https://github.com/tenable/router_badusb
BadUSB in Routers
https://github.com/tenable/router_badusb
asus badusb bsides bsidesdublin man-in-the-middle mikrotik router
Last synced: 9 months ago
JSON representation
BadUSB in Routers
- Host: GitHub
- URL: https://github.com/tenable/router_badusb
- Owner: tenable
- Archived: true
- Created: 2019-03-12T11:59:58.000Z (almost 7 years ago)
- Default Branch: master
- Last Pushed: 2022-11-29T20:04:15.000Z (about 3 years ago)
- Last Synced: 2024-10-29T17:55:29.417Z (about 1 year ago)
- Topics: asus, badusb, bsides, bsidesdublin, man-in-the-middle, mikrotik, router
- Language: Shell
- Homepage:
- Size: 7.03 MB
- Stars: 189
- Watchers: 26
- Forks: 35
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- Codeowners: .github/CODEOWNERS
Awesome Lists containing this project
- awesome-rainmana - tenable/router_badusb - BadUSB in Routers (Shell)
README
# BadUSB in Routers
Material found in this repository was originally presented at [BSides Dublin](https://www.bsidesdub.ie/) on March 23, 2019. The slides are included here in pdf format.
This repository contains configuration files for [P4wnP1](https://github.com/mame82/P4wnP1), a BadUSB framework for the Raspberry Pi. The configuration files allow an attacker to execute BadUSB style attacks on certain routers.
The following hardware and software were used for the BadUSB attacks:
* Raspberry Pi Zero
* USB-A Addon
* 8 GB microSD
* Raspbian Stretch (Version: November 2018)
* P4wnP1 (Version: [9c8cc09a6503f10309c04310c3bba9c07caab8b7](https://github.com/mame82/P4wnP1/tree/9c8cc09a6503f10309c04310c3bba9c07caab8b7))

---
## mikrotik_mitm

The mikrotik_mitm directory contains configuration files to man-in-the-middle outbound traffic from RouterOS LAN hosts. The configuration files were tested using RouterOS on an hAP using default configurations on 6.44.1 Stable. Presumably, it works on any RouterOS based router that supports 4g USB functionality. The attack will cause all internet bound traffic to be routed to the Raspberry Pi plugged into the USB port. The Pi will forward all of the internet traffic to a remote VPN server.
*PoC Video:*
[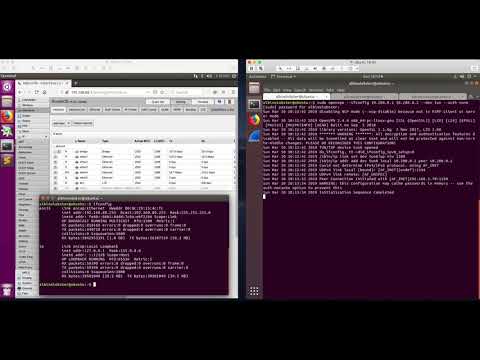](http://www.youtube.com/watch?v=3X7xrgan5Tk)
As written the "remote" VPN server is at 192.168.1.64. If you are going to try this out for yourself, you'll need to adjust the openvpn connection and possibly the iptables / dhcp options depending on where your VPN server is. The VPN server configuration is fairly simple:
```sh
sudo sysctl -w net.ipv4.ip_forward=1
sudo openvpn --ifconfig 10.200.0.1 10.200.0.2 --dev tun --auth none
sudo iptables -I FORWARD -i tun0 -j ACCEPT
sudo iptables -I FORWARD -i tun0 -o ACCEPT
sudo iptables -t nat -A POSTROUTING -j MASQUERADE
```

As mentioned, RouterOS will recognize the USB device using the default configuration. However! For some reason, the router won't recognize the Pi until you first plug in something else. You only have to do it once and then you are good until the router reboots. I'm not sure of the root cause of this. I've been using this ethernet adapter (you can find it on Amazon):

---
## mikrotik_wan_lan_access
This is a non-mitm version of the MikroTik attack. The Pi will be assigned 192.168.4.1 and it should have access to both the WAN and LAN. LAN devices should also be able to reach the Pi. This is kind of useful if you just want to plug in your Pi as some type of local server... or if you want a reverse shell out to the internet.
---
## asus_bsides_routing_table

The asus_bsides_routing_table directory contains configuration files to hijack traffic bound for http://securitybsides.com. The attack relies on the ability of the USB WAN to insert arbitrary entries into the router's routing table via DHCP options.
This attack was tested against an Asus RT-AC51U with load balancing dual WAN configured.
*PoC Video:*
[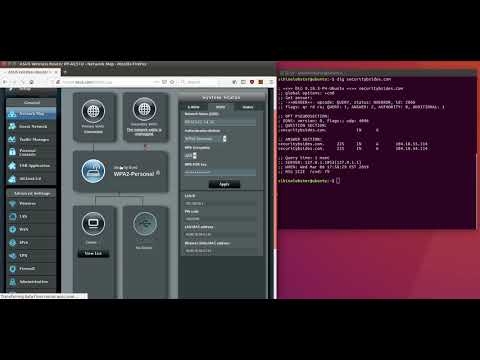](http://www.youtube.com/watch?v=LvWo8fUaJdo)
---
## Traditional Attacks over IP

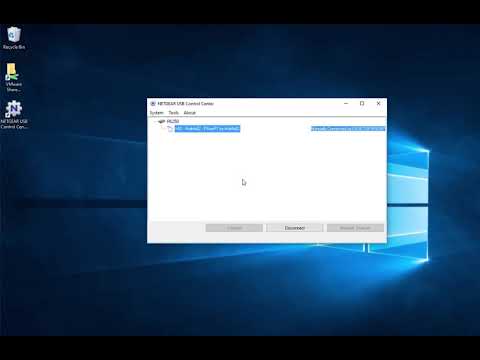
A variety of routers support printer sharing (Netgear, Linksys, and TP-Link). The way this works is that you plug your USB printer into the router and then you install client software on your LAN host which gives it the ability to talk to the printer via the router.
I've found that the router/client software will actually communicate with pretty much any USB device. For whatever reason, the device makers didn't limit the functionality to printers only.
As such, an attacker can execute any of the normal payloads that come with P4wnP1. In my PoC video, I'm using hid_keyboard2.txt. The downside to this attack is that it requires special software be installed and that the user actually click "connect".
*PoC Video:*
[](http://www.youtube.com/watch?v=aoaB6hiHGiM)