https://github.com/simeononsecurity/Shodan_PS
A collection of PowerShell modules for interacting with the Shodan API. Includes modules for returning information about the API, client IP, DNS, exploits, honeypot scores, hosts, ports, profiles, and scans. Shodan API key required. Query and scan credits used.
https://github.com/simeononsecurity/Shodan_PS
enumeration powershell powershell-module powershell-script shodan shodan-api
Last synced: 9 months ago
JSON representation
A collection of PowerShell modules for interacting with the Shodan API. Includes modules for returning information about the API, client IP, DNS, exploits, honeypot scores, hosts, ports, profiles, and scans. Shodan API key required. Query and scan credits used.
- Host: GitHub
- URL: https://github.com/simeononsecurity/Shodan_PS
- Owner: simeononsecurity
- License: mit
- Created: 2020-11-15T01:28:41.000Z (about 5 years ago)
- Default Branch: main
- Last Pushed: 2024-07-26T23:00:06.000Z (over 1 year ago)
- Last Synced: 2025-04-23T06:36:15.633Z (10 months ago)
- Topics: enumeration, powershell, powershell-module, powershell-script, shodan, shodan-api
- Language: PowerShell
- Homepage: https://simeononsecurity.com/github/shodan-powershell/
- Size: 1.1 MB
- Stars: 24
- Watchers: 2
- Forks: 7
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
- awesome-ip-search-engines - Shodan PS
README
# Shodan_PS
[](https://github.com/sponsors/simeononsecurity) [](https://github.com/simeononsecurity/Shodan_PS/actions/workflows/virustotal.yml)
A collection of PowerShell Modules for Interacting with the Shodan API
**Notes:**
- You'll need you Shodan API key, which can be found on your [Shodan Account](https://account.shodan.io/)
- Examples of the APIs used in the modules may be found on the [Shodan Developers Page](https://developer.shodan.io/api)
- Certain Modules may use scan or query credits Query Credits are used when you download data via the website, CLI or API (what these scripts do).
Since we are using the API it is important to note that query credits are deducted if:
1. A search filter is used
2. Page 2 or beyond is requested
The credits renew at the start of the month and 1 credit lets you download 100 results.
As for scan credits, 1 scan credit lets you scan 1 IP, and they also renew at the start of the month.
Please view the Shodan Help Center [HERE](https://help.shodan.io/the-basics/credit-types-explained) for full details.
## Table of Contents
- [Download Instructions](https://github.com/simeononsecurity/Shodan_PS#download)
- [Installation Instructions](https://github.com/simeononsecurity/Shodan_PS#install)
- **Modules**
- [Get-ShodanAPIInfo](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanAPIInfo) - Return information about the API plan belonging to the given API key.
- [Get-ShodanClientHTTPHeaders](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanClientHTTPHeaders) - Shows the HTTP headers that your client sends when connecting to a webserver.
- [Get-ShodanClientIP](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanClientIP) - Gets your current IP address as seen from the Internet.
- [Get-ShodanDNSDomain](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanDNSDomain) - Gets all the subdomains and other DNS entries for the given domain
- [Get-ShodanDNSResolve](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanDNSResolve) - Looks up the IP addresses for the provided hostname(s).
- [Get-ShodanDNSReverse](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanDNSReverse) - Looks up the hostnames that have been defined for the given list of IP addresses.
- [Get-ShodanExploitCount](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanExploitCount) - Searches for exploits but only returns information about the total number of matches related to the search term, and optionally the exploit author, platform, port, source, or type.
- [Get-ShodanHoneyScore](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanHoneyScore) - Calculates a honeypot probability score ranging from 0 (not a honeypot) to 1.0 (is a honeypot).
- [Get-ShodanHostCount](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanHostCount) - Returns the total number of results of "/shodan/host/search" provides.
- [Get-ShodanHostIP](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanHostIP) - Search Shodan with IP address.
- [Get-ShodanHostSearch](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanHostSearch) - Search Shodan using the same query syntax as the website and use facets to get summary information for different properties.
- [Get-ShodanHostSearchFacets](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanHostSearchFacets) - This module returns a list of search filters that can be used in the search query.
- [Get-ShodanHostSearchFilters](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanHostSearchFilters) - This module returns a list of search filters that can be used in the search query.
- [Get-ShodanPorts](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanPorts) - List all ports that Shodan is crawling on the Internet.
- [Get-ShodanProfile](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanProfile) - Returns information about the Shodan account linked to this API key
- [Get-ShodanScanID](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanScanID) - Check the progress of a previously submitted scan request
- [Get-ShodanScanProtocols](https://github.com/simeononsecurity/Shodan_PS/tree/main/Get-ShodanScanProtocols) - List all protocols that can be used when performing on-demand Internet scans via Shodan
- [Set-ShodanScanIP](https://github.com/simeononsecurity/Shodan_PS/tree/main/Set-ShodanScanIP) - Use this module to request Shodan to crawl a network.
## Download
You will need to clone or download the scripts to your computer.
You can use the Code dropdown menu on this repo page by scrolling up, or just copy and paste the following link: [https://github.com/simeononsecurity/Shodan_PS.git](https://github.com/simeononsecurity/Shodan_PS.git)

