https://github.com/sigoden/proxyfor
A powerful and flexible proxy CLI for capturing and inspecting HTTP(S) and WS(S) traffic, with TUI and WebUI.
https://github.com/sigoden/proxyfor
cli forward-proxy http http2 https man-in-the-middle proxy proxy-server reverse-proxy rust websocket
Last synced: 9 months ago
JSON representation
A powerful and flexible proxy CLI for capturing and inspecting HTTP(S) and WS(S) traffic, with TUI and WebUI.
- Host: GitHub
- URL: https://github.com/sigoden/proxyfor
- Owner: sigoden
- License: apache-2.0
- Created: 2024-03-05T01:56:58.000Z (almost 2 years ago)
- Default Branch: main
- Last Pushed: 2025-01-19T08:20:48.000Z (about 1 year ago)
- Last Synced: 2025-04-14T05:56:40.730Z (11 months ago)
- Topics: cli, forward-proxy, http, http2, https, man-in-the-middle, proxy, proxy-server, reverse-proxy, rust, websocket
- Language: Rust
- Homepage:
- Size: 253 KB
- Stars: 415
- Watchers: 4
- Forks: 28
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE-APACHE
Awesome Lists containing this project
- jimsghstars - sigoden/proxyfor - A powerful and flexible proxy CLI for capturing and inspecting HTTP(S) and WS(S) traffic, with TUI and WebUI. (Rust)
- awesome-ops - sigoden/proxyfor - 2.0|441|2024-03-05|2025-01-19 | 一个强大而灵活的代理 CLI,用于捕获和检查 HTTP(S) 和 WS(S) 流量,带有 TUI 和 WebUI。 | (命令行工具)
README
# Proxyfor
[](https://github.com/sigoden/proxyfor/actions/workflows/ci.yaml)
[](https://crates.io/crates/proxyfor)
[](https://hub.docker.com/r/sigoden/proxyfor)
A powerful and flexible proxy CLI for capturing and inspecting HTTP(S) and WS(S) traffic.
## Features
- Supports forward/reverse proxy
- Provides TUI & WebUI
- Enables filtering & searching
- Handles HTTP/HTTPS/WS/WSS protocols
- Comes with a tool for installing CA certificates
- Allows export in Markdown, cURL, or HAR formats
- Captures request/response in a non-blocking, streaming way
- Offers a single-file portable executable for use across Windows/macOS/Linux
## Screenshots
**Terminal User Interface (TUI)**

**Web User Interface (WebUI)**

## Installation
### With cargo
```
cargo install proxyfor
```
### With docker
```
docker run -v ~/.proxyfor:/.proxyfor -p 8080:8080 --rm sigoden/proxyfor --web
```
### Binaries on macOS, Linux, Windows
Download from [Github Releases](https://github.com/sigoden/proxyfor/releases), unzip and add proxyfor to your $PATH.
## Proxy Modes Explained
### Forward Proxy
In this mode, your client applications (e.g., web browsers, curl) are configured to send their requests to `proxyfor`, which then forwards them to the target servers. You would configure your client to use a proxy at `http://127.0.0.1:8080`.
```bash
proxyfor
curl -x http://127.0.0.1:8080 httpbin.org/ip
```
### Reverse Proxy
In reverse proxy mode, `proxyfor` sits in front of a target server. Clients access `proxyfor` and it forwards the requests to the defined URL. This mode is ideal when clients cannot be configured to use a proxy.
