Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/qeeqbox/dom-based-cross-site-scripting
A threat actor may inject malicious content into HTTP requests. The content is not reflected in the HTTP response and executed in the victim's browser.
https://github.com/qeeqbox/dom-based-cross-site-scripting
cross dom example infosecsimplified metadata qeeqbox scripting site vulnerability xss xss-vulnerability
Last synced: 25 days ago
JSON representation
A threat actor may inject malicious content into HTTP requests. The content is not reflected in the HTTP response and executed in the victim's browser.
- Host: GitHub
- URL: https://github.com/qeeqbox/dom-based-cross-site-scripting
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-28T18:44:36.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:59:33.000Z (about 1 year ago)
- Last Synced: 2024-11-15T17:42:26.217Z (3 months ago)
- Topics: cross, dom, example, infosecsimplified, metadata, qeeqbox, scripting, site, vulnerability, xss, xss-vulnerability
- Homepage:
- Size: 220 KB
- Stars: 3
- Watchers: 1
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
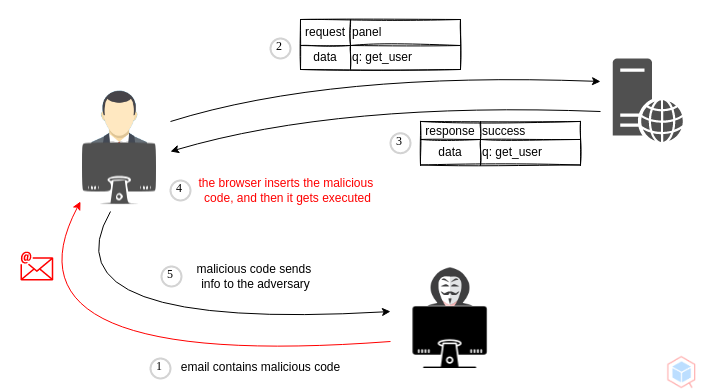
A threat actor may inject malicious content into HTTP requests. The content is not reflected in the HTTP response and executed in the victim's browser.
## Example #1
1. Threat actor crafts an email with a malicious request to a vulnerable target and sends the email to a victim
2. The victim clicks on the email and sends the request to the vulnerable target
3. The target sends the malicious code back to the victim
4. The victim's browser inserts the malicious code
5. When malicious code gets executed, it calls back the threat actor
## Impact
Vary
## Risk
- Read & modify data
## Redemption
- Client input validation
- Output encoding
- Browser built-in XSS preveiton
## ID
cb251c97-067d-4f13-8195-4f918273f41b
## References
- [wiki](https://en.wikipedia.org/wiki/cross-site_scripting)