For this example we will be cloning the repo within Git Bash, after clicking on the clipboard icon as seen above, we can type git clone and right click the Git Bash window to select paste from the dropdown menu:
```
exampleuser@exampleComputer MINGW64 ~/Documents/Github git clone https://github.com/simeononsecurity/Shodan_PS.git
```
For detailed instructions on cloning please view [the github documentation.](https://docs.github.com/en/free-pro-team@latest/github/creating-cloning-and-archiving-repositories/cloning-a-repository)
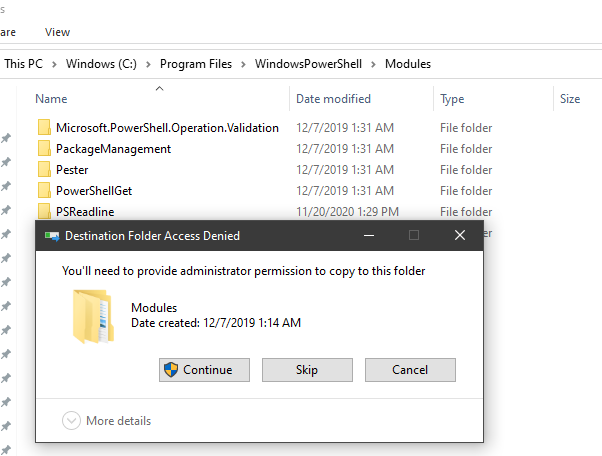
Once you have the files, you need to copy the files to C:\Program Files\WindowsPowerShell\Modules, doing this will prompt dialog saying that access is denied, click continue to finish copying the files to this location and then proceed to the installation instructions [here](#Install)
**OR**
You can use the Code dropdown menu on this repo page by scrolling up, or just click on the following link:
[https://github.com/simeononsecurity/Shodan_PS/archive/main.zip](https://github.com/simeononsecurity/Shodan_PS/archive/main.zip)

Unzip main.zip by right clicking on the file and selecting extract here from the dropdown menu.
Once you have the files, you need to copy the files to C:\Program Files\WindowsPowerShell\Modules, doing this will prompt dialog saying that access is denied, click continue to finish copying the files to this location and then proceed to the installation instructions [here](#Install)

## PowerShell Gallery:
```
Install-Module -Name Get-ShodanAPIInfo
Install-Module -Name Get-ShodanClientHTTPHeaders
Install-Module -Name Get-ShodanClientIP
Install-Module -Name Get-ShodanDNSDomain
Install-Module -Name Get-ShodanDNSResolve
Install-Module -Name Get-ShodanDNSReverse
Install-Module -Name Get-ShodanExploitCount
Install-Module -Name Get-ShodanExploitSearch
Install-Module -Name Get-ShodanHoneyScore
Install-Module -Name Get-ShodanHostCount
Install-Module -Name Get-ShodanHostIP
Install-Module -Name Get-ShodanHostSearch
Install-Module -Name Get-ShodanHostSearchFacets
Install-Module -Name Get-ShodanHostSearchFilters
Install-Module -Name Get-ShodanPorts
Install-Module -Name Get-ShodanProfile
Install-Module -Name Get-ShodanScanID
Install-Module -Name Get-ShodanScanProtocols
Install-Module -Name Set-ShodanScanIP
```
## Manual Install:
To install the modules You will need to run a PowerShell window as administrator.
There are two ways of doing this:
The first way is by right clicking the PowerShell icon on the Desktop and selecting Run as Administrator from the dropdown menu.

**OR**
By typing p (or however many characters it takes PowerShell to show up) into the search bar and clicking on Run as Administrator.

You will need to be in the directory that you copied the scripts to.
Run the following command to change your working directory:
```
PS C:\WINDOWS\system32> cd 'C:\Program Files\WindowsPowerShell\Modules\Shodan_PS'
PS C:\Program Files\WindowsPowerShell\Modules\Shodan_PS>
```
On Windows client computers we need to change the PowerShell execution policy which is Restricted by default.
For more information please read this [Microsoft documentation.](https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-7.1)
Run the following command to set the policy to RemoteSigned and enter y to select that Yes you want to change the policy.
```
PS C:\Program Files\WindowsPowerShell\Modules\Shodan_PS> Set-ExecutionPolicy RemoteSigned
Execution Policy Change
The execution policy helps protect you from scripts that you do not trust. Changing the execution policy might expose you to the
security risks described in the about_Execution_Policies help topic at https:/go.microsoft.com/fwlink/?LinkID=135170. Do you want to
change the execution policy?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): y
```
Once the execution policy has been changed, you can run the following command to Import the modules.
```
PS C:\Program Files\WindowsPowerShell\Modules\Shodan_PS> Get-ChildItem -Recurse *.psm1 | Import-Module
```
Now you can run any of the scripts as a module via powershell.
Explore the World of Cybersecurity
#### Links:
- [github.com/simeononsecurity](https://github.com/simeononsecurity)
- [simeononsecurity.ch](https://simeononsecurity.ch)