https://github.com/sasanlabs/vulnerableapp-facade
VulnerableApp-facade is probably most modern lightweight distributed farm of Vulnerable Applications built for handling wide range of vulnerabilities across tech stacks.
https://github.com/sasanlabs/vulnerableapp-facade
distributed-vulnerable-application docker docker-compose gateway hacktoberfest lightweight lua nginx openresty owasp-zap proxy-server react sasanlabs typescript vulnerable-application vulnerable-web-application
Last synced: 8 months ago
JSON representation
VulnerableApp-facade is probably most modern lightweight distributed farm of Vulnerable Applications built for handling wide range of vulnerabilities across tech stacks.
- Host: GitHub
- URL: https://github.com/sasanlabs/vulnerableapp-facade
- Owner: SasanLabs
- License: apache-2.0
- Created: 2020-12-28T13:39:53.000Z (almost 5 years ago)
- Default Branch: main
- Last Pushed: 2023-12-04T01:33:48.000Z (about 2 years ago)
- Last Synced: 2025-03-27T08:03:45.257Z (9 months ago)
- Topics: distributed-vulnerable-application, docker, docker-compose, gateway, hacktoberfest, lightweight, lua, nginx, openresty, owasp-zap, proxy-server, react, sasanlabs, typescript, vulnerable-application, vulnerable-web-application
- Language: TypeScript
- Homepage:
- Size: 6.77 MB
- Stars: 47
- Watchers: 3
- Forks: 52
- Open Issues: 21
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
README
# Owasp VulnerableApp-facade
  [](https://opensource.org/licenses/Apache-2.0) [](https://codecov.io/gh/SasanLabs/VulnerableApp-facade) [](http://makeapullrequest.com) [](https://hub.docker.com/r/sasanlabs/owasp-vulnerableapp-facade/)
As we are seeing a lot of technological enhancements in the industry in the past few years, these technical enhancements are solving one or the other problem however, with that they also bring few different vulnerabilities. Vulnerable Applications are generally written in one of the tech stacks like either Node.js or Java with a SQL or NoSQL database etc. and hence they are not able to expand to a whole new set of vulnerabilities that are present in other technologies. Also adding more vulnerabilities in a single vulnerable application makes it heavier and complex which finally makes it unmaintainable. So VulnerableApp-facade is built to solve this problem by building a distributed farm of Vulnerable Applications such that they can be built agnostic to tech stacks.
## High Level Design Details
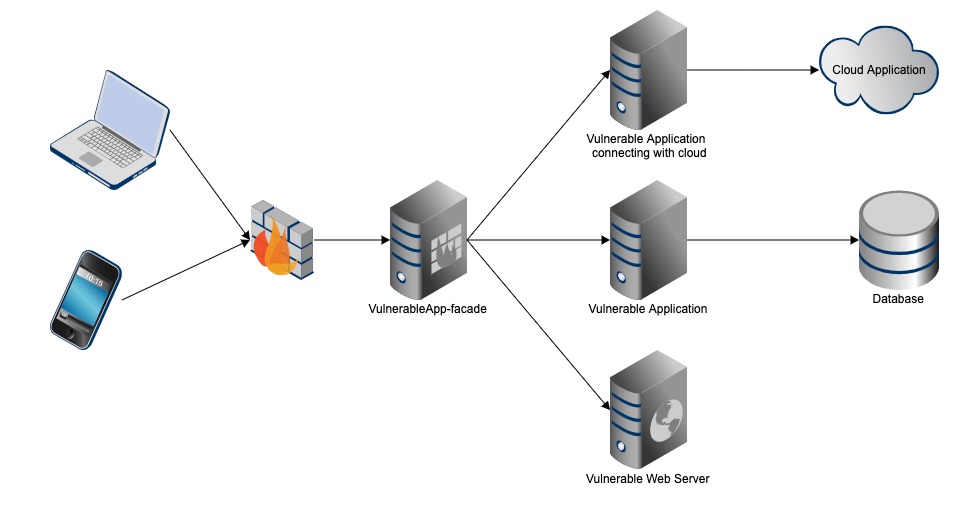
**VulnerableApp-facade** is a small component which acts as a webserver and a gateway. It routes the calls to different Vulnerable Applications which are registered with it based on an url pattern. It also exposes a schema/contract (Vulnerability Definition) and if a vulnerable application adhere to that then it will be able to interact and route the traffic to that vulnerable application. It also provides the generic skeleton UI which it builds by reading the provided schema (Vulnerability Definition) from the vulnerable application and then loads the UI specific to vulnerable application inside the skeleton UserInterface.
