https://github.com/ucybers/bug-bounty-beginner-roadmap
This is a resource for anyone looking to learn bug hunting and provides guidance during the study and learning phase.
https://github.com/ucybers/bug-bounty-beginner-roadmap
bug bug-bounty bugbounty bugbounty-tool bugs cmd cmdline cyber-security cybersecurity cybersecurity-tool guide hacker linux linux-shell powershell roadmap tutorial tutorials windows
Last synced: about 2 months ago
JSON representation
This is a resource for anyone looking to learn bug hunting and provides guidance during the study and learning phase.
- Host: GitHub
- URL: https://github.com/ucybers/bug-bounty-beginner-roadmap
- Owner: UCYBERS
- License: gpl-3.0
- Created: 2024-08-01T11:18:29.000Z (10 months ago)
- Default Branch: main
- Last Pushed: 2024-08-01T22:13:10.000Z (10 months ago)
- Last Synced: 2025-03-24T10:38:53.541Z (2 months ago)
- Topics: bug, bug-bounty, bugbounty, bugbounty-tool, bugs, cmd, cmdline, cyber-security, cybersecurity, cybersecurity-tool, guide, hacker, linux, linux-shell, powershell, roadmap, tutorial, tutorials, windows
- Homepage: https://ucybers.com/
- Size: 126 KB
- Stars: 26
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
# Bug-Bounty-Beginner-Roadmap
This is a resource for anyone looking to learn bug hunting and provides guidance during the study and learning phase.
Feel free to contribute to this repository!
# Bug Bounty Beginner's Roadmap
Hello! I'm **DARK**. I work as a Network and Information Security Engineer and Ethical Hacker. I've created this repository for everyone to contribute to, aiming to guide young and enthusiastic individuals in starting their careers in bug bounty. More content will be added regularly, so keep following along. Let's get started!
***NOTE:*** The bug bounty landscape has evolved significantly over the past few years. Issues that were easy to find a year ago are now much more challenging. Automation is widely used, and most of the "low-hanging fruit" are often duplicated if you're unlucky. If you want to start in bug bounty, you need to be determined, consistent, and focused, as the competition is very intense.
# Introduction
- **What is a bug?**
- A security bug or vulnerability is a weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, negatively impacts confidentiality, integrity, or availability.
- **What is Bug Bounty?**
- A bug bounty, or bug bounty program, is IT jargon for a reward program offered for finding and reporting bugs in a particular software product. Many IT companies offer bug bounties to drive product improvement and increase interaction from end users or clients. Companies with bug bounty programs may receive hundreds of bug reports, including security bugs and vulnerabilities, with many reporters standing to receive awards.
- **What is the Reward?**
- Rewards vary based on the severity of the issue and the cost to fix it. They can range from real money (most common) to premium subscriptions (e.g., Prime, Netflix), discount coupons (for e-commerce or shopping sites), gift vouchers, and swags (apparel, badges, customized stationery, etc.). Monetary rewards can range from $50 to $50,000 or even more.
# What to learn?
- **Technical**
- **Computer Fundamentals**
- https://www.comptia.org/training/by-certification/a
- https://youtu.be/y2kg3MOk1sY?si=UARPFFqJLnN7_U3H
- https://www.tutorialspoint.com/computer_fundamentals/index.htm
- https://www.geeksforgeeks.org/computer-fundamentals-tutorial/
- https://www.udemy.com/course/computer-fundamentals-u/
- https://www.coursera.org/courses?query=computer%20fundamentals
- **Computer Networking**
- https://youtube.com/playlist?list=PLDQaRcbiSnqF5U8ffMgZzS7fq1rHUI3Q8&si=oVf5e0eg5Lh8_Gv2
- https://www.youtube.com/watch?v=qiQR5rTSshw
