https://github.com/veinar/envcloak
A secure and easy-to-use tool for managing sensitive data with built-in encryption, decryption, and key management. Protect your secrets during development, testing, and deployment with CLI command + Python library support.
https://github.com/veinar/envcloak
cicd cicd-pipeline cli-tool decryption devops encryption encryption-decryption env environment-variables python-library secret-management secret-sharing secrets security sensitive-data-security tool tooling tools validation
Last synced: 5 months ago
JSON representation
A secure and easy-to-use tool for managing sensitive data with built-in encryption, decryption, and key management. Protect your secrets during development, testing, and deployment with CLI command + Python library support.
- Host: GitHub
- URL: https://github.com/veinar/envcloak
- Owner: Veinar
- License: apache-2.0
- Created: 2024-11-19T21:45:16.000Z (about 1 year ago)
- Default Branch: develop
- Last Pushed: 2024-12-14T00:54:27.000Z (about 1 year ago)
- Last Synced: 2025-06-22T03:45:49.393Z (8 months ago)
- Topics: cicd, cicd-pipeline, cli-tool, decryption, devops, encryption, encryption-decryption, env, environment-variables, python-library, secret-management, secret-sharing, secrets, security, sensitive-data-security, tool, tooling, tools, validation
- Language: Python
- Homepage:
- Size: 283 KB
- Stars: 18
- Watchers: 1
- Forks: 7
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
- Changelog: CHANGELOG
- Contributing: CONTRIBUTING.md
- License: LICENSE
- Code of conduct: CODE_OF_CONDUCT.md
- Security: SECURITY.md
Awesome Lists containing this project
README

⚠️ IMPORTANT NOTE: EnvCloak is NOT Limited to .env Files!⚠️
EnvCloak was originally built to secure .env files, but it can encrypt and decrypt any file type.
Use it for .json, .yaml, .txt, binary files, or any sensitive data.
The name may be misleading, but the tool is far more versatile than it suggests!
# 🔒 EnvCloak
> "Because Your Secrets Deserve Better Than Plaintext!"






[](https://codecov.io/gh/Veinar/envcloak)
[](https://www.codefactor.io/repository/github/veinar/envcloak)
[](https://www.bestpractices.dev/projects/9736)




Welcome to EnvCloak, the ultimate sidekick for developers, ops folks, and anyone who’s ever accidentally committed an API key to version control. (Yes, I know… it happens to the best of us. 😅) EnvCloak takes the stress out of managing environment variables by wrapping them in the cozy blanket of encryption, so you can focus on building awesome things—without the lingering fear of a security breach.
> If you find EnvCloak useful, please ⭐ the repository. It helps others discover this project! - thank you!
## 🛠️ Installation
In order to install `envcloak` simply run:
```bash
pip install envcloak
```
or if you want `dev` tools too 😎:
```bash
pip install envcloak[dev]
```
> 👋 There are also [self-contained binaries](examples/cli/README.md#get-yourself-a-envcloak-without-requirement-to-use-python-) for `Windows`, `Linux` and `MacOS`, don't have to use python at all! 🥳
## 🚀 Example Workflow
> ℹ️ More examples are present in [examples](./examples) section.