### Glimpse of the Owasp VulnerableApp-Facade
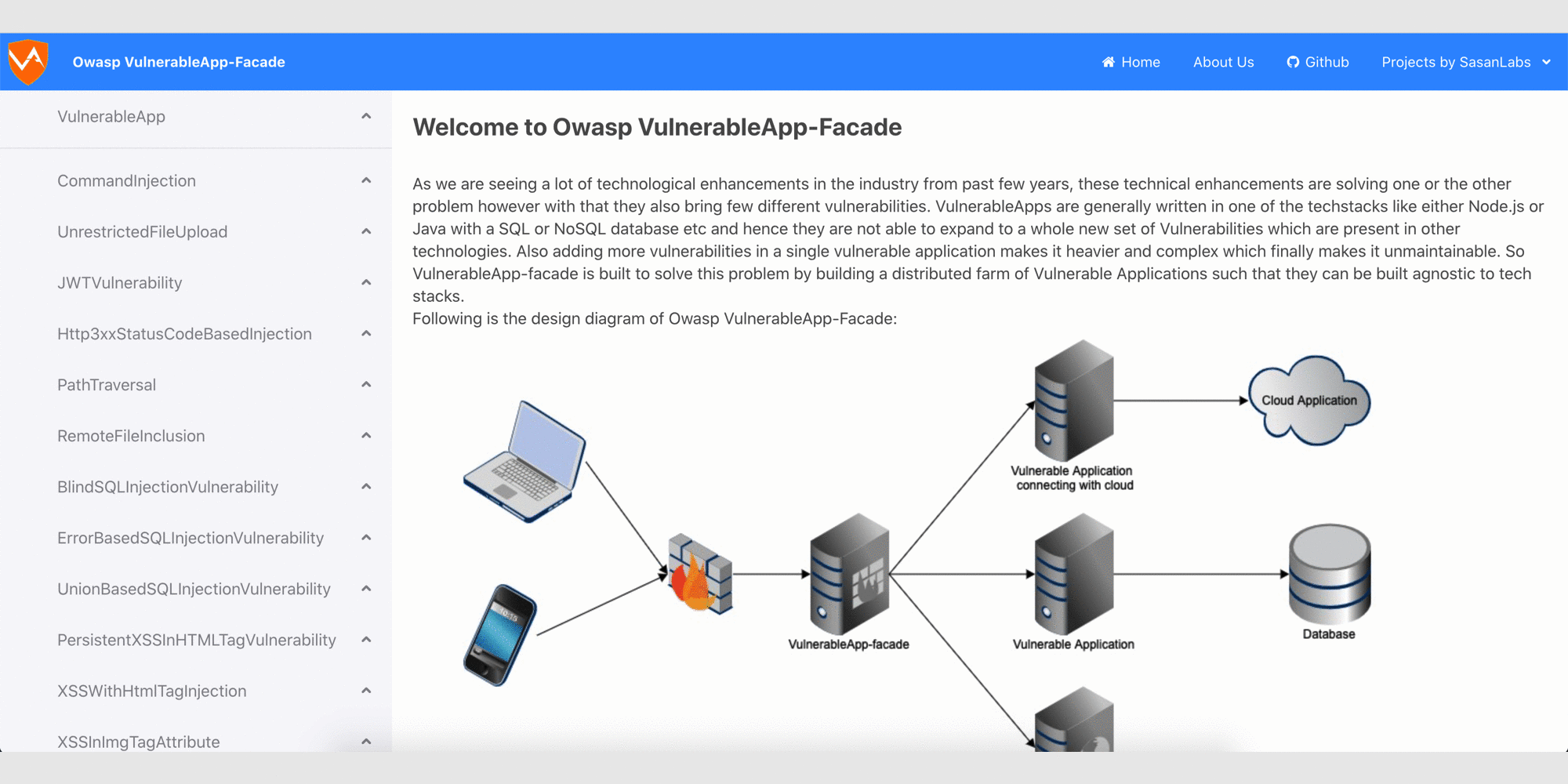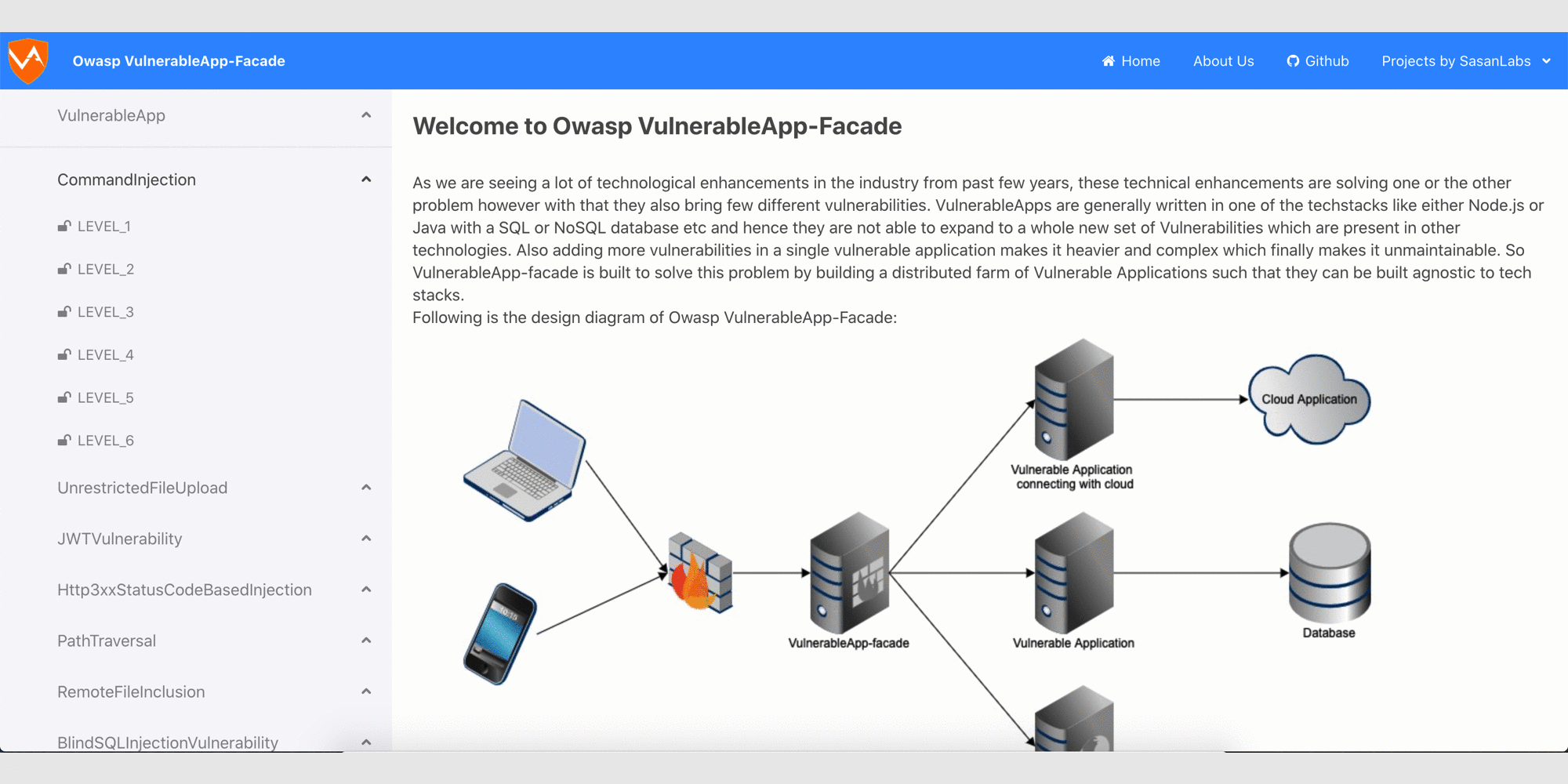