https://github.com/vsec7/BurpSuite-Xkeys
A Burp Suite Extension to extract interesting strings (key, secret, token, or etc.) from a webpage.
https://github.com/vsec7/BurpSuite-Xkeys
burp-extensions burpsuite hacking osint pentest-tool pentesting
Last synced: 11 months ago
JSON representation
A Burp Suite Extension to extract interesting strings (key, secret, token, or etc.) from a webpage.
- Host: GitHub
- URL: https://github.com/vsec7/BurpSuite-Xkeys
- Owner: vsec7
- Created: 2020-06-15T09:46:58.000Z (over 5 years ago)
- Default Branch: master
- Last Pushed: 2024-07-09T23:32:40.000Z (over 1 year ago)
- Last Synced: 2024-11-09T06:38:41.730Z (over 1 year ago)
- Topics: burp-extensions, burpsuite, hacking, osint, pentest-tool, pentesting
- Language: Python
- Size: 106 KB
- Stars: 250
- Watchers: 14
- Forks: 54
- Open Issues: 3
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-burp-extensions - Xkeys - A Burp Suite Extension to extract interesting strings (key, secret, token, or etc.) from a webpage. and lists them as information issues. (Vulnerability Specific Extensions / Sensitive Data Exposure)
- awesome-hacking-lists - vsec7/BurpSuite-Xkeys - A Burp Suite Extension to extract interesting strings (key, secret, token, or etc.) from a webpage. (Python)
README
# Xkeys (BurpSuite Extension)
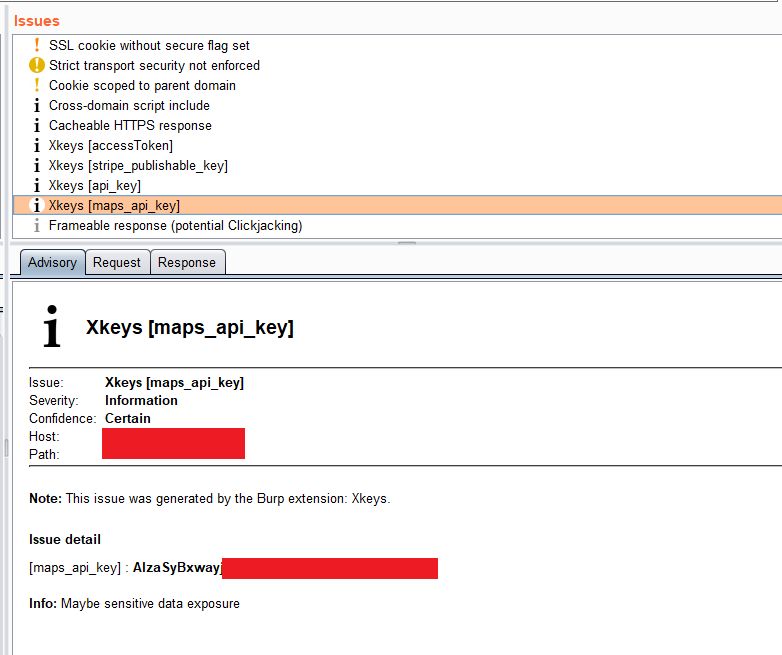
## Description
A Burp Suite Extension to extract interesting strings (key, secret, token, or etc.) from a webpage. and lists them as information issues.
