https://github.com/qeeqbox/two-factor-authentication-sim-cloning
An adversary may utilize a sim swapping attack for defeating 2fa authentication
https://github.com/qeeqbox/two-factor-authentication-sim-cloning
2factor authintacation bypass infosecsimplified qeeqbox vulnerability
Last synced: 3 months ago
JSON representation
An adversary may utilize a sim swapping attack for defeating 2fa authentication
- Host: GitHub
- URL: https://github.com/qeeqbox/two-factor-authentication-sim-cloning
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-07-23T18:18:23.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:13:41.000Z (over 1 year ago)
- Last Synced: 2025-01-16T05:55:50.574Z (4 months ago)
- Topics: 2factor, authintacation, bypass, infosecsimplified, qeeqbox, vulnerability
- Homepage:
- Size: 232 KB
- Stars: 14
- Watchers: 3
- Forks: 3
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
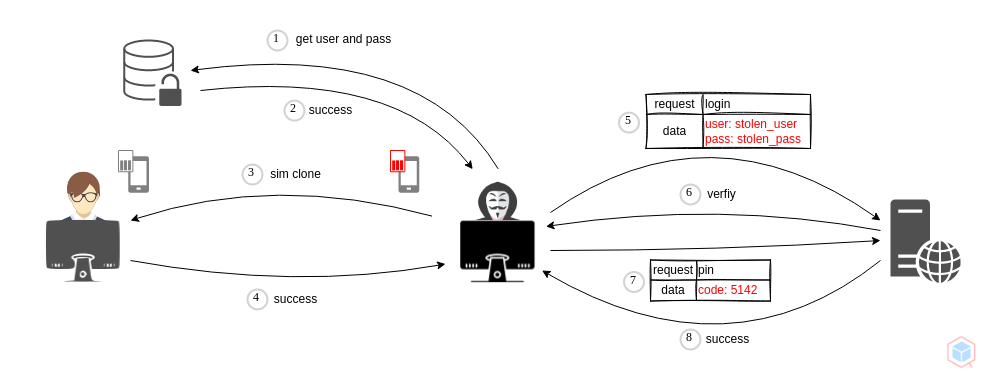
An adversary may utilize a sim swapping attack for defeating 2fa authentication.
## Example #1
1. Adversary steals the username and password pair for website
2. Adversary compromises the victim's sim card and clone it
3. Adversary logs in with the stolen username and password
4. Adversary receives a pin code on the compromised phone and uses it for verification.
## Impact
High
## Risk
- gain unauthorized access
## Redemption
- use more factors
## ID
58a84977-90e1-4156-a555-8568e83115d0
## References
- [howtogeek](hthttps://www.howtogeek.com/668922/how-to-protect-yourself-from-sim-swapping-attacks/)