### Generating key:
```bash
# With password and salt
envcloak generate-key-from-password --password "YourTopSecretPassword" \
--salt "e3a1c8b0d4f6e2c7a5b9d6f0cr2ad1a2" --output secretkey.key
# With password without salt (we will add random salt then)
envcloak generate-key-from-password --password "YourTopSecretPassword" --output secretkey.key
# From random password and salt
envcloak generate-key --output secretkey.key
```
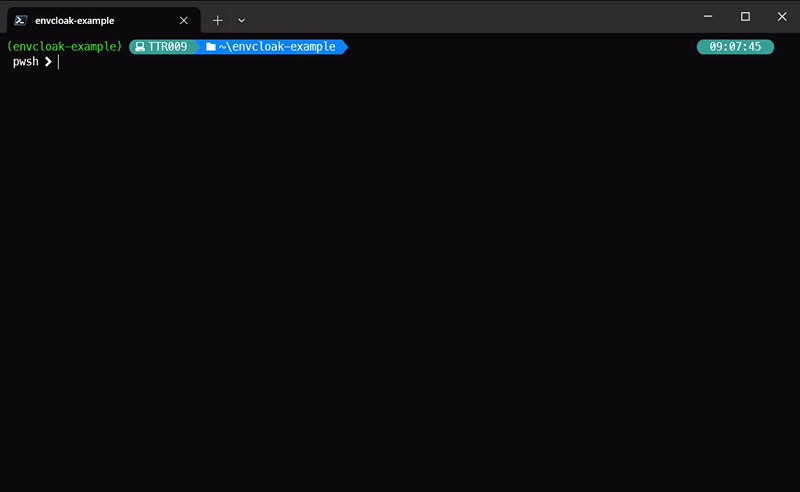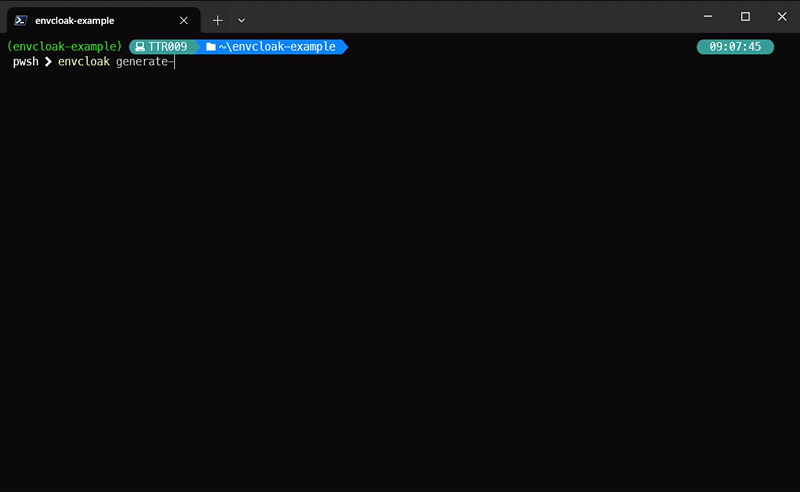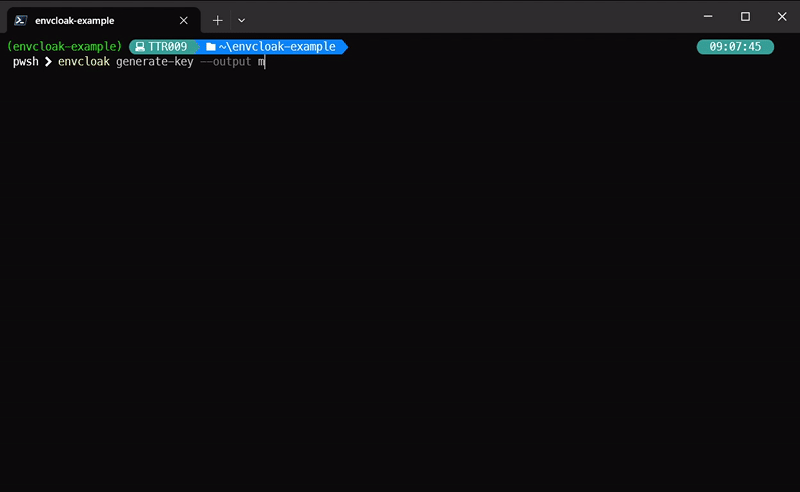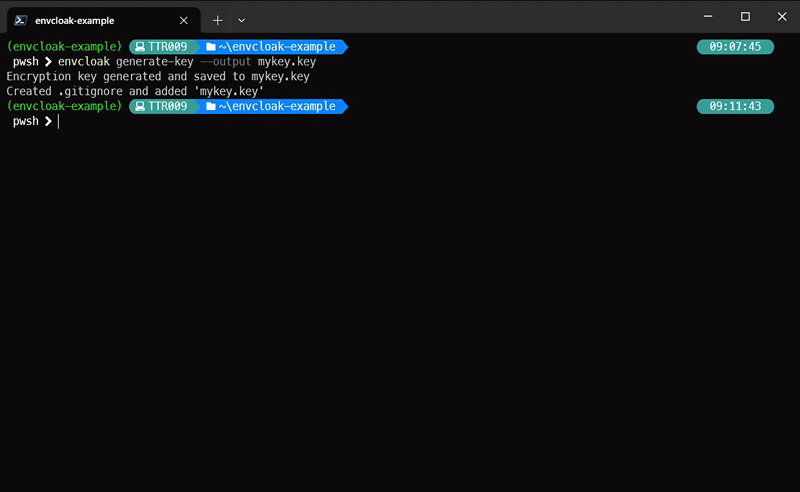
> **What it does:** generates your private key used to encrypt and decrypt files. **Appends (or creates if needed) .gitignore as well** as super-hero should! 🎉
> ⚠ **If someone knows your password and salt (option 1) can recreate same `key` - keep those variables safe as `key` itself** ⚠
