https://github.com/qeeqbox/local-file-inclusion
A threat actor may cause a vulnerable target to include/retrieve local file
https://github.com/qeeqbox/local-file-inclusion
file include infosecsimplified local qeeqbox vulnerability
Last synced: 3 months ago
JSON representation
A threat actor may cause a vulnerable target to include/retrieve local file
- Host: GitHub
- URL: https://github.com/qeeqbox/local-file-inclusion
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2023-06-23T05:25:50.000Z (almost 2 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:56:17.000Z (over 1 year ago)
- Last Synced: 2025-01-16T05:55:51.391Z (4 months ago)
- Topics: file, include, infosecsimplified, local, qeeqbox, vulnerability
- Homepage:
- Size: 110 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
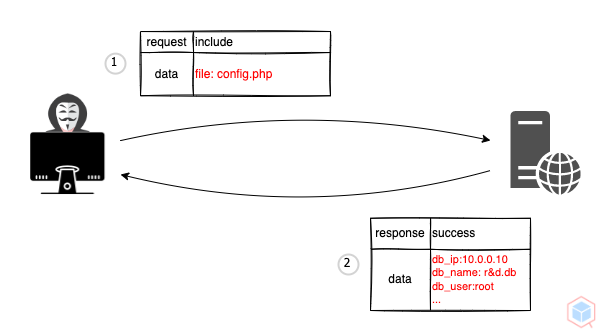
A threat actor may cause a vulnerable target to include/retrieve local file
## Example #1
1. A threat actor sends a malicious request that includes the local file name to a vulnerable target
2. The vulnerable target includes the malicious local file as PHP and outputs it
## Code
#### Target-Logic
```php
#allow_url_include = On
```
#### Target-In
```
http://vulnerable.test/index.php?file=config.php
```
#### Target-Out
```
db_ip:10.0.0.10
db_name:r&d.db
db_user:root
```
## Impact
High
## Names
- Local file inclusion
- LFI
## Risk
- Read data
## Redemption
- Input validation
- Whitelist
## ID
2690f163-038a-4bc5-9ff3-3a02ba5f84ee
## References
- [Wikipedia](https://en.wikipedia.org/wiki/file_inclusion_vulnerability)