- https://youtube.com/playlist?list=PLG49S3nxzAnlCJiCrOYuRYb6cne864a7G&si=um2E56jRrlrD_aI6
- https://www.udacity.com/course/computer-networking--ud436
- https://www.coursera.org/professional-certificates/google-it-support
- https://www.udemy.com/course/introduction-to-computer-networks/
- **Operating Systems**
- https://www.youtube.com/watch?v=z2r-p7xc7c4
- https://youtu.be/sWbUDq4S6Y8?si=PxHxzDTbj_JCpGGm
- https://www.coursera.org/learn/os-power-user
- https://www.udacity.com/course/introduction-to-operating-systems--ud923
- https://www.udemy.com/course/linux-command-line-volume1/
- https://youtu.be/ROjZy1WbCIA?si=5WyHmKyD9xLHeQF6
- **Command Line**
- **Windows:**
- https://youtu.be/Jfvg3CS1X3A?si=P54O2otUu3BuodEp
- https://youtu.be/qnXe1gecux8?si=zSkPIdA28hfVbr3-
- https://www.youtube.com/watch?v=UVUd9_k9C6A
- **Linux:**
- https://youtube.com/playlist?list=PLS1QulWo1RIb9WVQGJ_vh-RQusbZgO_As&si=lrSOP47nwRV-63_0
- https://youtu.be/gd7BXuUQ91w?si=oQD3y4zzYUecoyfu
- https://youtu.be/ZtqBQ68cfJc?si=MdPu18--CktQYuVK
- https://www.youtube.com/watch?v=2PGnYjbYuUo
- https://youtube.com/playlist?list=PLT98CRl2KxKHaKA9-4_I38sLzK134p4GJ&si=rqeEYTu9jHPwN_Oj
- https://youtu.be/WMy3OzvBWc0?si=ps_aF5AZ4fRGYec-
- **Programming**
- **C**
- https://youtu.be/87SH2Cn0s9A?si=89Mec5YZBGXKcKsG
- https://academy.ucybers.com/p/c-programming-for-hacking
- https://youtu.be/KJgsSFOSQv0?si=9bstBmoBB-k8Cg_-
- https://www.programiz.com/c-programming
- **Python**
- https://youtu.be/kqtD5dpn9C8?si=HR9wQ9c4as3N9J_N
- https://youtu.be/_uQrJ0TkZlc?si=FSHrjCFfN4-DJXL4
- https://youtu.be/rfscVS0vtbw?si=tjSgCK9Xup7aZU-o
- **JavaScript**
- https://youtu.be/W6NZfCO5SIk?si=AsWBI_naaiA7Eeya
- https://youtu.be/PkZNo7MFNFg?si=x6GeqMwW_e3Pnmfa
- https://www.youtube.com/watch?v=jS4aFq5-91M
- **PHP**
- https://youtu.be/OK_JCtrrv-c?si=_UYoV__q_ghOyZDJ
- https://youtube.com/playlist?list=PL0eyrZgxdwhwwQQZA79OzYwl5ewA7HQih&si=8F4HPw0mKvMRJTwg
- https://youtu.be/xcg9qq6SZ0w?si=dDE56ihKGe7vu49D
# Where to learn from?
- **Books**
- Web Application Hacker's Handbook: https://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470
- Real World Bug Hunting: https://www.amazon.in/Real-World-Bug-Hunting-Field-Hacking-ebook/dp/B072SQZ2LG
- Bug Bounty Hunting Essentials: https://www.amazon.in/Bug-Bounty-Hunting-Essentials-Quick-paced-ebook/dp/B079RM344H
- Bug Bounty Bootcamp: https://www.amazon.in/Bug-Bounty-Bootcamp-Reporting-Vulnerabilities-ebook/dp/B08YK368Y3
- Hands on Bug Hunting: https://www.amazon.in/Hands-Bug-Hunting-Penetration-Testers-ebook/dp/B07DTF2VL6
- Hacker's Playbook 3: https://www.amazon.in/Hacker-Playbook-Practical-Penetration-Testing/dp/1980901759
- OWASP Testing Guide: https://www.owasp.org/index.php/OWASP_Testing_Project
- Web Hacking 101: https://www.pdfdrive.com/web-hacking-101-e26570613.html
- OWASP Mobile Testing Guide :https://www.owasp.org/index.php/OWASP_Mobile_Security_Testing_Guide
- **Writeups**
- Medium: https://medium.com/analytics-vidhya/a-beginners-guide-to-cyber-security-3d0f7891c93a
- Infosec Writeups: https://infosecwriteups.com/?gi=3149891cc73d
- Hackerone Hacktivity: https://hackerone.com/hacktivity
- Google VRP Writeups: https://github.com/xdavidhu/awesome-google-vrp-writeups
- UCYBERS: https://ucybers.com/
- **Blogs and Articles**
- Hacking Articles: https://www.hackingarticles.in/
- Vickie Li Blogs: https://vickieli.dev/
- UCYBERS Blogs: https://ucybers.com/blog/
- Bugcrowd Blogs: https://www.bugcrowd.com/blog/
- Intigriti Blogs: https://blog.intigriti.com/
- Portswigger Blogs: https://portswigger.net/blog
- **Forums**
- Reddit: https://www.reddit.com/r/websecurity/
- Reddit: https://www.reddit.com/r/netsec/
- Bugcrowd Discord: https://discord.com/invite/TWr3Brs
