Ecosyste.ms: Awesome
An open API service indexing awesome lists of open source software.
https://github.com/qeeqbox/stored-cross-site-scripting
An adversary may inject malicious content into a vulnerable target
https://github.com/qeeqbox/stored-cross-site-scripting
cross example infosecsimplified metadata qeeqbox scripting site stored visulization vulnerability xss-vulnerability
Last synced: 2 days ago
JSON representation
An adversary may inject malicious content into a vulnerable target
- Host: GitHub
- URL: https://github.com/qeeqbox/stored-cross-site-scripting
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-28T19:25:42.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:01:03.000Z (10 months ago)
- Last Synced: 2024-05-01T11:27:25.150Z (7 months ago)
- Topics: cross, example, infosecsimplified, metadata, qeeqbox, scripting, site, stored, visulization, vulnerability, xss-vulnerability
- Homepage:
- Size: 125 KB
- Stars: 4
- Watchers: 1
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
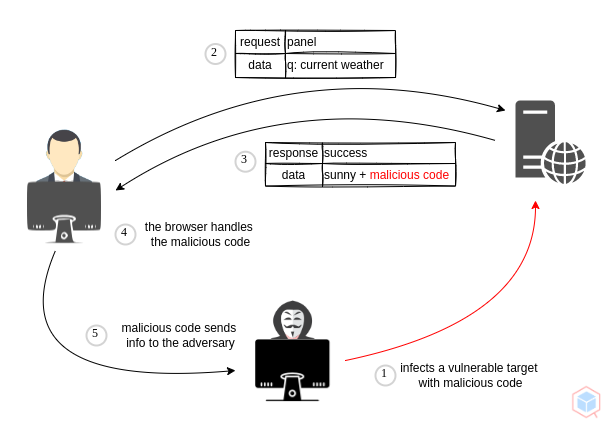
A threat actor may inject malicious content where content is saved into a database, when users visit the malicious vulnerable website, the malicious content is loaded from the database and the browser executes that.
## Example #1
1. Threat actor infects a vulnerable target with malicious code to a victim
2. The victim requests the vulnerable target and receives the malicious code
3. When malicious code gets executed, it calls back the threat actor
## Impact
Vary
## Risk
- Read & modify data
## Redemption
- Output encoding
- Browser built-in XSS preveiton
## ID
cb251c97-067d-4f13-8195-4f918273f41b
## References
- [wiki](https://en.wikipedia.org/wiki/cross-site_scripting)