https://github.com/slashdevops/idp-scim-sync
Keep your AWS Single Sign-On (SSO) groups and users in sync with your Google Workspace directory
https://github.com/slashdevops/idp-scim-sync
aws aws-lambda-golang aws-sso aws-sso-scim go-cli google-workspace scim sso
Last synced: about 1 month ago
JSON representation
Keep your AWS Single Sign-On (SSO) groups and users in sync with your Google Workspace directory
- Host: GitHub
- URL: https://github.com/slashdevops/idp-scim-sync
- Owner: slashdevops
- License: apache-2.0
- Created: 2021-07-24T10:59:27.000Z (over 4 years ago)
- Default Branch: main
- Last Pushed: 2024-08-27T07:38:13.000Z (over 1 year ago)
- Last Synced: 2024-08-27T08:39:44.700Z (over 1 year ago)
- Topics: aws, aws-lambda-golang, aws-sso, aws-sso-scim, go-cli, google-workspace, scim, sso
- Language: Go
- Homepage:
- Size: 4.66 MB
- Stars: 91
- Watchers: 2
- Forks: 20
- Open Issues: 6
-
Metadata Files:
- Readme: README.md
- Contributing: CONTRIBUTING.md
- Funding: .github/FUNDING.yml
- License: LICENSE
- Code of conduct: CODE_OF_CONDUCT.md
- Security: SECURITY.md
Awesome Lists containing this project
README
# 🆔 idp-scim-sync
[](https://bestpractices.coreinfrastructure.org/projects/5348)
[](https://github.com/slashdevops/idp-scim-sync/actions/workflows/build.yml)

[](https://goreportcard.com/report/github.com/slashdevops/idp-scim-sync)
[](https://github.com/slashdevops/idp-scim-sync/blob/main/LICENSE)
[](https://github.com/slashdevops/idp-scim-sync/actions/workflows/release.yml)
[](https://github.com/slashdevops/idp-scim-sync/releases)
[](https://codecov.io/gh/slashdevops/idp-scim-sync)
Keep your [AWS IAM Identity Center](https://aws.amazon.com/iam/identity-center/) (formerly AWS SSO) in sync with your [Google Workspace](https://workspace.google.com/) directory using an [AWS Lambda function](https://aws.amazon.com/lambda/). 🚀
## ✨ Features
* ✅ **Extended Attribute Support**: Syncs extended AWS SSO SCIM API fields as described in the [official documentation](https://docs.aws.amazon.com/singlesignon/latest/developerguide/limitations.html).
* ✅ **Efficient Data Retrieval**: Uses [partial responses](https://cloud.google.com/storage/docs/json_api#partial-response) from the Google Workspace API to fetch only the data you need.
* ✅ **Nested Groups Support**: Supports nested groups in Google Workspace thanks to the `includeDerivedMembership` API query parameter.
* ✅ **Multiple Deployment Options**: Can be deployed via the `AWS Serverless Application Repository`, as a `Container Image`, or as a `CLI`.
* ✅ **Incremental Sync**: Drastically reduces the number of requests to the AWS SSO SCIM API by using a [state file](docs/State-File-example.md) to track changes.
## Compatibility
This project is compatible with the latest AWS Lambda runtimes. Since version `v0.0.19`, it uses the `provided.al2` runtime and `arm64` architecture.
| Version Range | AWS Lambda Runtime | Architecture | Deprecation Date |
| -------------------- | ------------------ | ------------------ | ---------------- |
| `<= v0.0.18` | Go 1.x | amd64 (Intel) | 2023-12-31 |
| `>= v0.0.19 < v0.31.0` | provided.al2 | arm64 (Graviton 2) | 2026-06-30 |
| `>= v0.31.0` | provided.al2023 | arm64 (Graviton 2) | 2029-06-30 |
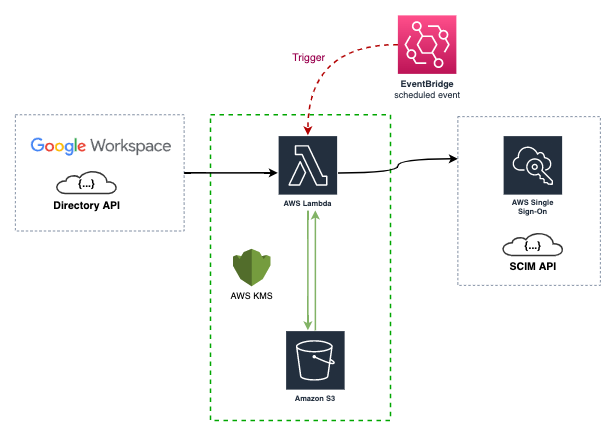
## ⚙️ How It Works
The AWS Lambda function is triggered by a CloudWatch event rule (every 15 minutes by default). It syncs your AWS IAM Identity Center with your Google Workspace directory using their respective APIs.
During the first sync, the data of your Groups and Users is stored in an AWS S3 bucket as a [state file](docs/State-File-example.md). This state file is a custom implementation to save time and requests to the AWS SSO SCIM API, and to mitigate some of its limitations.
