https://github.com/qeeqbox/xpath-injection
A threat actor may alter the XML path language (XPath) query to read data on the target
https://github.com/qeeqbox/xpath-injection
infosecsimplified injection metadata qeeqbox visualization vulnerability xpath xpath-injection
Last synced: 3 months ago
JSON representation
A threat actor may alter the XML path language (XPath) query to read data on the target
- Host: GitHub
- URL: https://github.com/qeeqbox/xpath-injection
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-12-23T22:40:51.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T01:03:48.000Z (almost 2 years ago)
- Last Synced: 2025-03-05T17:51:51.840Z (9 months ago)
- Topics: infosecsimplified, injection, metadata, qeeqbox, visualization, vulnerability, xpath, xpath-injection
- Homepage:
- Size: 179 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
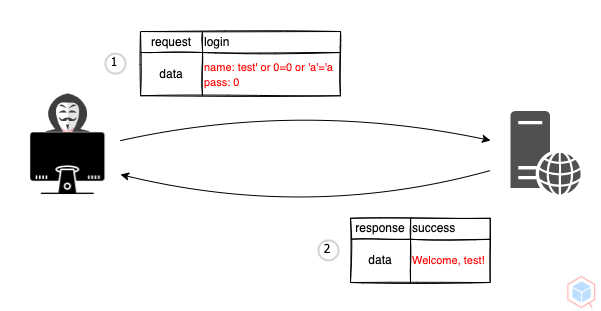
A threat actor may alter the XML path language (XPath) query to read data on the target (This is more dangerous than SQL injection because it may allow querying the whole database - XML document)
(XPath is a language that queries XML documents - the XPath expression is a locator)
## Example #1
1. Threat actor submits a malicious XPATH query to a vulnerable target
2. The target parses the malicious query (that contains expressions called a locator) and returns data from the database (XML document)
## Code
#### Target-logic (db)
```xml
test
P@ssw0rd!01
```
#### Target-logic
```c#
...
String xpath_query = "//user[name/text()='" + get("name") + "' And pass/text()='" + get("pass") + "']";
...
```
#### Target-in
```
name: test' or 0=0 or 'a'='a
pass: 0
//String xpath_query = "//user[(name/text()='test' or 0=0) or ('a'='a' And pass/text()='P@ssw0rd!01')]";
```
#### Target-Out
```
Welcome, test!
```
## Impact
High
## Names
- XPATH Injection
## Risk
- Read data
## Redemption
- Input validation
- Parametrized queries
## ID
6c020d48-9b20-4011-a513-36676994ee8e
## References
- [wiki](https://en.wikipedia.org/wiki/xpath)