https://github.com/the-robot/sqliv
massive SQL injection vulnerability scanner
https://github.com/the-robot/sqliv
crawler multiprocessing reverse-ip-scan scanner scanning sql-injection sqli sqli-vulnerability-scanner
Last synced: 11 months ago
JSON representation
massive SQL injection vulnerability scanner
- Host: GitHub
- URL: https://github.com/the-robot/sqliv
- Owner: the-robot
- License: gpl-3.0
- Archived: true
- Created: 2015-06-11T16:04:41.000Z (over 10 years ago)
- Default Branch: master
- Last Pushed: 2018-08-14T11:28:52.000Z (over 7 years ago)
- Last Synced: 2024-10-28T21:39:53.888Z (over 1 year ago)
- Topics: crawler, multiprocessing, reverse-ip-scan, scanner, scanning, sql-injection, sqli, sqli-vulnerability-scanner
- Language: Python
- Homepage: https://en.kali.tools/all/?tool=1334
- Size: 872 KB
- Stars: 1,158
- Watchers: 63
- Forks: 376
- Open Issues: 18
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-bbht - sqliv - massive SQL injection vulnerability scanner (Exploitation / SQLi)
- awesome-bugbounty-tools - sqliv - massive SQL injection vulnerability scanner (Exploitation / SQL Injection)
- WebHackersWeapons - sqliv - robot/sqliv?label=%20)|[`sqli`](/categorize/tags/sqli.md)|[](/categorize/langs/Python.md)| (Weapons / Tools)
- awesome-termux-hacking - sqliv - massive SQL injection vulnerability scanner.[](https://github.com/the-robot/sqliv/stargazers/) (Uncategorized / Uncategorized)
- awesome-bbht - sqliv - massive SQL injection vulnerability scanner (Exploitation / SQLi)
README
SQLiv
===
### Massive SQL injection scanner
**Features**
1. multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo
2. targetted scanning by providing specific domain (with crawling)
3. reverse domain scanning
> both SQLi scanning and domain info checking are done in multiprocessing
> so the script is super fast at scanning many urls
> quick tutorial & screenshots are shown at the bottom
> project contribution tips at the bottom
---
**Installation**
1. git clone https://github.com/the-robot/sqliv.git
2. sudo python2 setup.py -i
> Dependencies
> - [bs4](https://pypi.python.org/pypi/bs4)
> - [termcolor](https://pypi.python.org/pypi/termcolor)
> - [google](https://pypi.python.org/pypi/google)
> - [nyawc](https://pypi.python.org/pypi/nyawc/)
**Pre-installed Systems**
- [BlackArch Linux](https://blackarch.org/scanner.html) 
---
### Quick Tutorial
**1. Multiple domain scanning with SQLi dork**
- it simply search multiple websites from given dork and scan the results one by one
```python
python sqliv.py -d -e
python sqliv.py -d "inurl:index.php?id=" -e google
```
**2. Targetted scanning**
- can provide only domain name or specifc url with query params
- if only domain name is provided, it will crawl and get urls with query
- then scan the urls one by one
```python
python sqliv.py -t
python sqliv.py -t www.example.com
python sqliv.py -t www.example.com/index.php?id=1
```
**3. Reverse domain and scanning**
- do reverse domain and look for websites that hosted on same server as target url
```python
python sqliv.py -t -r
```
**4. Dumping scanned result**
- you can dump the scanned results as json by giving this argument
```python
python sqliv.py -d -e -o result.json
```
**View help**
```python
python sqliv.py --help
usage: sqliv.py [-h] [-d D] [-e E] [-p P] [-t T] [-r]
optional arguments:
-h, --help show this help message and exit
-d D SQL injection dork
-e E search engine [Google only for now]
-p P number of websites to look for in search engine
-t T scan target website
-r reverse domain
```
---
### screenshots
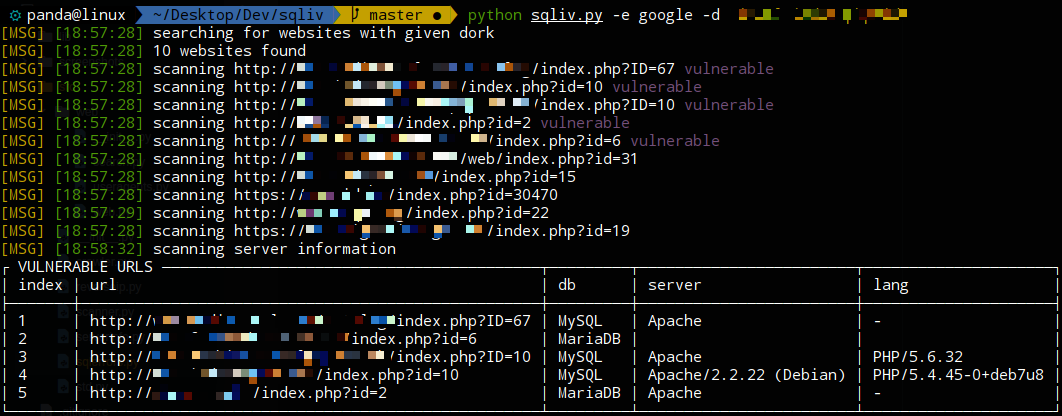
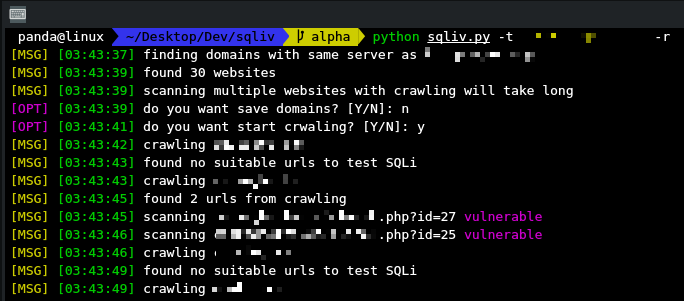
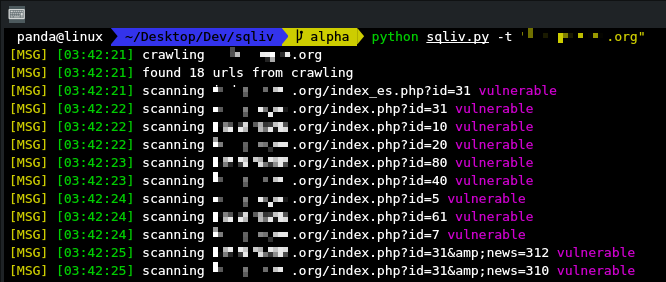
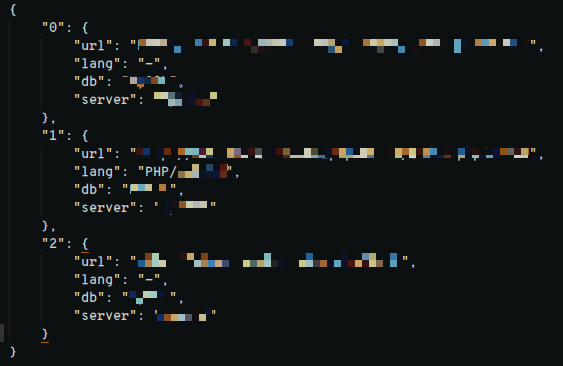
---
### Development
**TODO**
1. POST form SQLi vulnerability testing