https://github.com/securifybv/PHPUnserializeCheck
PHP Unserialize Check - Burp Scanner Extension
https://github.com/securifybv/PHPUnserializeCheck
Last synced: 12 months ago
JSON representation
PHP Unserialize Check - Burp Scanner Extension
- Host: GitHub
- URL: https://github.com/securifybv/PHPUnserializeCheck
- Owner: securifybv
- Created: 2017-02-27T19:37:17.000Z (about 9 years ago)
- Default Branch: master
- Last Pushed: 2018-03-15T08:24:03.000Z (almost 8 years ago)
- Last Synced: 2024-10-26T11:32:09.058Z (over 1 year ago)
- Language: Java
- Homepage:
- Size: 105 KB
- Stars: 18
- Watchers: 5
- Forks: 15
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - securifybv/PHPUnserializeCheck - PHP Unserialize Check - Burp Scanner Extension (Java)
README
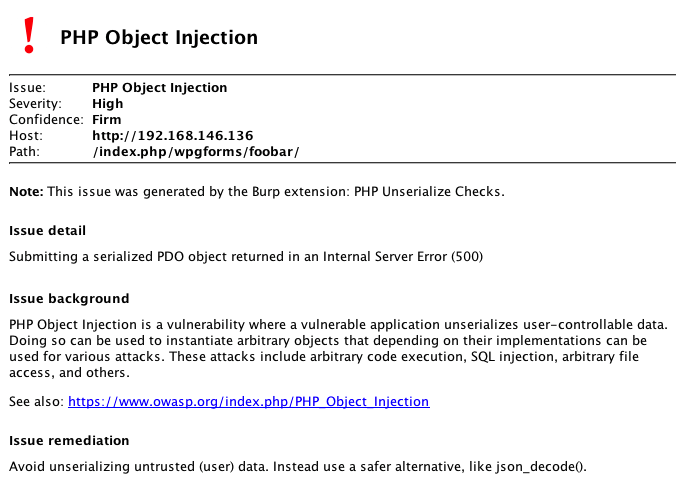
# PHP Unserialize Check
This Burp Scanner Extension tries to find PHP Object Injection Vulnerabilities.
It passes a serialized `PDO` object to the found injection points. If PHP tries to unserialize this object a fatal exception is thrown triggered in the object's `__wakeup()` method (ext/pdo/pdo_dbh.c):
```
static PHP_METHOD(PDO, __wakeup)
{
zend_throw_exception_ex(php_pdo_get_exception(), 0, "You cannot serialize or unserialize PDO instances");
}
```
If `display_errors` is disabled, this will result in a 500 Internal Server Error. If this is the case the check will try to unserialize a stdClass object and an empty array. If either one returns a 200 OK, it is assumed that the code is vulnerable to PHP Object Injection.
If `display_errors` is enabled, the fatal exception is returned to the user, making it easier to detected the vulnerability.
Based on http://blog.portswigger.net/2012/12/sample-burp-suite-extension-custom_20.html