- UCYBERS Discord: https://discord.com/invite/Y3s4s4E7
- **Official Websites**
- UCYBERS: https://ucybers.com/
- OWASP: https://owasp.org/
- PortSwigger: https://portswigger.net/
- Cloudflare: https://www.cloudflare.com/
- **YouTube Channels**
- **English**
- Insider PHD: https://www.youtube.com/c/InsiderPhD
- Stok: https://www.youtube.com/c/STOKfredrik
- Bug Bounty Reports Explained: https://www.youtube.com/c/BugBountyReportsExplained
- Vickie Li: https://www.youtube.com/c/VickieLiDev
- Hacking Simplified: https://www.youtube.com/c/HackingSimplifiedAS
- Pwn function :https://www.youtube.com/c/PwnFunction
- Farah Hawa: https://www.youtube.com/c/FarahHawa
- XSSRat: https://www.youtube.com/c/TheXSSrat
- Zwink: https://www.youtube.com/channel/UCDl4jpAVAezUdzsDBDDTGsQ
- Live Overflow :https://www.youtube.com/c/LiveOverflow
- **Arabic**
- UCYBERS: https://youtube.com/@ucybers
## Join Twitter Today!
World class security researchers and bug bounty hunters are on Twitter. Where are you? Join Twitter now and get daily updates on new issues, vulnerabilities, zero days, exploits, and join people sharing their methodologies, resources, notes and experiences in the cyber security world!
- UCYBERS Twitter: https://x.com/UCybersX
## PRACTICE! PRACTICE! and PRACTICE!
- **CTF**
- Hacker 101: https://www.hackerone.com/hackers/hacker101
- PicoCTF: https://picoctf.org/
- TryHackMe: https://tryhackme.com/ (premium/free)
- HackTheBox: https://www.hackthebox.com/ (premium)
- VulnHub: https://www.vulnhub.com/
- HackThisSite: https://hackthissite.org/
- CTFChallenge: https://ctfchallenge.co.uk/
- PentesterLab: https://pentesterlab.com/referral/olaL4k8btE8wqA (premium)
- **Online Labs**
- PortSwigger Web Security Academy: https://portswigger.net/web-security
- OWASP Juice Shop: https://owasp.org/www-project-juice-shop/
- XSSGame: https://xss-game.appspot.com/
- BugBountyHunter: https://www.bugbountyhunter.com/ (premium)
- W3Challs : https://w3challs.com/
- **Offline Labs**
- DVWA: https://dvwa.co.uk/
- bWAPP: http://www.itsecgames.com/
- Metasploitable2: https://sourceforge.net/projects/metasploitable/files/Metasploitable2/
- BugBountyHunter: https://www.bugbountyhunter.com/ (premium)
- W3Challs : https://w3challs.com/
### More Tools and Services To use
- **Servers**
- [Shodan](https://shodan.io) - Search Engine for the Internet of Everything
- [Censys Search](https://search.censys.io/) - Search Engine for every server on the Internet to reduce exposure and improve security
- [Onyphe.io](https://www.onyphe.io/) - Cyber Defense Search Engine for open-source and cyber threat intelligence data
- [ZoomEye](https://www.zoomeye.org/) - Global cyberspace mapping
- [GreyNoise](https://viz.greynoise.io/) - The source for understanding internet noise
- [Natlas](https://natlas.io/) - Scaling Network Scanning
- [Netlas.io](https://netlas.io/) - Discover, Research and Monitor any Assets Available Online
- [FOFA](https://fofa.info/) - Cyberspace mapping
- [Quake](https://quake.360.net/quake/#/index) - Cyberspace surveying and mapping system
- [Hunter](https://hunter.how/) - Internet Search Engines For Security Researchers
### Vulnerabilities
- [NIST NVD](https://nvd.nist.gov/vuln/search) - US National Vulnerability Database
- [MITRE CVE](https://cve.mitre.org/cve/search_cve_list.html) - Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities
- [GitHub Advisory Database](https://github.com/advisories) - Security vulnerability database inclusive of CVEs and GitHub originated security advisories
- [cloudvulndb.org](https://www.cloudvulndb.org/) - The Open Cloud Vulnerability & Security Issue Database
- [osv.dev](https://osv.dev/list) - Open Source Vulnerabilities
- [Vulners.com](https://vulners.com/) - Your Search Engine for Security Intelligence