### Encrypting Variables:
> ⚠️ This tool allows to encrypt more `.env` is just an example! 😎
```bash
envcloak encrypt --input .env --output .env.enc --key-file mykey.key
```
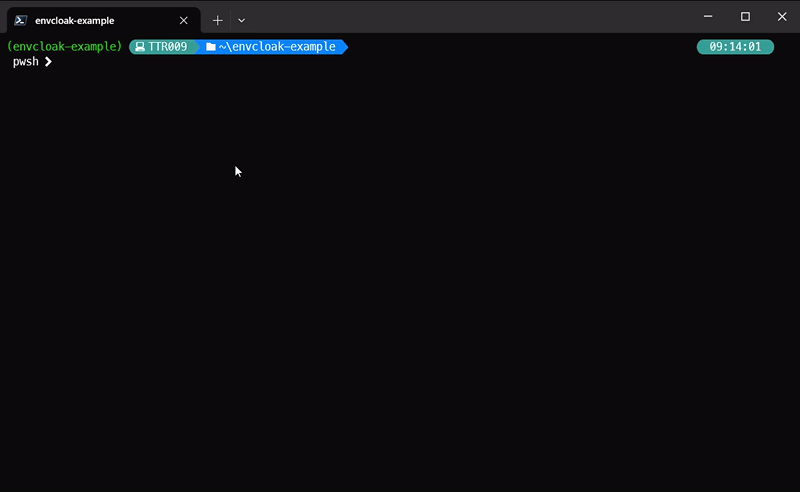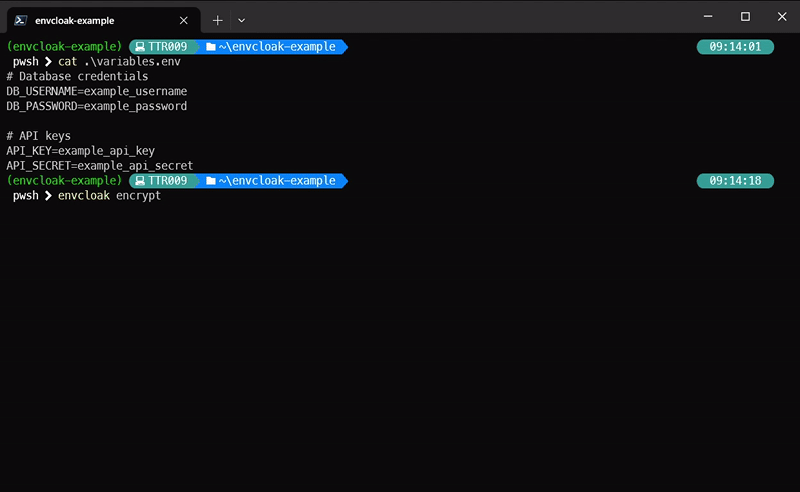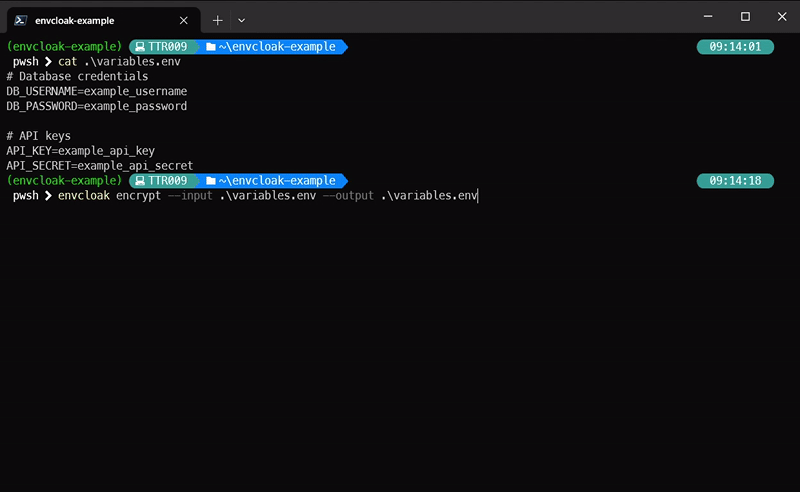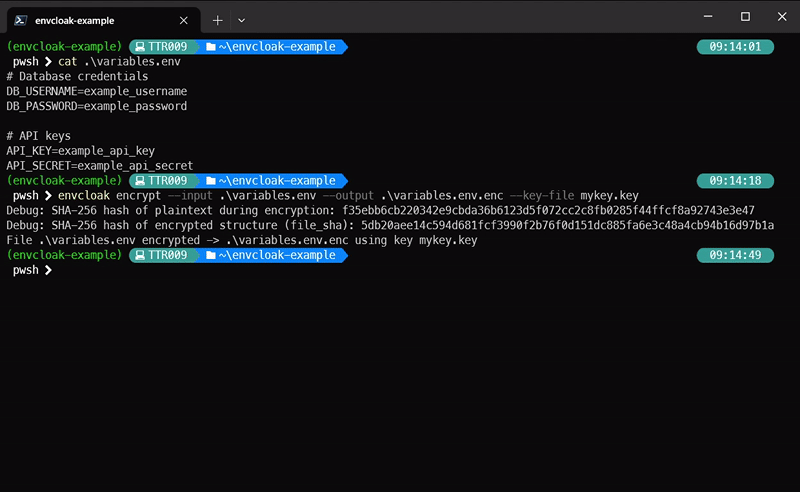
> **What it does:** Encrypts your `.env` file with a specified key, outputting a sparkling `.env.enc` file.
