https://github.com/qeeqbox/cross-site-request-forgery
A threat actor may trick an authenticated or trusted victim into executing unauthorized actions on their behalf
https://github.com/qeeqbox/cross-site-request-forgery
cross example forgery infosecsimplified metadata qeeqebox request site vulnerability
Last synced: 9 months ago
JSON representation
A threat actor may trick an authenticated or trusted victim into executing unauthorized actions on their behalf
- Host: GitHub
- URL: https://github.com/qeeqbox/cross-site-request-forgery
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-21T03:23:23.000Z (over 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:55:57.000Z (almost 2 years ago)
- Last Synced: 2025-01-16T05:55:52.471Z (11 months ago)
- Topics: cross, example, forgery, infosecsimplified, metadata, qeeqebox, request, site, vulnerability
- Homepage:
- Size: 237 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
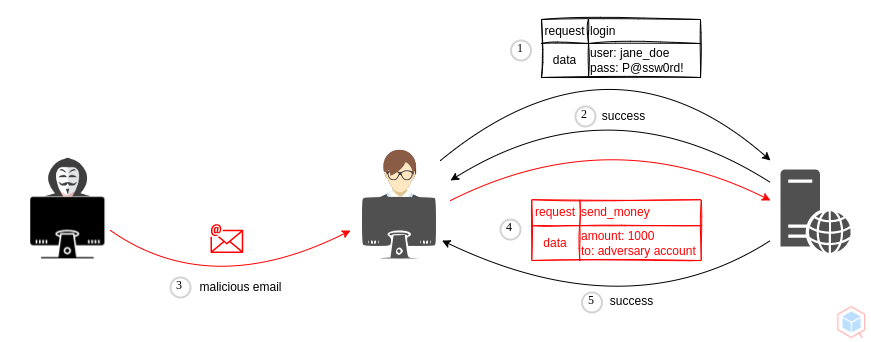
A threat actor may trick an authenticated or trusted victim into executing unauthorized actions on their behalf.
## Example #1
1. Threat actor crafts an exploit URL for a fund transfer from a vulnerable website
2. Bob logs in to the vulnerable website (Bob is authenticated - session cookie is saved)
3. Threat actor tricks Bob into clicking on the exploit URL
4. Bob clicks on the exploit URL
5. Bob's browser loads the session cookie and performs a fund transfer
## Code
#### Target-Logic
```py
@app.route("/send_money", methods=["POST"])
@login_required
def send_money():
...
amount = int(request.form.get("amount"))
to_user = get_user(int(reques.form.get("to_user")))
if current_user:
if current_user['balance'] <= amount:
current_user['balance'] -= amount
to_user['balance'] += amount
return make_response({"transfer":"success"}, 200)
return make_response({"transfer":"failed"}, 200)
```
#### Victim-Executes
```html
document.forms[0].submit();
```
#### Target-In
```
amount=1000
to_user=ABC-999
```
#### Target-Output
```json
{"transfer":"success"}
```
## Impact
Vary
## Risk
- Read & modify data
- Execute commands
## Redemption
- Header verification
- Challenge-response
- Anti-csrf tokens
- Same-site cookies
## Names
- XSRF
- Sea Surf
- Session Riding
- Cross-Site reference forgery
- Hostile linking
## ID
776dd60c-c1de-46a3-a104-25cd836e24b6
## References
- [wiki](https://en.wikipedia.org/wiki/cross-site_request_forgery)