- [opencve.io](https://www.opencve.io/cve) - Easiest way to track CVE updates and be alerted about new vulnerabilities
- [security.snyk.io](https://security.snyk.io/) - Open Source Vulnerability Database
- [Mend Vulnerability Database](https://www.mend.io/vulnerability-database/) - The largest open source vulnerability DB
- [Rapid7 - DB](https://www.rapid7.com/db/) - Vulnerability & Exploit Database
- [CVEDetails](https://www.cvedetails.com/) - The ultimate security vulnerability datasource
- [VulnIQ](https://vulniq.com/) - Vulnerability intelligence and management solution
- [SynapsInt](https://synapsint.com/) - The unified OSINT research tool
- [Aqua Vulnerability Database](https://avd.aquasec.com/) - Vulnerabilities and weaknesses in open source applications and cloud native infrastructure
- [Vulmon](https://vulmon.com/) - Vulnerability and exploit search engine
- [VulDB](https://vuldb.com/) - Number one vulnerability database
- [ScanFactory](https://in.scanfactory.io/cvemon.html) - Realtime Security Monitoring
- [Trend Micro Zero Day Initiative](https://www.zerodayinitiative.com/advisories/published/) - Publicly disclosed vulnerabilities discovered by Zero Day Initiative researchers
- [Google Project Zero](https://bugs.chromium.org/p/project-zero/issues/list?can=1&q=&sort=-id&colspec=ID%20Type%20Status%20Priority%20Milestone%20Owner%20Summary) - Vulnerabilities including Zero Days
- [Trickest CVE Repository](https://github.com/trickest/cve) - Gather and update all available and newest CVEs with their PoC
- [cnvd.org.cn](https://www.cnvd.org.cn/) - Chinese National Vulnerability Database
- [InTheWild.io](https://inthewild.io/feed) - Check CVEs in our free, open source feed of exploited vulnerabilities
- [Vulnerability Lab](https://www.vulnerability-lab.com/) - Vulnerability research, bug bounties and vulnerability assessments
- [Red Hat Security Advisories](https://access.redhat.com/security/security-updates/) - Information about security flaws that affect Red Hat products and services in the form of security advisories
- [Cisco Security Advisories](https://sec.cloudapps.cisco.com/security/center/publicationListing.x) - Security advisories and vulnerability information for Cisco products, including network equipment and software
- [Microsoft Security Response Center](https://msrc.microsoft.com/update-guide/en-us) - Reports of security vulnerabilities affecting Microsoft products and services
- [VARIoT](https://www.variotdbs.pl/vulns/) - VARIoT IoT Vulnerabilities Database
### Exploits
- [Exploit-DB](https://www.exploit-db.com/) - Exploit Database
- [Sploitus](https://sploitus.com/) - Convenient central place for identifying the newest exploits
- [Rapid7 - DB](https://www.rapid7.com/db/) - Vulnerability & Exploit Database
- [Vulmon](https://vulmon.com/) - Vulnerability and exploit search engine
- [packetstormsecurity.com](https://packetstormsecurity.com/) - Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers
- [0day.today](https://0day.today/) - Ultimate database of exploits and vulnerabilities
- [LOLBAS](https://lolbas-project.github.io/) - Living Off The Land Binaries, Scripts and Libraries
- [GTFOBins](https://gtfobins.github.io/) - Curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems
- [Payloads All The Things](https://swisskyrepo.github.io/PayloadsAllTheThingsWeb/) - A list of useful payloads and bypasses for Web Application Security
- [XSS Payloads](http://www.xss-payloads.com/) - The wonderland of JavaScript unexpected usages, and more
- [exploitalert.com](https://www.exploitalert.com/search-results.html) - Database of Exploits
- [Reverse Shell generator](https://www.revshells.com/) - Online Reverse Shell generator with Local Storage functionality, URI & Base64 Encoding, MSFVenom Generator, and Raw Mode
