https://github.com/supersjgk/data-analysis-dns-over-https
A Data Analytics + ML project to classify Benign and Malicious DNS-over-HTTPS traffic
https://github.com/supersjgk/data-analysis-dns-over-https
classification-model data-analysis data-analysis-python data-analytics datamining decision-trees dns dns-over-https doh gradient-boosting knn machine-learning random-forest
Last synced: 12 months ago
JSON representation
A Data Analytics + ML project to classify Benign and Malicious DNS-over-HTTPS traffic
- Host: GitHub
- URL: https://github.com/supersjgk/data-analysis-dns-over-https
- Owner: supersjgk
- Created: 2021-11-12T09:15:29.000Z (over 4 years ago)
- Default Branch: main
- Last Pushed: 2023-04-24T17:00:22.000Z (almost 3 years ago)
- Last Synced: 2025-01-25T04:46:03.369Z (about 1 year ago)
- Topics: classification-model, data-analysis, data-analysis-python, data-analytics, datamining, decision-trees, dns, dns-over-https, doh, gradient-boosting, knn, machine-learning, random-forest
- Language: Jupyter Notebook
- Homepage:
- Size: 74.2 KB
- Stars: 1
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
The main objective of this project is to deploy DoH within an application and capture benign as well as malicious DoH traffic as a two-layered approach to detect and characterize DoH traffic using time-series classifier.
This project uses the following Machine Learning classification algorithms: Naive Bayes, KNN, Decision Tree, Random Forest, Gradient Boost.
The final dataset includes implementing DoH protocol within an application using five different browsers and tools and four servers to capture Benign-DoH, Malicious-DoH and non-DoH traffic. Layer 1 of the proposed two-layered approach is used to classify DoH traffic from non-DoH traffic and layer 2 is used to characterize Benign-Doh from Malicious-DoH traffic. The browsers and tools used to capture traffic include Google Chrome, Mozilla Firefox, dns2tcp, DNSCat2, and Iodine while the servers used to respond to DoH requests are AdGuard, Cloudflare, Google DNS, and Quad9.
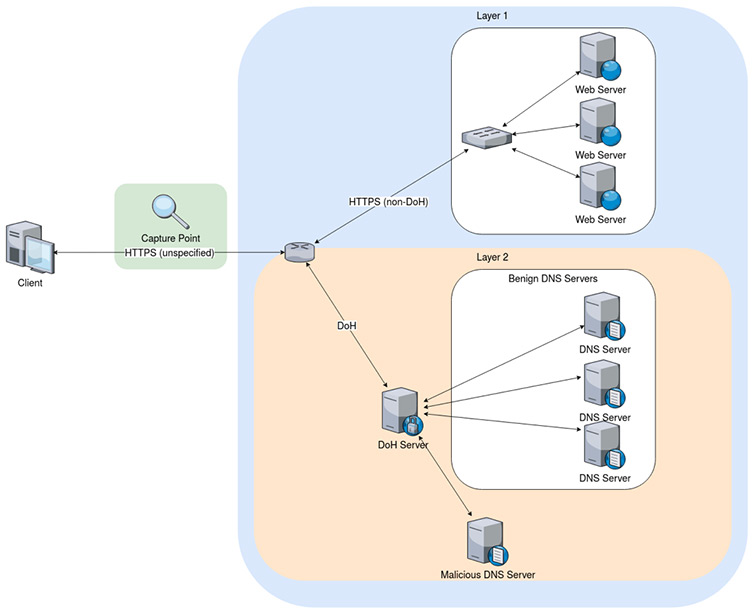
I have taken subsets of data from each of the five browsers and merged them into First layer data and Second layer data. If you want the whole dataset, go to: http://205.174.165.80/CICDataset/DoHBrw-2020/