### Decrypting Variables:
```bash
envcloak decrypt --input .env.enc --output .env --key-file mykey.key
```
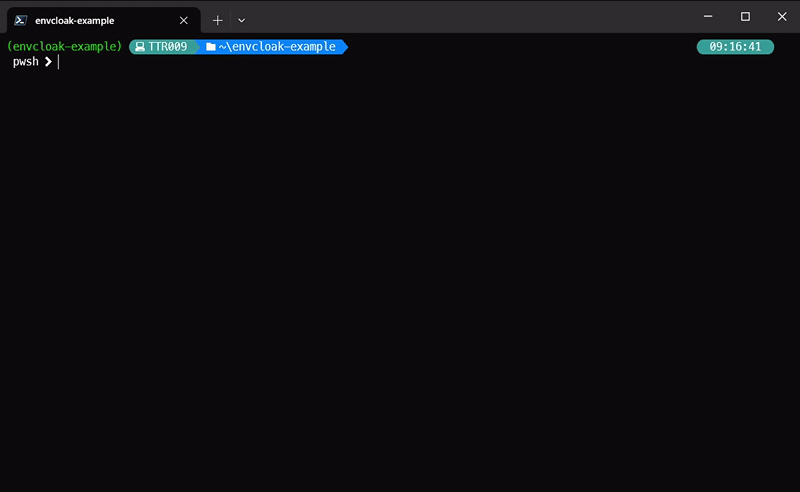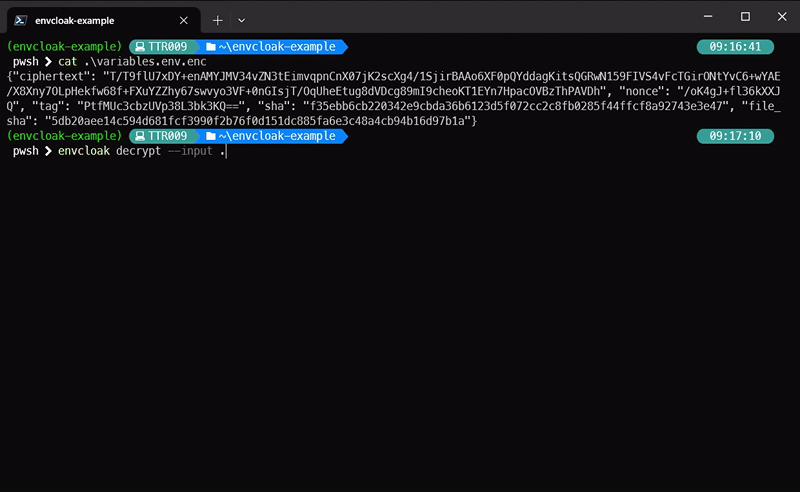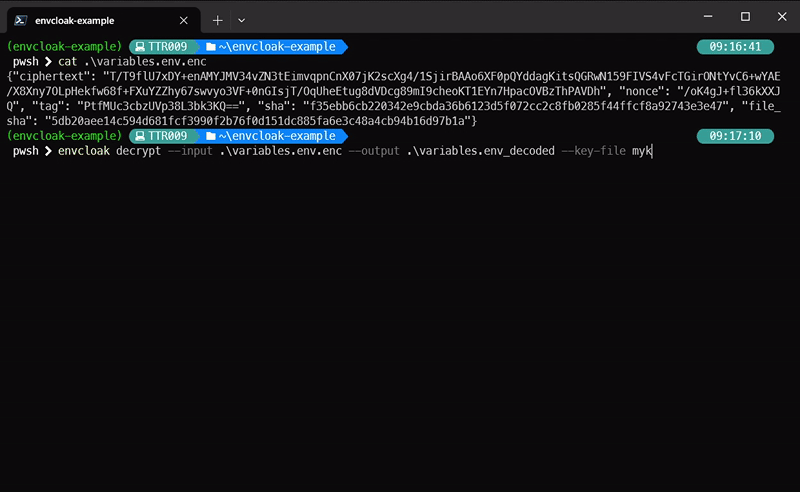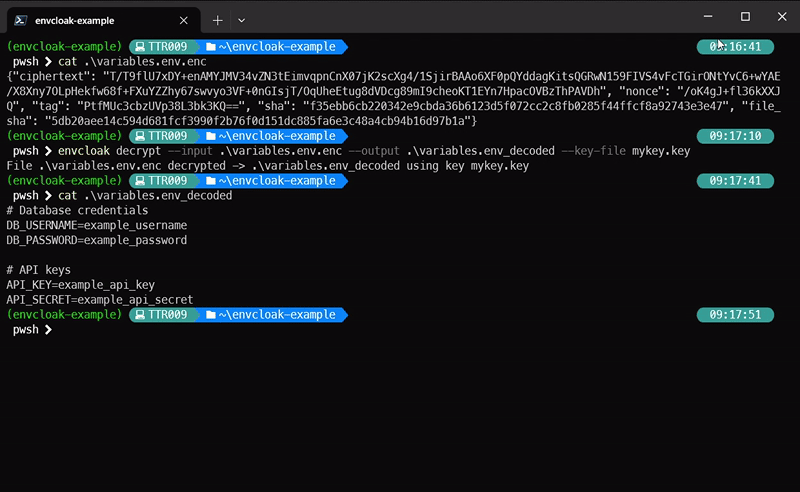
> **What it does:** Decrypts the `.env.enc` file back to `.env` using the same key. Voilà!
or you may want to use it ...
