https://github.com/vah13/extractTVpasswords
tool to extract passwords from TeamViewer memory using Frida
https://github.com/vah13/extractTVpasswords
cplusplus frida hacking python teamviewer
Last synced: 12 months ago
JSON representation
tool to extract passwords from TeamViewer memory using Frida
- Host: GitHub
- URL: https://github.com/vah13/extractTVpasswords
- Owner: vah13
- Created: 2017-08-01T19:50:03.000Z (over 8 years ago)
- Default Branch: master
- Last Pushed: 2018-07-17T07:05:20.000Z (over 7 years ago)
- Last Synced: 2024-07-31T13:15:03.755Z (over 1 year ago)
- Topics: cplusplus, frida, hacking, python, teamviewer
- Language: C++
- Homepage:
- Size: 1.26 MB
- Stars: 463
- Watchers: 32
- Forks: 116
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - vah13/extractTVpasswords - tool to extract passwords from TeamViewer memory using Frida (C++)
README
# Extract password from TeamViewer memory using Frida (CVE-2018-14333)
Hi there, in this article we want to tell about our little research about password security in TeamViewer. The method can help during the pentest time for post exploitation to get access to another machine using TeamViewer.
## TeamViewer automatically authentication
A few days ago I worked on my windows cloud VPS with TeamViewer (where I set a custom password). After work I disconnected, at the next time when I wanted to connect, I saw that TeamViewer had auto-filled the password.
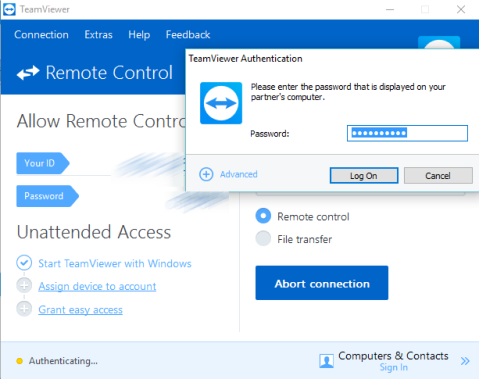
I think “Interesting, how can i get access to the password? How is the password stored in my computer?”
## Password location
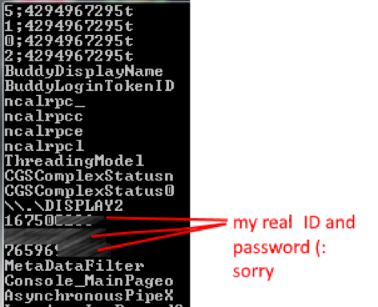
I dumped the memory of the TeamViewer and grepped password.
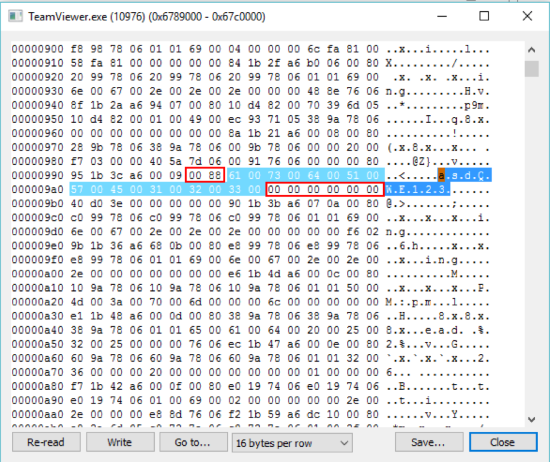
Ooo yeees, 😊 password in the memory is stored in Unicode format. It turns out that if you finish work with TeamViewer and don’t kill the process (or exit from TeamViewer
the password will be stored in memory)
After analyzing we understood that the first red area is a start magic data, in the second one – end magic data (from time to time, end magic data has this value = 00 00 00 20 00 00).
## Script for getting password
To extract passwords from memory we wrote two mini programs, in Python and C++ language.
Thx Frida team for a wonderful tool! Our python script attaches to the TeamViewer.exe process, gets the base address and memory size of each library in this process. After that, it dumps one by one memory area, searches parts with [00 88] bytes at the start and [00 00 00] bytes in the end and copies them in the array. The next and the last step is choosing end decoding raws according to the regexp and password policy.
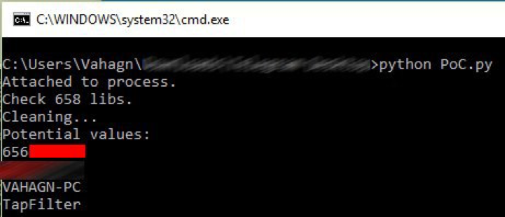
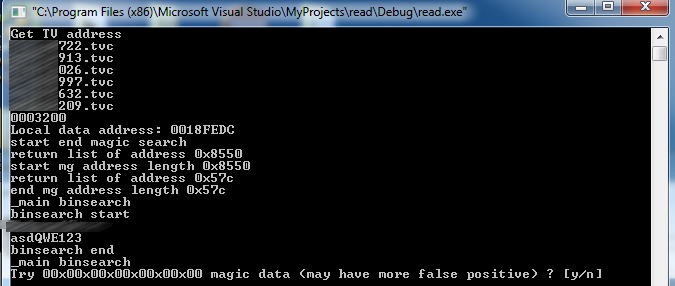
After executing the C++ code, you will get this view “asdQWE123” is the password
### For the future
1. The programs can extract well remote ID and passwords, but he also gets some false positive dates. If we will have free time, we will try to reduce false positive rates.
2. Optimize C++ code from https://github.com/vah13/extractTVpasswords
#### examples
c++ example
python example

[@NewFranny](https://twitter.com/NewFranny)
[@vah_13](https://twitter.com/vah_13)