https://github.com/scotty-kdw/ARM-Analyzer
Backward Taint Analysis (GUI) on Desktop : Analyzing trace log to determine exploitability by tracking data propagation
https://github.com/scotty-kdw/ARM-Analyzer
Last synced: 5 months ago
JSON representation
Backward Taint Analysis (GUI) on Desktop : Analyzing trace log to determine exploitability by tracking data propagation
- Host: GitHub
- URL: https://github.com/scotty-kdw/ARM-Analyzer
- Owner: scotty-kdw
- Created: 2017-01-01T08:22:46.000Z (almost 9 years ago)
- Default Branch: master
- Last Pushed: 2017-01-06T02:34:23.000Z (almost 9 years ago)
- Last Synced: 2024-08-05T17:26:01.256Z (over 1 year ago)
- Language: C#
- Size: 10.8 MB
- Stars: 46
- Watchers: 4
- Forks: 7
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - scotty-kdw/ARM-Analyzer - Backward Taint Analysis (GUI) on Desktop : Analyzing trace log to determine exploitability by tracking data propagation (C# #)
README
## ARM-Analyzer : Backward Taint Analyzer for ARM architecture ##
### Abstract ###
We have developed a set of tools for analyzing crashes occurred on Linux OS and ARM architecture to determine exploitability with taint analysis for practical use. For the analysis, Dynamic Binary Instrumentation (DBI) is required to extract context information of each instruction at runtime. Unfortunately, most existing DBI tools have been developed for x86 architecture. Therefore, we have developed a dedicated tool called [ARM-Tracer](https://github.com/scotty-kdw/ARM-Tracer#arm-tracer "ARM-Tracer") based on ptrace system call. ARM-Tracer can dynamically trace a specific thread in the multi-threaded environment and generate a trace log until the target gets crashed. Then, the trace log is analyzed by another tool that we have developed to perform the backward taint analysis on Desktop for efficiency. The tool is named [ARM-Analyzer](https://github.com/scotty-kdw/ARM-Analyzer#arm-analyzer "ARM-Analyzer"), a stand-alone GUI application developed in C# language, which lets us know whether the crash is affected by the input data. For this, we analyzed ARM instructions to identify taint objects of each instruction.
### Our Tools ###
[**▼ ARM-Tracer**](https://github.com/scotty-kdw/ARM-Tracer#arm-tracer "ARM-Tracer") - Trace Log Generation (CLI) on a target device or emulator : Generating context information of every instruction from a specific point (input data) to a crash point
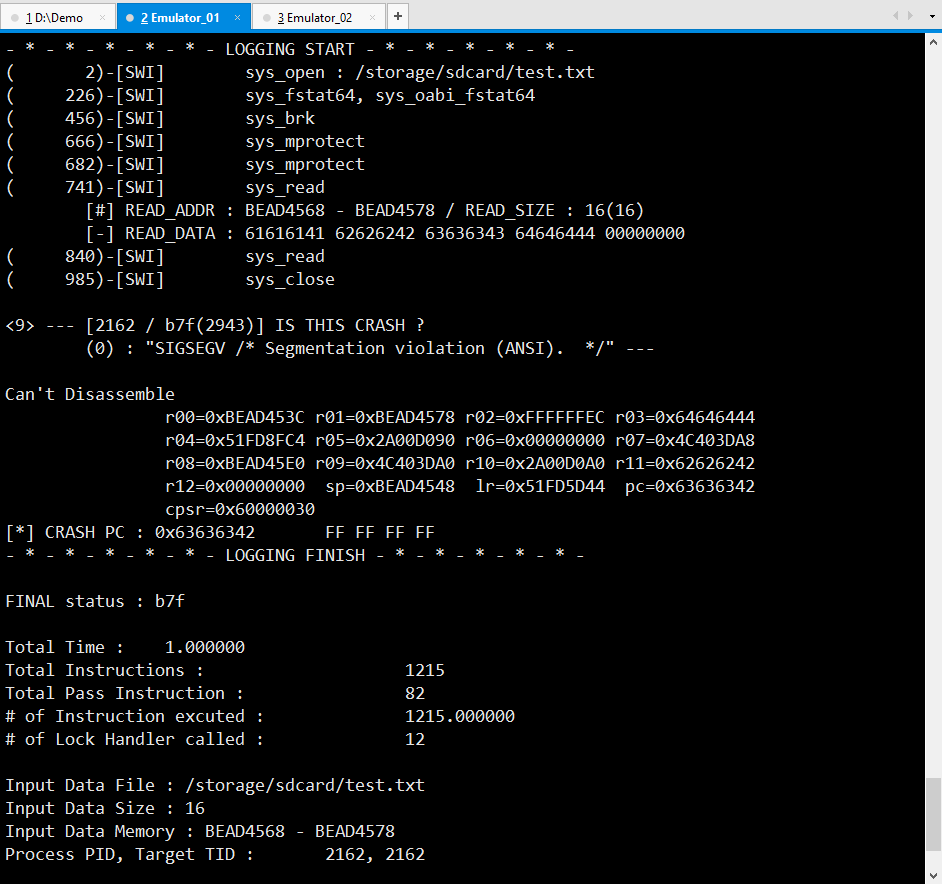
[**▼ ARM-Analyzer**](https://github.com/scotty-kdw/ARM-Analyzer#arm-analyzer "ARM-Analyzer") - Backward Taint Analysis (GUI) on Desktop : Analyzing trace log to determine exploitability by tracking data propagation
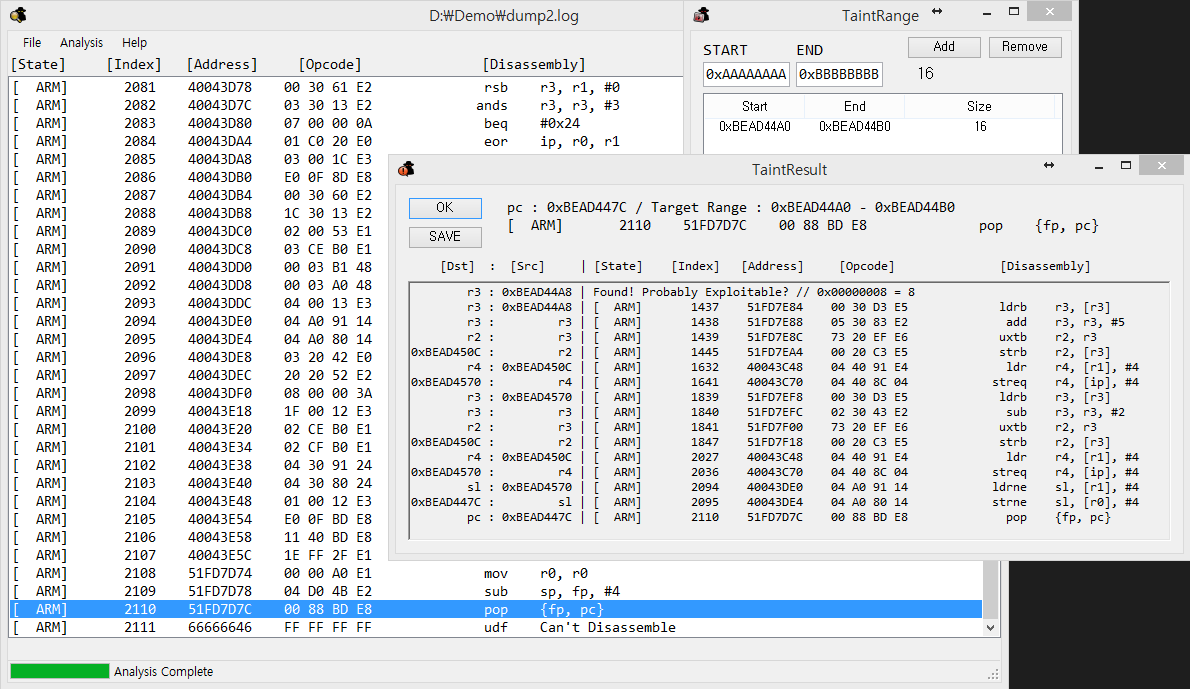
##
**Compile for ARM-Tracer**
$ sudo apt-get install gcc-arm-linux-androideabi
$ ./make
##
**Thanks to**
- VDT (Visual Data Tracer) : Crash analyzer for user level applications on Windows OS (x86) `Our motivation`
- Capstone : Pretty good multi-architecture disassembler