https://github.com/sysdiglabs/aws-templates-secure-for-cloud
Deploy Sysdig Secure for cloud with AWS Cloudformation
https://github.com/sysdiglabs/aws-templates-secure-for-cloud
aws cloudformation image-scanning
Last synced: 7 months ago
JSON representation
Deploy Sysdig Secure for cloud with AWS Cloudformation
- Host: GitHub
- URL: https://github.com/sysdiglabs/aws-templates-secure-for-cloud
- Owner: sysdiglabs
- Created: 2020-10-19T15:19:42.000Z (over 5 years ago)
- Default Branch: main
- Last Pushed: 2024-09-12T16:02:49.000Z (over 1 year ago)
- Last Synced: 2024-09-13T05:00:16.463Z (over 1 year ago)
- Topics: aws, cloudformation, image-scanning
- Language: Makefile
- Homepage: https://docs.sysdig.com/en/docs/installation/sysdig-secure-for-cloud/deploy-sysdig-secure-for-cloud-on-aws/#onboarding-a-single-account-using-a-cft
- Size: 351 KB
- Stars: 4
- Watchers: 14
- Forks: 1
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- Codeowners: CODEOWNERS
Awesome Lists containing this project
README
# Sysdig Secure for Cloud in AWS - Cloudformation Templates
This repository contains the CloudFormation templates to deploy [Sysdig Secure for Cloud](https://docs.sysdig.com/en/docs/sysdig-secure/sysdig-secure-for-cloud/) suite.
## Features
Provides unified threat-detection, compliance, forensics and analysis through these major components:
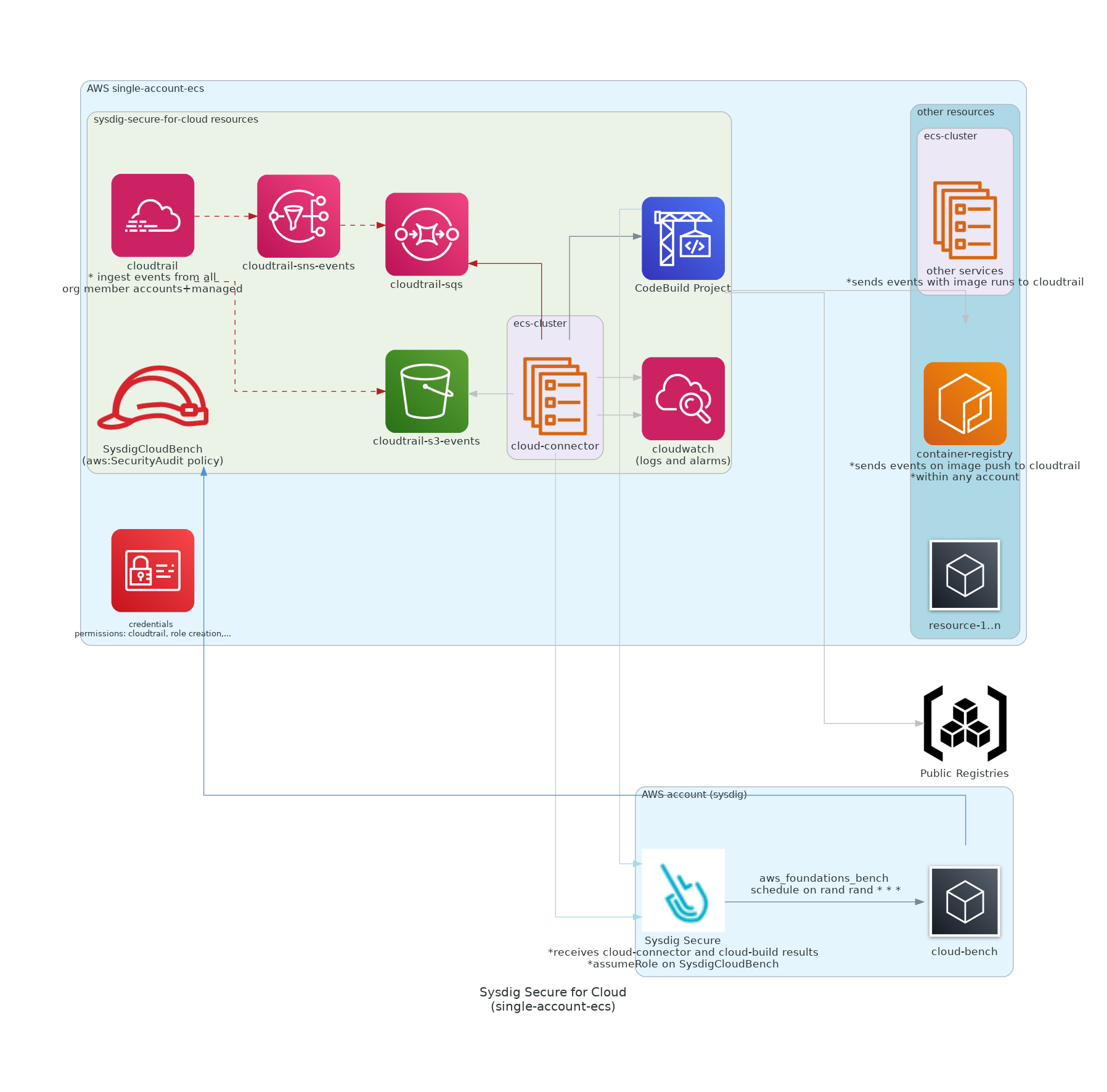