### 🐍 In Your Python Code
```python
from envcloak import load_encrypted_env
load_encrypted_env('.env.enc', key_file='mykey.key').to_os_env()
# Now os.environ contains the decrypted variables
```
> **What it does:** Loads decrypted variables directly into `os.environ`. Secrets delivered, stress-free.
## 🛠️ Implementation Details
🔑 Encryption Algorithm
* Powered by AES-256-GCM for speed and security.
* Provides [`sha3` validation](docs/sha_validation.md) of files and content.
🗝️ Key Storage
* Local key files with strict permissions.
* Secure environment variables for CI/CD systems.
🗂️ File Handling
* Works with individual files.
* Works with directories using `--directory` instead of `--input` on `encrypt` and `decrypt`.
> ℹ️ EnvCloak process files in batch one-by-one.
* Can [recursively](docs/recursive.md) encrypt or decrypt directories.
* Can list files in directory that will be encrypted using `--preview` flag (ℹ️ only for directories and it does not commit the operation!).
🚦 Error Handling
* Clear, friendly error messages for any hiccups.
* Gracefully handles missing keys or corrupted files.
✅ Compatibility of pipelines and systems
* k8s / OKD / OCP deployments
* Jenkins pipelines
* Azure Pipelines
* Github Workflows
* Gitlab CI/CD Pipelines
## 🎉 Why EnvCloak?
Because you deserve peace of mind. EnvCloak wraps your environment variables in layers of encryption goodness, protecting them from prying eyes and accidental slips. Whether you’re a solo dev or part of a big team, this tool is here to make managing secrets simple, secure, and downright pleasant.
So go ahead—secure your `.env` like a boss. And remember, EnvCloak isn’t just a tool; it’s your secret-keeping partner in crime. (But the good kind of crime. 😎)
### Comparison of EnvCloak with Alternatives
| Tool | Strengths | Weaknesses |
|---------------|----------------------------------------|-----------------------------------------|
| **EnvCloak** | Lightweight, Python-native, simple to integrate with CI/CD workflows. | Limited ecosystem compared to established tools. |
| [**Sops**](https://github.com/mozilla/sops) | Integrates with cloud providers, supports partial file encryption. | More complex to configure for beginners. |
| [**BlackBox**](https://github.com/StackExchange/blackbox) | Simple file-based encryption for Git repos. | Limited to GPG, lacks flexibility. |
| [**Vault**](https://www.vaultproject.io/) | Robust, enterprise-grade with dynamic secrets. | High complexity, overkill for small projects. |
| [**Confidant**](https://lyft.github.io/confidant/) | AWS IAM integration, designed for secure CI/CD workflows. | Requires AWS, limited to its ecosystem. |
| [**Doppler**](https://www.doppler.com/) | Centralized secret management with CI/CD integration. | Paid plans for advanced features, cloud-reliant. |
> **Key Differentiator for EnvCloak**: Focused specifically on Python developers and lightweight CI/CD needs, making it ideal for small to medium projects.
## 🤔 What Do You Think?
We’d love to hear your thoughts about EnvCloak! Open an [issue](https://github.com/Veinar/envcloak/issues) or join the conversation in [Discussions](https://github.com/Veinar/envcloak/discussions).
## 🌟 Hall of Fame
A huge thanks to all our amazing contributors! 🎉
## 🔗 Get Started Today!
Don’t let your API keys end up in the wrong hands (or on Twitter). Grab EnvCloak now and start encrypting like a pro.
Happy `env` (an many other file types) Cloaking! 🕵️♂️