https://github.com/qeeqbox/session-replay
A threat actor may re-use a stolen or leaked session identifier to access the user's account
https://github.com/qeeqbox/session-replay
example infosecsimplified metadata qeeqbox replay session visualization vulnerability
Last synced: 11 months ago
JSON representation
A threat actor may re-use a stolen or leaked session identifier to access the user's account
- Host: GitHub
- URL: https://github.com/qeeqbox/session-replay
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-21T19:39:53.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:59:54.000Z (about 2 years ago)
- Last Synced: 2025-01-16T05:55:51.007Z (about 1 year ago)
- Topics: example, infosecsimplified, metadata, qeeqbox, replay, session, visualization, vulnerability
- Homepage:
- Size: 257 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
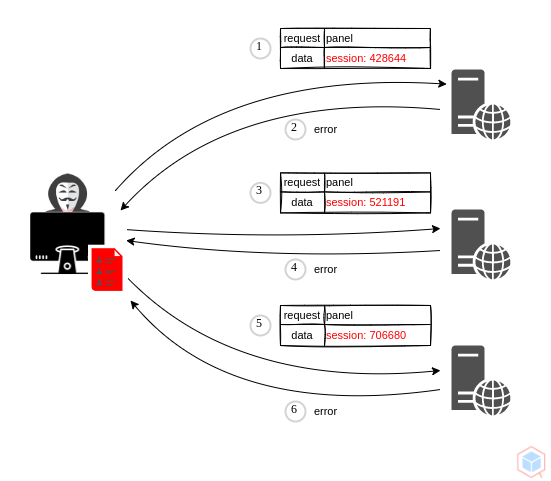
A threat actor may re-use a stolen or leaked session identifier to access the user's account.
## Example #1
1. Threat actor obtains a valid session identifier and does not use it immediately
2. Threat actor re-using the same session identifier to gain unauthorized access to a victim's account
## Example #2
1. Bob submits a request to buy an item from a vulnerable website
2. Threat actor finds the request and tricks bob into re-submitting it
3. The vulnerable website receives both requests with the same session identifier and processes them
## Impact
Vary
## Risk
- gain unauthorized access
## Redemption
- Identity confirmation
- Regenerate session ids at authentication
- Timeout and replace old session ids
- Store ids in HTTP cookies
## ID
fe0561ad-6ce7-4cf3-a229-eb136ad1f919
## References
- [wiki](https://en.wikipedia.org/wiki/session_fixation)