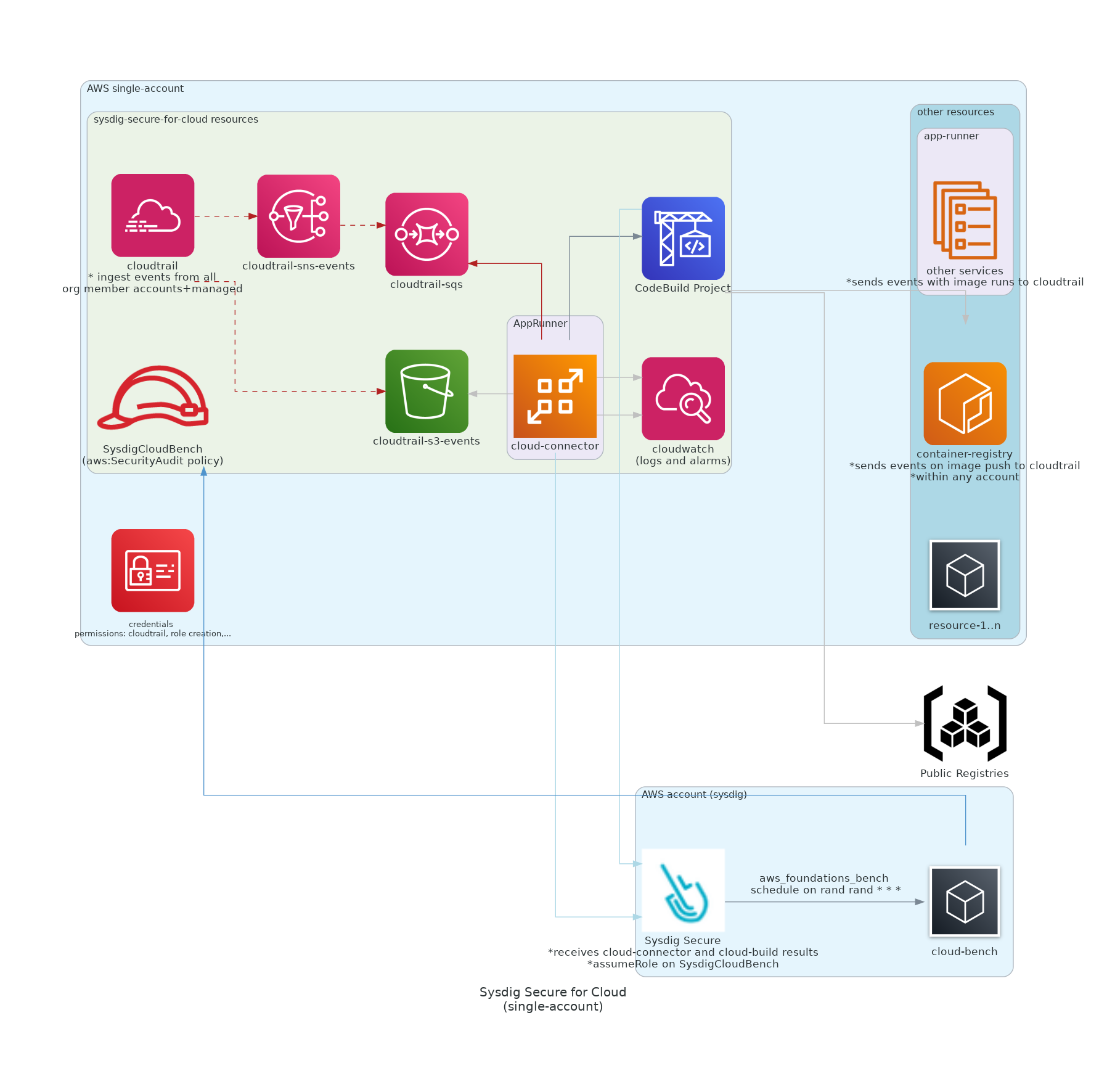
* **[Threat Detection](https://docs.sysdig.com/en/docs/sysdig-secure/insights/)**: Tracks abnormal and suspicious activities in your cloud environment based on Falco language. Managed through `cloud-connector` module.
* **[Compliance](https://docs.sysdig.com/en/docs/sysdig-secure/posture/compliance/compliance-unified-/)**: Enables the evaluation of standard compliance frameworks. Requires both modules `cloud-connector` and `cloud-bench`.
* **[Identity and Access Management](https://docs.sysdig.com/en/docs/sysdig-secure/posture/identity-and-access/)**: Analyses user access overly permissive policies. Requires both modules `cloud-connector` and `cloud-bench`.
* **[Image Scanning](https://docs.sysdig.com/en/docs/sysdig-secure/scanning/)**: Automatically scans all container images pushed to the registry (ECR) and the images that run on the AWS workload (currently ECS). Managed through `cloud-connector`.
Disabled by Default, can be enabled through `deploy_image_scanning_ecr` and `deploy_image_scanning_ecs` input variable parameters.
For Terraform flavor, check [Secure for cloud - Terraform](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/)
## UseCases
If you're unsure about what/how to use this module, please fill the [questionnaire](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/blob/master/use-cases/_questionnaire.md) report as an issue and let us know your context, we will be happy to help and improve our module.
### Single-Account
Deploy the latest versions using one of the workloads that most suit you:
#### ECS-based workload
[Template for ECS workload](https://console.aws.amazon.com/cloudformation/home#/stacks/quickCreate?stackName=Sysdig-CloudVision&templateURL=https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/ecs/latest/entry-point.yaml)
#### AppRunner-based workload
Less resource-demanding and economic deployment (ECS requires VPCs and Gateways), but Apprunner is not available on all regions yet
[Template for AppRunner workload](https://console.aws.amazon.com/cloudformation/home#/stacks/quickCreate?stackName=Sysdig-CloudVision&templateURL=https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/apprunner/latest/entry-point.yaml)
If needed, we also have an Sysdig Secure for Cloud Terraform version
## Organizational
No official cloudformation templates available yet.
If Terraform is not desired, you can approach the installation through the `manual` setup, following the so prefixed
extra [use-cases](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/tree/master/use-cases)
---
## Authors
Module is maintained and supported by [Sysdig](https://sysdig.com).
## License
Apache 2 Licensed. See LICENSE for full details.