https://github.com/samhaxr/XXRF-Shots
XXRF Shots - Useful for testing SSRF vulnerability
https://github.com/samhaxr/XXRF-Shots
Last synced: 4 months ago
JSON representation
XXRF Shots - Useful for testing SSRF vulnerability
- Host: GitHub
- URL: https://github.com/samhaxr/XXRF-Shots
- Owner: samhaxr
- License: gpl-3.0
- Created: 2018-10-10T11:05:09.000Z (about 7 years ago)
- Default Branch: master
- Last Pushed: 2023-02-18T00:49:06.000Z (over 2 years ago)
- Last Synced: 2024-08-05T17:28:13.525Z (over 1 year ago)
- Language: JavaScript
- Homepage:
- Size: 26.4 KB
- Stars: 75
- Watchers: 8
- Forks: 29
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - samhaxr/XXRF-Shots - XXRF Shots - Useful for testing SSRF vulnerability (JavaScript)
README
# What is SSRF vulnerability?
Server Side Request Forgery (SSRF) is a type of vulnerability that enables attackers to send specially crafted requests through a vulnerable web application. With this technique, attackers can gain unauthorized access to internal resources behind a firewall, which would typically be inaccessible from external networks. In other words, the attacker is able to trick the server into making requests on their behalf, allowing them to manipulate the server's behavior and potentially gain access to sensitive data or resources. This vulnerability class is particularly dangerous, as it can be used to compromise entire networks and can result in significant damage and loss.
# Installation
```
git clone https://github.com/ariya/phantomjs.git
cd phantomjs
chmod +x build.py
./build.py
```
# Usage
```
./xxrf.sh
```
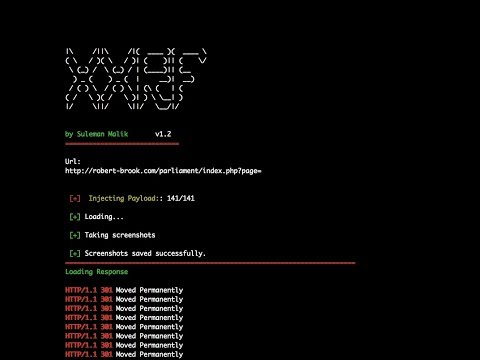
To use the script, you need to enter a URL that contains a vulnerable parameter and then hit the return key. The script is designed to execute two distinct tasks. Firstly, it injects a payload next to the vulnerable parameter in the URL, and then it processes the request by passing it to another Python script developed by @maaaaz. This script requires phantomJS to perform a screenshot function. Using the list of injected payloads, the script takes screenshots and saves them in a designated directory for screenshots.
Example: https://www.example.com/index.php?url=
# Youtube
[](https://www.youtube.com/watch?v=z9ct4OoRQ_M)