Type : Passive Scanner
# Setup
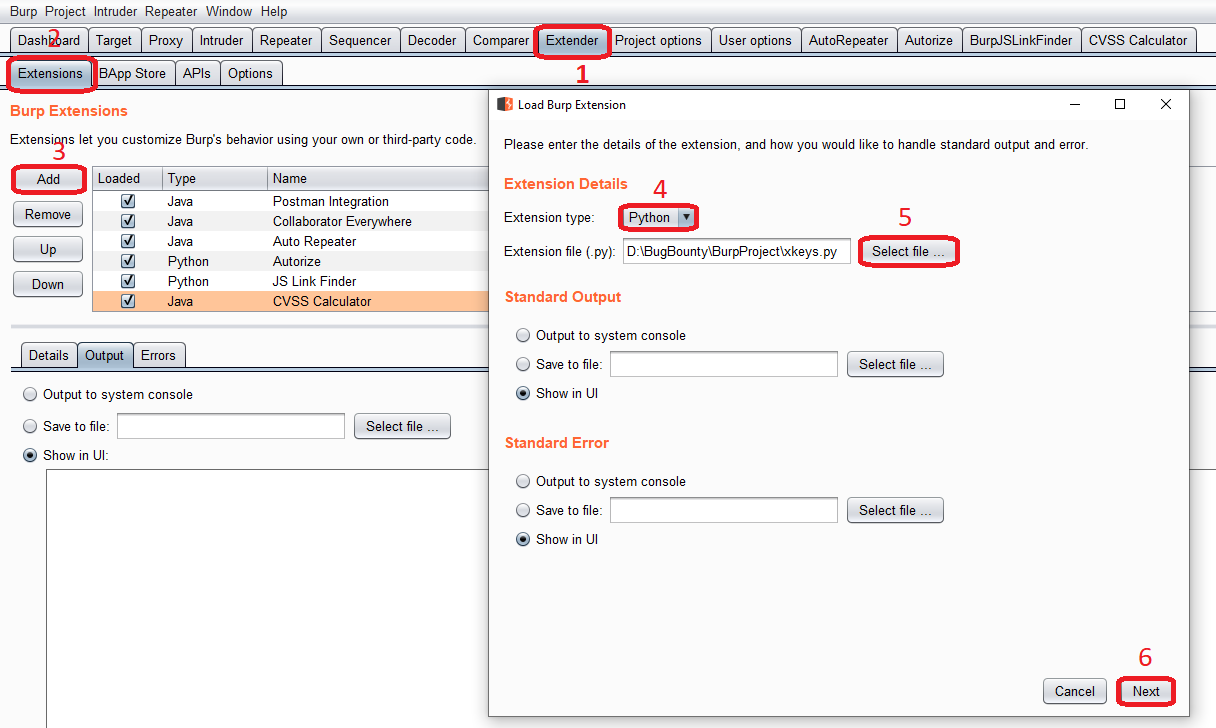
- Setup the python environment by providing the Jython.jar file in the 'Options' tab under 'Extender' in Burp Suite.
- Download the BurpSuite-Xkeys.zip.
- In the 'Extensions' tab under 'Extender', select 'Add'.
- Change the extension type to 'Python'.
- Provide the path of the file "Xkeys.py" and click on 'Next'.
# Usage
- The extension will start identifying assets through passive scan.
## Result
- The extension will show on issues box and on output extender
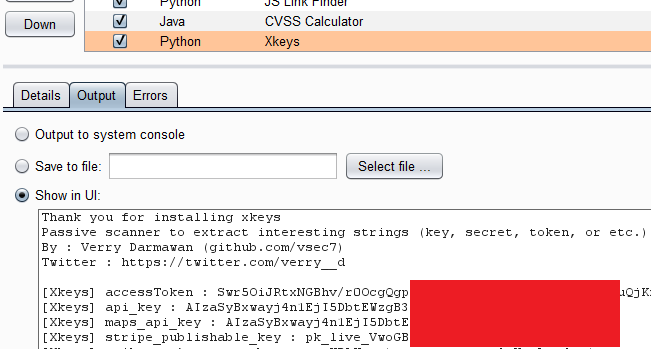
## Possible Value Extraction
```
{keyword}=
{keyword}=
{keyword} =
{keyword} =
{keyword}'=''
{keyword}'= ''
{keyword}' =''
{keyword}' = ''
{keyword}"=""
{keyword}"= ""
{keyword}" =""
{keyword}" = ""
{keyword}":""
{keyword}": ""
{keyword}" :""
{keyword}" : ""
{keyword}=&
```
## Requirements
- [Jython 2.7.0](https://www.jython.org/download.html)
- [Burp Suite Pro](https://portswigger.net/burp)
## Code Credits:
```
# PortSwigger example-scanner-checks: https://github.com/PortSwigger/example-scanner-checks
# RedHuntLabs BurpSuite-Asset_Discover: https://github.com/redhuntlabs/BurpSuite-Asset_Discover
```
- Sec7or Team
- Surabaya Hacker Link