https://github.com/qeeqbox/xxe-injection
A threat actor may interfere with an application's processing of extensible markup language (XML) data to view the content of a target's files
https://github.com/qeeqbox/xxe-injection
infosecsimplified injection metadata qeeqbox visualization vulnerability xee xml xxe xxe-injection
Last synced: 3 months ago
JSON representation
A threat actor may interfere with an application's processing of extensible markup language (XML) data to view the content of a target's files
- Host: GitHub
- URL: https://github.com/qeeqbox/xxe-injection
- Owner: qeeqbox
- License: agpl-3.0
- Created: 2022-12-23T17:26:38.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2024-01-29T00:58:42.000Z (over 1 year ago)
- Last Synced: 2025-01-16T05:55:50.467Z (4 months ago)
- Topics: infosecsimplified, injection, metadata, qeeqbox, visualization, vulnerability, xee, xml, xxe, xxe-injection
- Homepage:
- Size: 97.7 KB
- Stars: 2
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
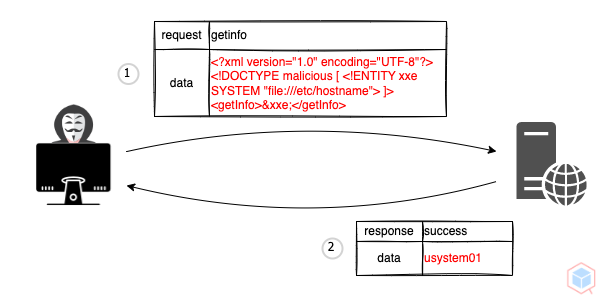
A threat actor may interfere with an application's processing of extensible markup language (XML) data to view the content of a target's files
## Example #1
1. Threat actor sends a malicious request that contains a reference to an external entity (a system identifier)
2. The target's XML processor replaces the external entity with the content dereferenced by the system identifier
## Code
#### Target Logic
```py
@app.route("/parse_xml",methods = ['POST'])
def parse_xml():
parser = etree.XMLParser(resolve_entities=True)
root = etree.fromstring(request.files['xml'].read(), parser)
response = make_response(etree.tostring(root), 200)
response.mimetype = "text/plain"
return response
```
#### Target-in
```xml
John01
```
#### Target-Out
```
Jone Doe
```
#### Target-in
```xml
]>
&xxe;
```
#### Target-Out
```
usystem01
```
## Impact
High
## Names
- XXE injection
- XEE injection
- XML injection
## Risk
- Read data
## Redemption
- Secure processing
- Disable DTD and XML external entity
## ID
4b3566ce-3f7f-40d8-b882-09f59ca967b8
## References
- [wiki](https://en.wikipedia.org/wiki/XML_external_entity_attack)