```bash
proxyfor https://httpbin.org
curl http://127.0.0.1:8080/ip
```
## Command Line Interface (CLI)
```
Usage: proxyfor [OPTIONS] [URL]
Arguments:
[URL] Reverse proxy url
Options:
-l, --listen Listening ip and port address [default: 0.0.0.0:8080]
-f, --filters Only inspect http(s) traffic whose `{method} {uri}` matches the regex
-m, --mime-filters Only inspect http(s) traffic whose content-type matches the value
-W, --web Enable user-friendly web interface
-T, --tui Eenter TUI
-D, --dump Dump all traffics
-h, --help Print help
-V, --version Print version
```
### Choosing User Interface
`proxyfor` provides several ways to interact with captured traffic:
```sh
proxyfor # Enter TUI, equal to `proxyfor --tui`
proxyfor --web # Serve WebUI
proxyfor --web --tui # Serve WebUI + Enter TUI
proxyfor --dump # Dump all traffics to console
proxyfor > proxyfor.md # Dump all traffics to markdown file
```
### Specifying Address and Port
Customize the listening address and port:
```sh
proxyfor -l 8081
proxyfor -l 127.0.0.1
proxyfor -l 127.0.0.1:8081
```
### Filtering Traffic
Apply regex filters to limit captured traffic based on method and URI:
```sh
proxyfor -f httpbin.org/ip -f httpbin.org/anything
proxyfor -f '/^(get|post) https:\/\/httpbin.org/'
```
Filter based on MIME types:
```sh
proxyfor -m application/json -m application/ld+json
proxyfor -m text/
```
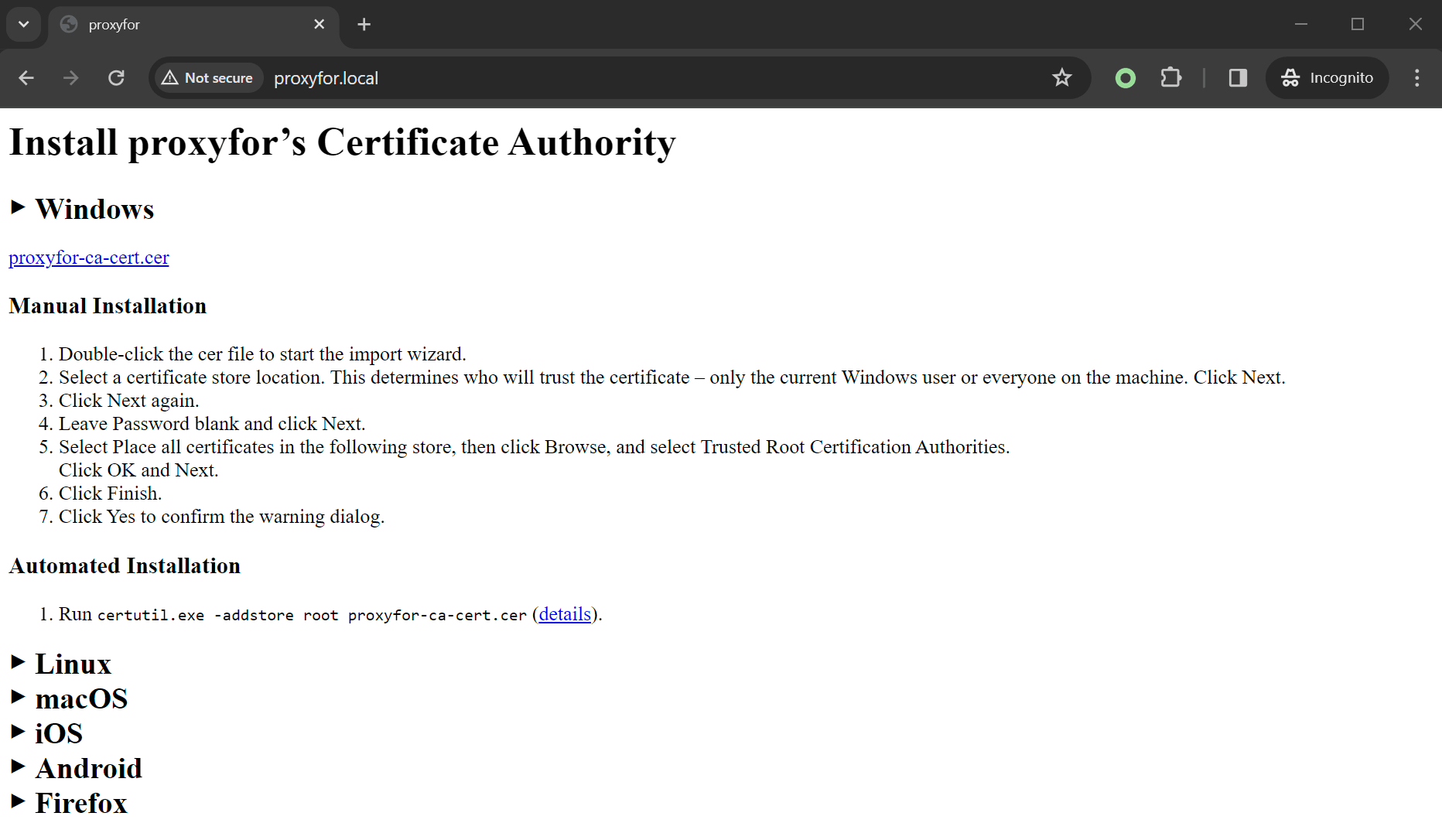
## CA Certificate Installation
To decrypt HTTPS traffic, you must install `proxyfor`'s CA certificate on your device. The easiest way to do this is to use the built-in certificate installation app.
1. Start `proxyfor` with desired proxy settings.
2. On your target device, configure the device to use `proxyfor` as the proxy.
3. Open a web browser on the target device and navigate to [proxyfor.local](http://proxyfor.local).
4. Follow the on-screen instructions to download and install the CA certificate.
## License
Copyright (c) 2024-∞ proxyfor-developers.
Proxyfor is made available under the terms of either the MIT License or the Apache License 2.0, at your option.
See the LICENSE-APACHE and LICENSE-MIT files for license details.