- [HackerOne hacktivity](https://hackerone.com/hacktivity) - See the latest hacker activity on HackerOne
- [Bugcrowd Crowdstream](https://bugcrowd.com/crowdstream) - Showcase of accepted and disclosed submissions on Bugcrowd programs
- [GTFOArgs](https://gtfoargs.github.io/) - Curated list of Unix binaries that can be manipulated for argument injection
- [shell-storm.org/shellcode](https://shell-storm.org/shellcode/index.html) - Shellcodes database for study cases
- [Hacking the Cloud](https://hackingthe.cloud/) - Encyclopedia of the attacks/tactics/techniques that offensive security professionals can use on their next cloud exploitation adventure
- [LOLDrivers](https://www.loldrivers.io/) - Open-source project that brings together vulnerable, malicious, and known malicious Windows drivers
- [PwnWiki](http://pwnwiki.io/) - Collection of TTPs (tools, tactics, and procedures) for what to do after access has been gained
- [CVExploits Search](https://cvexploits.io/) - Your comprehensive database for CVE exploits from across the internet
- [VARIoT](https://www.variotdbs.pl/exploits/) - VARIoT IoT exploits database
- [LOOBins](https://www.loobins.io/) - Detailed information on various built-in macOS binaries and how they can be used by threat actors for malicious purposes
- [Coalition Exploit Scoring System](https://ess.coalitioninc.com/) - Model that dynamically scores new and existing vulnerabilities to reflect their exploit likelihood
- [WADComs](https://wadcoms.github.io/) - Interactive cheat sheet containing a curated list of offensive security tools and their respective commands to be used against Windows/AD environments
- [LOLAPPS](https://lolapps-project.github.io/) - Compendium of applications that can be used to carry out day-to-day exploitation
- [Living off the Hardware](https://lothardware.com.tr/) - Resource collection that provides guidance on identifying and utilizing malicious hardware and malicious devices
- [Living Off the Pipeline](https://boostsecurityio.github.io/lotp/) - How development tools commonly used in CI/CD pipelines can be used to achieve arbitrary code execution
# Bug Bounty Platforms
- **Crowdsourcing**
- Bugcrowd: https://www.bugcrowd.com/
- Hackerone: https://www.hackerone.com/
- Intigriti: https://www.intigriti.com/
- YesWeHack: https://www.yeswehack.com/
- OpenBugBounty: https://www.openbugbounty.org/
- **Individual** **Programs**
- Meta: https://www.facebook.com/whitehat
- Google: https://about.google/appsecurity/
# Bug Bounty Report Format
- **Title**
- The first impression is the last impression, the security engineer
looks at the title first and he should be able to identify the issue.
- Write about what kind of functionality you can able to abuse or what kind
of protection you can bypass. Write in just one line.
- Include the Impact of the issue in the title if possible.
- **Description**
- This component provides details of the vulnerability, you can explain the vulnerability here, write about the paths, endpoints, error messages you got while testing. You can also attach HTTP requests, vulnerable source code.
- **Steps to Reproduce**
- Write the stepwise process to recreate the bug. It is important for an app owner to be able to verify what you've found and understand the scenario.
- You must write each step clearly in-order to demonstrate the issue. that helps security engineers to triage fast.
- **Proof of Concept**
- This component is the visual of the whole work. You can record a demonstration video or attach screenshots.
- **Impact**
- Write about the real-life impact, How an attacker can take advantage if he/she successfully exploits the vulnerability.
