Command execution
## Redemption
- Input validation
- Logic-less
## Names
- Client Side Template Injection
- SST injection
## ID
477ac741-89fe-4d0b-b094-09d720ed9d83
## References
- [tenable](https://www.tenable.com/plugins/was/112684)