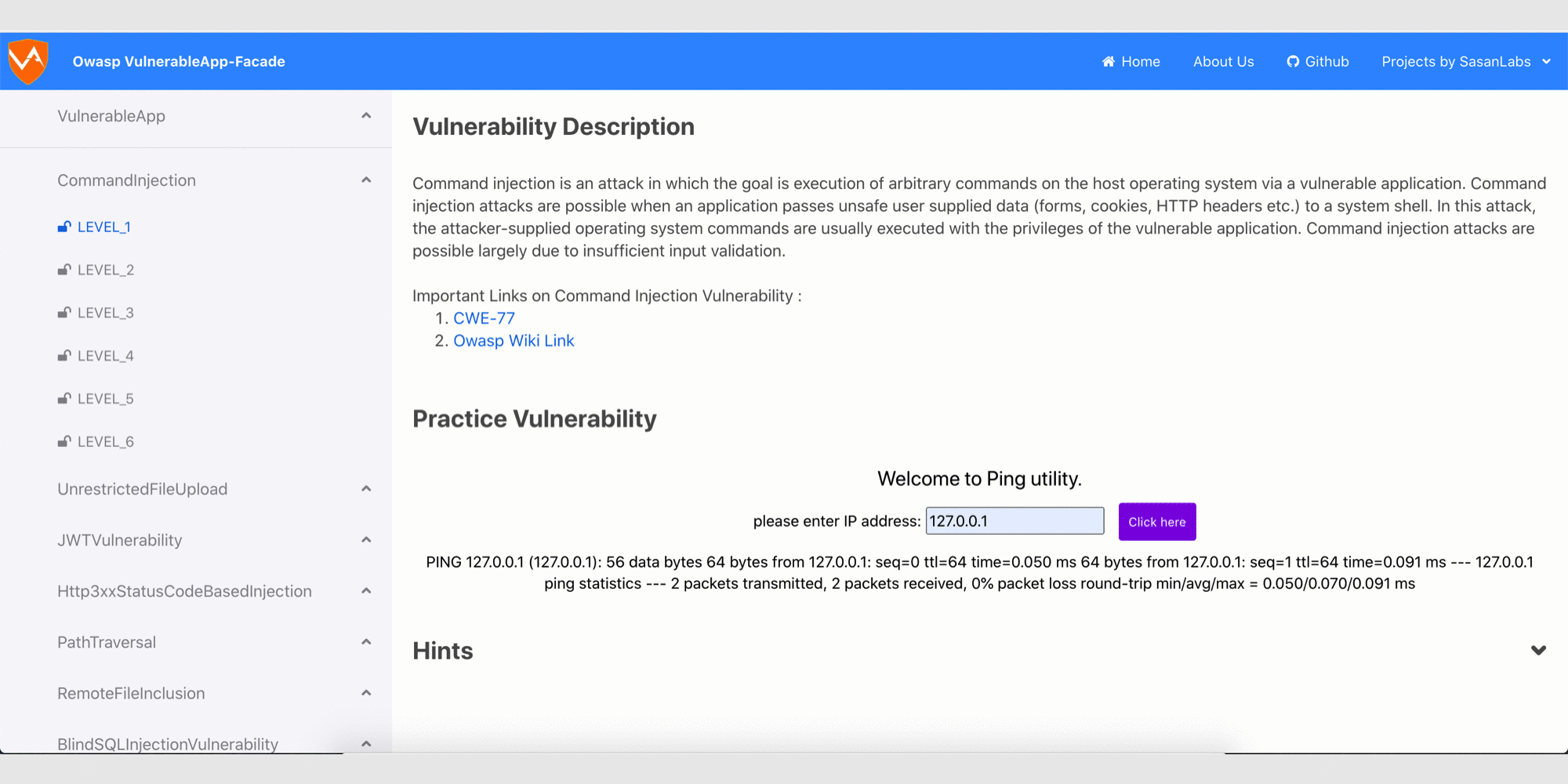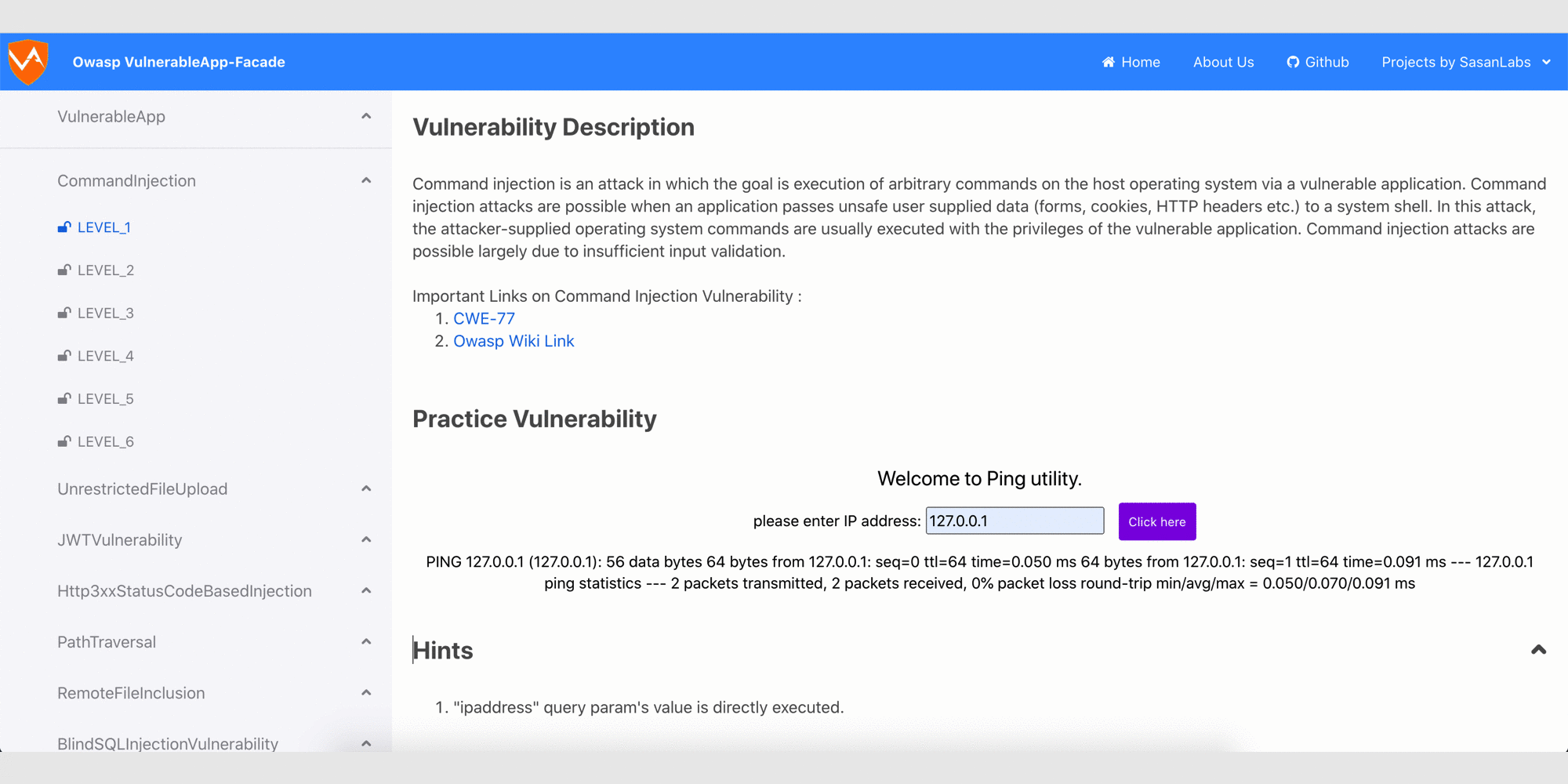
## How to run the project
VulnerableApp-facade is a farm of vulnerable applications where each application runs as a docker container. VulnerableApp-facade has `docker-compose.yml` file which contains docker configuration of other vulnerable applications along with docker configuration of VulnerableApp-facade.
