https://github.com/qeeqbox/two-factor-authentication-brute-force
A threat actor may lunch brute force to the two-factor authentication (2FA) logic causing unauthorized access to the target
https://github.com/qeeqbox/two-factor-authentication-brute-force
2fa authentication brute-force example infosecsimplified qeeqbox visualization vulnerability
Last synced: 8 days ago
JSON representation
A threat actor may lunch brute force to the two-factor authentication (2FA) logic causing unauthorized access to the target
- Host: GitHub
- URL: https://github.com/qeeqbox/two-factor-authentication-brute-force
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-04-19T17:23:29.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:04:37.000Z (about 2 years ago)
- Last Synced: 2025-06-04T12:16:09.057Z (8 months ago)
- Topics: 2fa, authentication, brute-force, example, infosecsimplified, qeeqbox, visualization, vulnerability
- Homepage:
- Size: 112 KB
- Stars: 3
- Watchers: 1
- Forks: 1
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
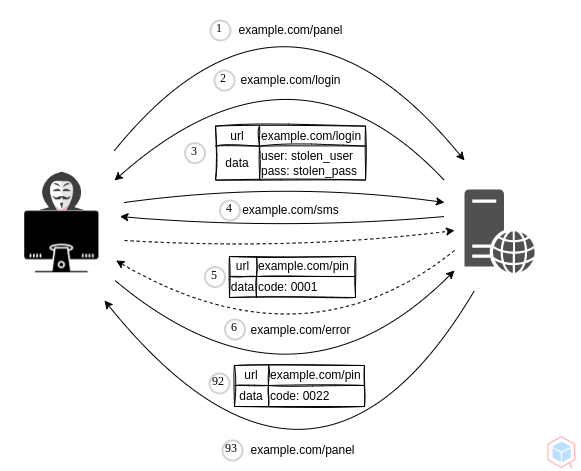
A threat actor may lunch brute force to the two-factor authentication (2FA) logic causing unauthorized access to the target.
## Example #1
1. Threat actor has a stolen username and password pair for a vulnerable website
2. Threat actor logs in and prompted with a four digits pin code that was sent to the victims mobile
3. Threat actor lunches brute-force against and triggers the right pin code
## Impact
Vary
## Risk
- Gain unauthorized access
## Redemption
- Increase code length
- Limit pin code submissions
## ID
58a84977-90e1-4156-a555-8568e83115d0
## References
- [hubsecurity](https://hubsecurity.io/the-cyber-risks-of-two-factor-authentication)