- What type of possible damages could be done? (avoid writing about the theoretical impact)
- Should align with the business objective of the organization
**Sample Report**
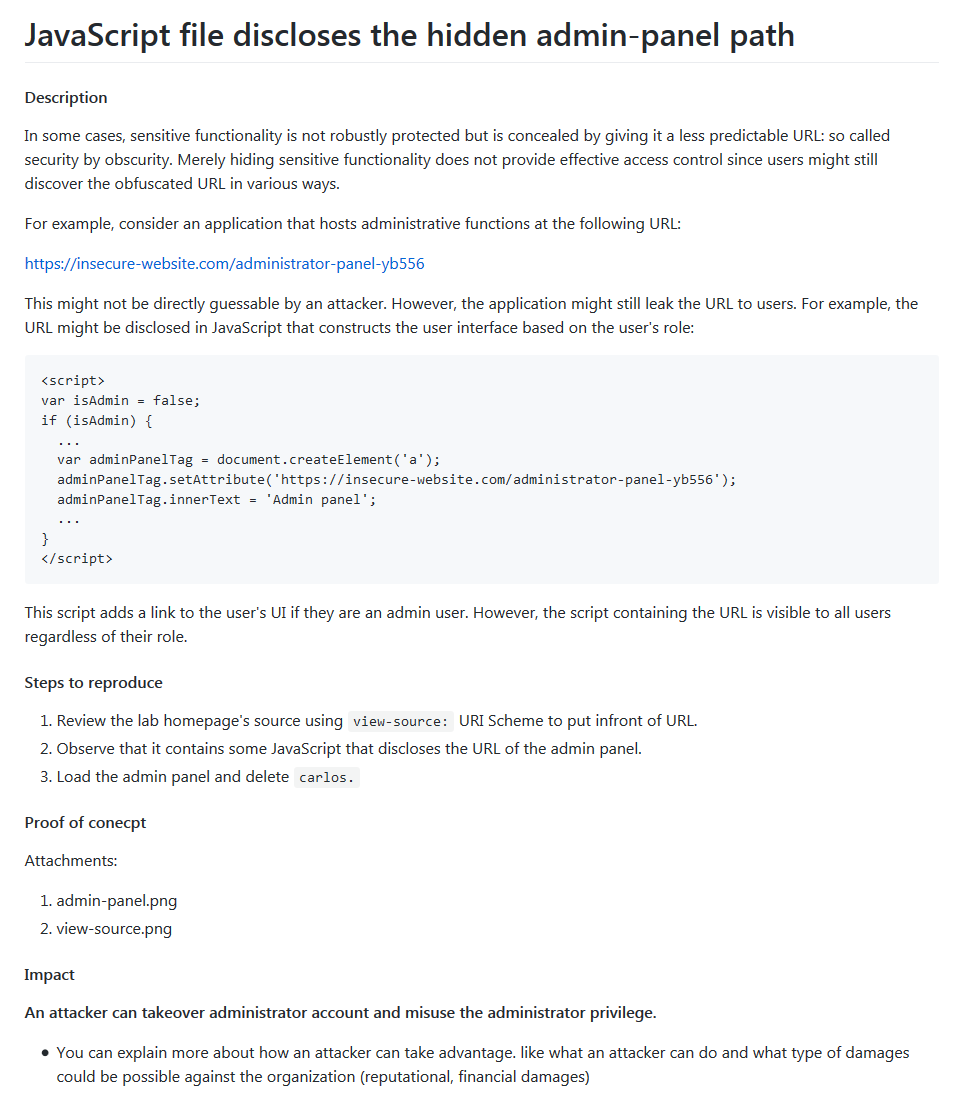
### Some additional Tips
1. **Don't do bug bounty as a full time** in the beginning (although I suggest don't do it full time at any point). There is no guarantee to get bugs every other day, there is no stability. Always keep multiple sources of income (bug bounty not being the primary).
2. **Stay updated**, learning should never stop. Join twitter, follow good people, maintain the curiosity to learn something new every day. Read writeups, blogs and keep expanding your knowledge.
3. Always see **bug bounty as a medium to enhance your skills**. Money will come only after you have the skills. Take money as a motivation only.
4. **Don't be dependent on automation**. You can't expect a tool to generate money for you. Automation is everywhere. The key to success in Bug Bounty is to be unique. Build your own methodology, learn from others and apply on your own.
5. Always try to escalate the severity of the bug, **Keep a broader mindset**. An RCE always has higher impact than arbitrary file upload.
6. It's not necessary that a vulnerability will be rewarded based on the industry defined standard impact. The asset owners **rate the issue with a risk rating**, often calculated as *impact * likelyhood* (exploitability). For example, an SQL Injection by default has a Critical impact, but if the application is accessible only inside the organization VPN and doesn't contain any user data/PII in the database, the likelyhood of the exploitation is reduced, so does the risk.
6. **Stay connected to the community**. Learn and contribute. There is always someone better than you in something. don't miss an opportunity to network. Join forums, go to conferences and hacking events, meet people, learn from their experiences.
7. **Always be helpful**.