https://github.com/qeeqbox/server-side-template-injection
A threat actor may alter the template syntax on the vulnerable target to execute commands
https://github.com/qeeqbox/server-side-template-injection
infosecsimplified injection qeeqbox server side template vulnerability
Last synced: 10 months ago
JSON representation
A threat actor may alter the template syntax on the vulnerable target to execute commands
- Host: GitHub
- URL: https://github.com/qeeqbox/server-side-template-injection
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-12-25T06:02:05.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:58:04.000Z (almost 2 years ago)
- Last Synced: 2025-01-16T05:55:51.029Z (11 months ago)
- Topics: infosecsimplified, injection, qeeqbox, server, side, template, vulnerability
- Homepage:
- Size: 78.1 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
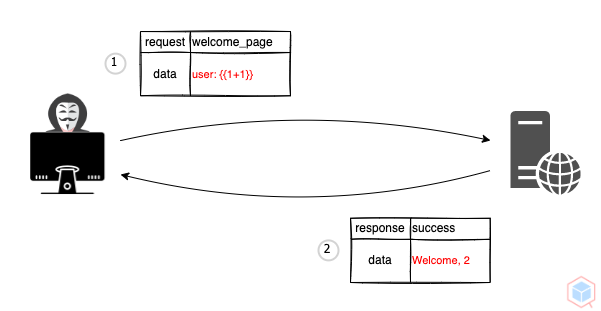
A threat actor may use a native template syntax on the vulnerable target to execute commands
## Example #1
1. Threat actor sends a native template syntax to a vulnerable target that uses a template engine
2. The target process the syntax and executes the result
## Code
#### Target-Logic
```py
@app.route('/welcome', methods=['GET'])
def welcome():
user = request.args.get('user')
template = f"
Welcome, {user}!
"
return render_template_string(template)
```
#### Target-In
```
{{1+1}}
```
#### Target-Out
```
Welcome, 4
```
## Impact
High
## Names
- Server Side Template Injection
- SST injection
## Risk
- Command execution
## Redemption
- Input validation
- Logic-less
## ID
E0679353-0BB6-404B-A6CC-6F6305FF118C
## References
- [owasp](https://owasp.org/www-project-web-security-testing-guide/v41/4-Web_Application_Security_Testing/07-Input_Validation_Testing/18-Testing_for_Server_Side_Template_Injection)