https://github.com/qeeqbox/sql-injection
A threat actor may alter structured query language (SQL) query to read, modify and write to the database or execute administrative commands for further chained attacks
https://github.com/qeeqbox/sql-injection
infosecsimplified metadata qeeqbox sql-injection visualization vulnerability
Last synced: 4 months ago
JSON representation
A threat actor may alter structured query language (SQL) query to read, modify and write to the database or execute administrative commands for further chained attacks
- Host: GitHub
- URL: https://github.com/qeeqbox/sql-injection
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-12-24T05:27:42.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:58:25.000Z (over 1 year ago)
- Last Synced: 2025-01-16T05:55:51.025Z (6 months ago)
- Topics: infosecsimplified, metadata, qeeqbox, sql-injection, visualization, vulnerability
- Homepage:
- Size: 131 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
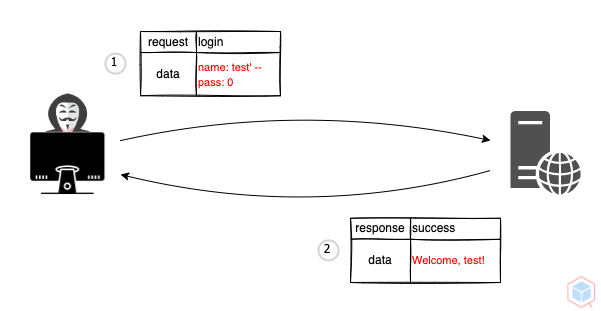
A threat actor may alter structured query language (SQL) query to read, modify and write to the database or execute administrative commands for further chained attacks (The threat actor may get output or verbose errors while performing the injection)
## Example #1
1. Threat actor sends a malicious SQL query to a vulnerable target
2. The target process the query and return the result
## Code
#### Target-Logic
```js
app.post("/query", (request, response) => {
const query = "SELECT * FROM users WHERE username = '"+ request.body.username +"' AND password = '"+ request.body.password +"'"
connection.query(query, (error, result) => {
response.json({"result":result,"err":error});
});
});
```
#### Target-In
```
test';--
```
#### Target-Out
```
Welcome, test!
```
## Impact
High
## Names
- SQL injection
## Risk
- Read & write data
- Command execution
## Redemption
- Input validation
- Parametrized queries
- Stored procedures
## ID
85b0dbbc-1d39-4d96-9816-319276d2c0e2
## References
- [wiki](https://en.wikipedia.org/wiki/sql_injection)