This project is developed using the [Go language](https://go.dev/) and [AWS SAM](https://docs.aws.amazon.com/serverless-application-model/latest/developerguide/sam-specification.html).
For more details on the resources created by the CloudFormation template, please check the [AWS SAM Template documentation](docs/AWS-SAM-Template.md).
> **Note:** If this is your first time implementing AWS IAM Identity Center, please read [Using SSO](docs/Using-SSO.md).
## 🚀 Getting Started
The easiest way to deploy and use this project is through the [AWS Serverless Application Repository](https://serverlessrepo.aws.amazon.com/applications/us-east-1/889836709304/idp-scim-sync).
### Credentials
You will need to configure credentials for both Google Workspace and AWS.
* **Google Workspace API Credentials**
* Follow the [Google Workspace documentation](https://developers.google.com/workspace/guides/create-credentials) to create credentials.
* You will need to create a **Service Account** and delegate **domain-wide authority** to it with the following scopes:
* `https://www.googleapis.com/auth/admin.directory.group.readonly`
* `https://www.googleapis.com/auth/admin.directory.user.readonly`
* `https://www.googleapis.com/auth/admin.directory.group.member.readonly`
* **AWS SSO SCIM API Credentials**
* Configure these credentials in the [AWS IAM Identity Center](https://aws.amazon.com/iam/identity-center/) service by following the [Automatic provisioning guide](https://docs.aws.amazon.com/singlesignon/latest/userguide/provision-automatically.html).
## 🛠️ Usage
You have several options to use this project:
### In AWS
* **AWS Serverless Application Repository (Recommended)**
* Deploy the application directly from the [AWS Serverless Application Repository](https://serverlessrepo.aws.amazon.com/applications/us-east-1/889836709304/idp-scim-sync).
* **AWS SAM**
* Build and deploy the Lambda function from your local machine.
* **Requirements:**
* [Git](https://git-scm.com/)
* [Go](https://go.dev/learn/)
* [AWS SAM CLI](https://docs.aws.amazon.com/serverless-application-model/latest/developerguide/serverless-sam-cli-install.html)
* **Commands:**
```bash
# Set your AWS CLI profile and region
export AWS_PROFILE=
export AWS_REGION=
# Validate the template
sam validate
# Build the project
sam build
# Deploy with a guided process
sam deploy --guided --capabilities CAPABILITY_IAM CAPABILITY_NAMED_IAM
```
### Locally
* **Build from Source**
* **Requirements:**
* [Git](https://git-scm.com/)
* [Go](https://go.dev/learn/)
* [Make](https://www.gnu.org/software/make/)
* **Commands:**
```bash
# Compile for your operating system
make
# Cross-compile for Windows, macOS, and Linux
make build-dist
```
* **Pre-built Binaries**
* Download the binaries from the [GitHub Releases](https://github.com/slashdevops/idp-scim-sync/releases).
* **Docker Image**
* Pull the image from one of the public repositories.
## 📦 Repositories
* 📦 [AWS Serverless Application Repository](https://serverlessrepo.aws.amazon.com/applications/us-east-1/889836709304/idp-scim-sync)
* 📦 [AWS ECR Public Gallery](https://gallery.ecr.aws/l2n7y5s7/slashdevops/idp-scim-sync)
* 📦 [GitHub Packages](https://github.com/slashdevops/idp-scim-sync/pkgs/container/idp-scim-sync)
* 📦 [Docker Hub](https://hub.docker.com/r/slashdevops/idp-scim-sync)
## ⚠️ Limitations
* **Group Limit**: The AWS SSO SCIM API has a limit of 50 groups per request. Please support the feature request on the [AWS Support site](https://repost.aws/questions/QUqqnVkIo_SYyF_SlX5LcUjg/aws-sso-scim-api-pagination-for-methods) to help get this limit increased.
* **Throttling**: With a large number of users and groups, you may encounter a `ThrottlingException` from the AWS SSO SCIM API. This project uses a [retryable HTTP client](https://github.com/hashicorp/go-retryablehttp) to mitigate this, but it's still a possibility.
* **User Status**: The Google Workspace API doesn't differentiate between normal and guest users except for their status. This project only syncs `ACTIVE` users.
## For `ssosync` Users
If you are coming from the [awslabs/ssosync](https://github.com/awslabs/ssosync) project, please note the following:
* This project only implements the `--sync-method groups`.
* This project only implements filtering for Google Workspace Groups, not Users.
* The flag names are different.
* Not all features of `ssosync` are implemented here, and they may not be in the future.
## 🧩 Components
* **idpscim**: A program for keeping AWS IAM Identity Center groups and users synced with your Google Workspace directory. See the [idpscim documentation](docs/idpscim.md) for more details.
* **idpscimcli**: A command-line tool to check and validate some of the functionalities implemented in `idpscim`. See the [idpscimcli documentation](docs/idpscimcli.md) for more details.
## 📄 License
This project is released under the Apache License 2.0. See the [LICENSE](LICENSE) file for more details.