### Simple Start ###
In order to run entire suit please follow the below steps:
1. Download and Install [Docker Compose](https://docs.docker.com/compose/install/).
2. Clone the github repository
3. Open the terminal and navigate to the Project root directory
4. Run the command: ``` docker-compose pull && docker-compose up ```
5. Navigate to browser and visit `http://localhost` to play with the application.
### Advanced Start ###
As [docker-compose.yml](https://github.com/SasanLabs/VulnerableApp-facade/blob/main/docker-compose.yml) contains all the applications which adhere to the schema of VulnerableApp-facade so in case you are looking for specific vulnerable applications like only Java related vulnerable applications then remove other vulnerable applications from [docker-compose.yml](https://github.com/SasanLabs/VulnerableApp-facade/blob/main/docker-compose.yml) and then run steps as mentioned in the [Simple start step](#simple-start).
## How to Contribute to the project
VulnerableApp-facade have majorly 2 components:
1. React UI component
2. Lua module
**React UI component** is used to load the skeleton UserInterface and Lua module is used to merge the Vulnerability Definitions exposed by different vulnerable applications.
In order to do changes in React UI component,
1. Start the VulnerableApplication-facade using steps mentioned at [Simple Start](#simple-start). This is an important step as it will start the underlying VulnerableApplications which will be invoked by the Facade UI internally. Consider the underlying VulnerableApplications as the backend for Facade application.
2. Navigate to `facade-app` folder
3. Do the code changes
4. Run `npm run start` which will start the npm server.
5. Navigate to `http://localhost:3000` to verify/view the changes
**Lua module** is used for handling the Nginx configuration and communication between facade application and VulnerableApplications which is the backend for facade application.
In order to make changes in Lua module, the easy way is to add the changes in the lua files and build the docker image with those changes
by executing command: ```docker build . -t sasanlabs/owasp-vulnerableapp-facade:unreleased``` and then run the project as mentioned at [How to run the project](#how-to-run-the-project)
Before raising the PR with UI changes please execute `npm run pretty` command in `facade-app` folder to auto handle formatting of javascript/typescript files.
## Integrated Vulnerable Applications
1. [Owasp VulnerableApp](https://github.com/SasanLabs/VulnerableApp)
2. [VulnerableApp-jsp](https://github.com/SasanLabs/VulnerableApp-jsp)
3. [VulnerableApp-php](https://github.com/SasanLabs/VulnerableApp-php)
## Contact ##
Please raise a github issue for enhancement/issues in VulnerableApp-facade or send email to karan.sasan@owasp.org regarding queries
we will try to resolve issues asap.
## Documentation and References
1. [Documentation](https://sasanlabs.github.io/VulnerableApp)
2. [Design Documentation](https://sasanlabs.github.io/VulnerableApp/DesignDocumentation.html)
3. [Owasp VulnerableApp](https://owasp.org/www-project-vulnerableapp/)
4. [Overview video for OWASP Spotlight series](https://www.youtube.com/watch?v=HRRTrnRgMjs)
5. [Overview Video](https://www.youtube.com/watch?v=AjL4B-WwrrA&ab_channel=OwaspVulnerableApp)
### Blogs
1. [Overview of Owasp-VulnerableApp - Medium article](https://hussaina-begum.medium.com/an-extensible-vulnerable-application-for-testing-the-vulnerability-scanning-tools-cc98f0d94dbc)
2. [Overview of Owasp-VulnerableApp - Blogspot post](https://hussaina-begum.blogspot.com/2020/10/an-extensible-vulnerable-application.html)
3. [Introduction to Owasp VulnerableApp by Kenji Nakajima](https://jpn.nec.com/cybersecurity/blog/220520/index.html)
### Troubleshooting references
1. [Reddit exploiting SQL Injection Vulnerability](https://www.reddit.com/r/hacking/comments/11wtf17/owasp_vulnerableappfacade_sql_injection/)
## Other links ##
1. [Owasp Project link](https://owasp.org/www-project-vulnerableapp-facade/)
2. [Github pages](https://sasanlabs.github.io/VulnerableApp-facade/)