https://github.com/qeeqbox/credential-stuffing
A threat actor may guess the target credentials using a known username and password pairs gathered from previous brute-force attacks
https://github.com/qeeqbox/credential-stuffing
credentials example infosecsimplified metadta qeeqbox stuffing visualization vulnerability
Last synced: 11 months ago
JSON representation
A threat actor may guess the target credentials using a known username and password pairs gathered from previous brute-force attacks
- Host: GitHub
- URL: https://github.com/qeeqbox/credential-stuffing
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-20T20:12:19.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:06:15.000Z (about 2 years ago)
- Last Synced: 2025-01-16T05:55:52.517Z (about 1 year ago)
- Topics: credentials, example, infosecsimplified, metadta, qeeqbox, stuffing, visualization, vulnerability
- Homepage:
- Size: 375 KB
- Stars: 2
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
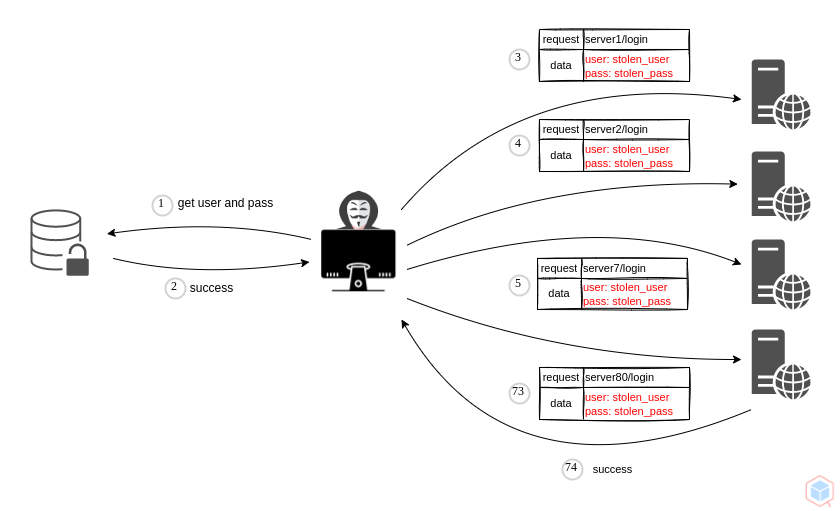
A threat actor may guess the target credentials using a known username and password pairs gathered from previous brute-force attacks.
## Example #1
1. Threat actor has a stolen username and password pair for a vulnerable
2. Threat actor uses the same pair for other websites
## Impact
Vary
## Risk
- Gain unauthorized access
## Redemption
- Increase the password length
- Increase password complexity
- Limit login attempts
- Implement captcha
- Multi-factor authentication
## ID
8456e95b-dae6-44ff-bb2b-75a37e16c0c7
## References
- [wiki](https://en.wikipedia.org/wiki/brute-force_attack/)