https://github.com/t3l3machus/synergy-httpx
A Python http(s) server designed to assist in red teaming activities such as receiving intercepted data via POST requests and serving content dynamically (e.g. payloads).
https://github.com/t3l3machus/synergy-httpx
arduino attiny85 hacking hacking-tools offensive-security penetration-testing-tools pentesting red-teaming redteam t3l3machus
Last synced: 8 months ago
JSON representation
A Python http(s) server designed to assist in red teaming activities such as receiving intercepted data via POST requests and serving content dynamically (e.g. payloads).
- Host: GitHub
- URL: https://github.com/t3l3machus/synergy-httpx
- Owner: t3l3machus
- License: bsd-2-clause
- Created: 2023-06-02T10:06:41.000Z (over 2 years ago)
- Default Branch: main
- Last Pushed: 2024-07-19T06:40:59.000Z (over 1 year ago)
- Last Synced: 2025-03-25T21:08:45.573Z (8 months ago)
- Topics: arduino, attiny85, hacking, hacking-tools, offensive-security, penetration-testing-tools, pentesting, red-teaming, redteam, t3l3machus
- Language: Python
- Homepage:
- Size: 83 KB
- Stars: 129
- Watchers: 2
- Forks: 17
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE.md
Awesome Lists containing this project
README
# Synergy Httpx
[](https://www.python.org/)

[](https://github.com/t3l3machus/Synergy-httpx/blob/main/LICENSE.md)

## Purpose
A Python http(s) server designed to assist in red teaming activities such as receiving intercepted data via POST requests and serving content dynamically (e.g. payloads).
I find this tool handy when performing USB-based attacks during physical pentests (Rubber ducky / BadUSB / ATtiny85, etc). Check out the `ATtiny85_templates` folder for some handy `.ino` templates to load on your microcontrollers. Credits: My templates are inspired by this repo -> [CedArctic/DigiSpark-Scripts](https://github.com/CedArctic/DigiSpark-Scripts/).
🎥 [How to turn your ATtiny85 into a rubber ducky ](https://www.youtube.com/watch?v=1l5UlG_R_Fc)
## Preview
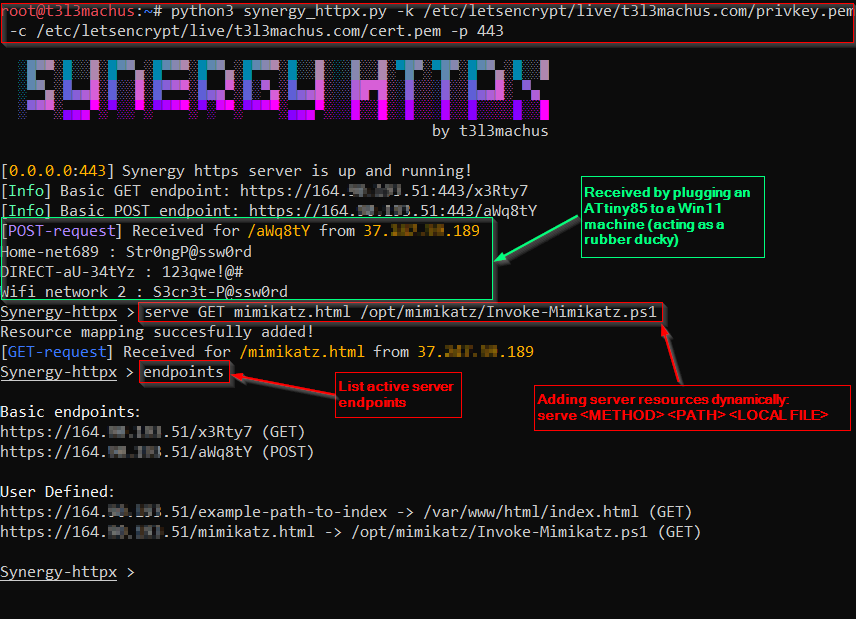
## Installation
This tool was explicitly developed and tested on kali linux. I doubt it will work properly on Windows.
```
pip3 install -r requirements.txt
```
## Usage
```
python3 synergy_httpx.py [-h] [-c CERT] [-k KEY] [-p PORT] [-q] [-i INTERFACE]
```
- If you provide cert.pem and key.pem files when you execute `synergy_httpx.py`, the server will run with SSL (https).
- You can use the "serve" and "release" prompt commands to associate/disassociate server path names with local files to be used as a response body to GET/POST requests, while the server is running. There are two standard hardcoded endpoints, 1 x GET mainly for connectivity tests and 1 x POST that will print the request body to the stdout, useful for intercepting data and sending them to your server via http(s).
- You can predifine endpoints (server paths mapped to local files) by editting the `user_defined_endpoints` dict in `synergy_httpx.py` (there are examples).
- Use the "endpoints" prompt command to list all of the server's active endpoints.