https://github.com/viralmaniar/peekaboo
PeekABoo tool can be used during internal penetration testing when a user needs to enable Remote Desktop on the targeted machine. It uses PowerShell remoting to perform this task. Note: Remote desktop is disabled by default on all Windows operating systems.
https://github.com/viralmaniar/peekaboo
bluekeep infrastructure-testing internal-pentest network-pentest pentest pentest-tool pentest-tools pentesters pentesting powershell remote-desktop security security-tools
Last synced: 4 months ago
JSON representation
PeekABoo tool can be used during internal penetration testing when a user needs to enable Remote Desktop on the targeted machine. It uses PowerShell remoting to perform this task. Note: Remote desktop is disabled by default on all Windows operating systems.
- Host: GitHub
- URL: https://github.com/viralmaniar/peekaboo
- Owner: Viralmaniar
- Created: 2019-04-22T11:21:38.000Z (over 6 years ago)
- Default Branch: master
- Last Pushed: 2019-04-29T06:27:07.000Z (over 6 years ago)
- Last Synced: 2025-04-24T13:42:04.974Z (7 months ago)
- Topics: bluekeep, infrastructure-testing, internal-pentest, network-pentest, pentest, pentest-tool, pentest-tools, pentesters, pentesting, powershell, remote-desktop, security, security-tools
- Language: Python
- Homepage:
- Size: 21.5 KB
- Stars: 138
- Watchers: 11
- Forks: 27
- Open Issues: 1
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# PeekABoo
PeekABoo tool can be used during internal penetration testing when a user needs to enable Remote Desktop on the targeted machine. It uses PowerShell remoting to perform this task.
The tool only works if WinRM is enabled. Since Windows Server 2012 WinRM is enabled by default on all Windows server operating systems, but not on client operating systems.
Note: Remote desktop is disabled by default on all Windows operating systems. User would require local administrator password or administrator privileges on the server to enable RDP on a targeted machine.
Any suggestions or ideas for this tool are welcome - just tweet me on [@ManiarViral](https://twitter.com/maniarviral)
# Screenshots
Targeted machine on an internal network has RDP disabled:

Enabling remote desktop service on a targeted machine by pressing `option 2`:

Successfully enabled remote desktop service on a targeted machine:
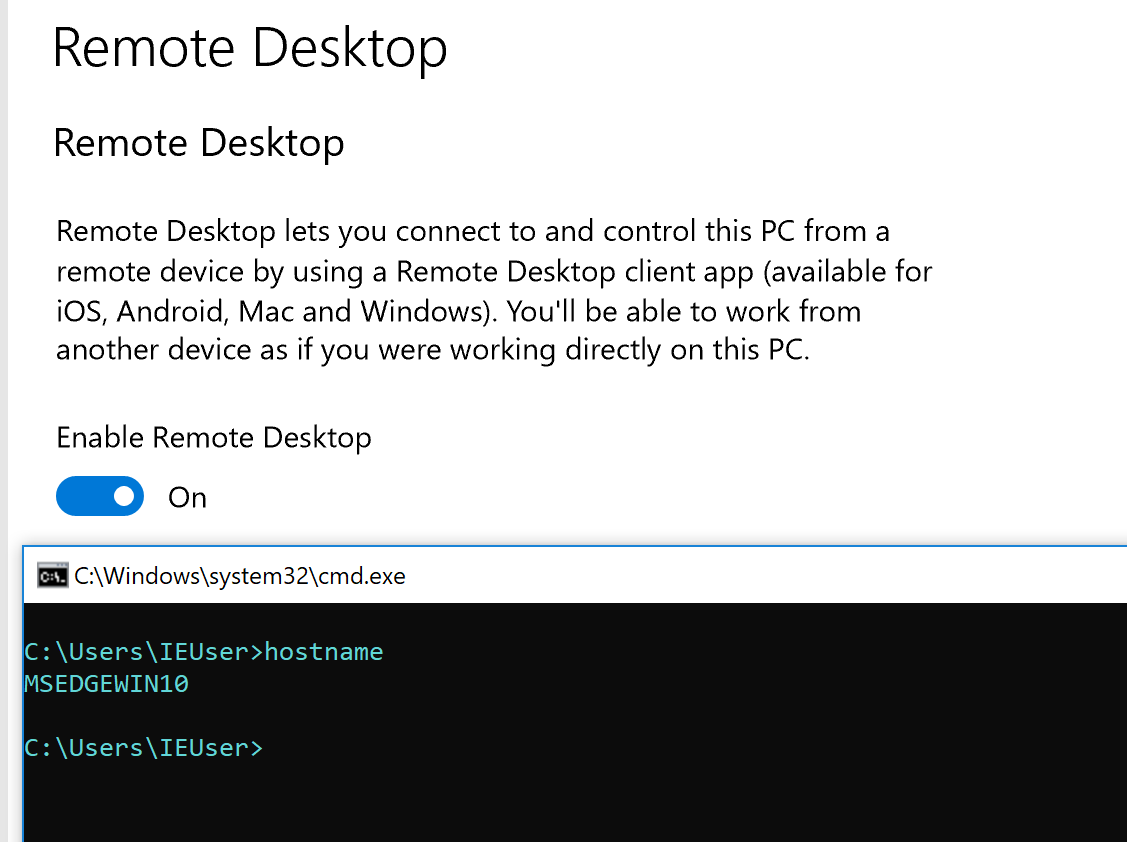
# How to install?
- git clone https://github.com/Viralmaniar/PeekABoo.git
- cd PeekABoo
- python peekaboo.py
# How do I use this?
- Press 1: This will set the PowerShell to unrestricted mode.
- Press 2: It enables the `Remote Desktop` on the targeted machine and shows the RDP port (3389) status.
- Press 3: It disables the `Remote Desktop` on the targeted machine.
- Press 4: To exit from the program.
# My Windows machine do not have Python installed, what should I do?
- Download an exe from the release section of the Github along with PowerShell files available [here](https://github.com/Viralmaniar/PeekABoo/releases) or do it on your own using PyInstaller after reviewing the source code.
- Compile `peekaboo.py` into an executable using [Pyinstaller](https://github.com/pyinstaller/pyinstaller)
- PyInstaller is available on PyPI. You can install it through pip:
pip install pyinstaller
# Questions?
Twitter: https://twitter.com/maniarviral
LinkedIn: https://au.linkedin.com/in/viralmaniar
# Contribution & License

This work is licensed under a Creative Commons Attribution 4.0 International License.
Want to contribute? Please fork it and hit up with a pull request.
Any suggestions or ideas for this tool are welcome - just tweet me on [@ManiarViral](https://twitter.com/maniarviral)