https://github.com/wallarm/api-firewall
Fast and light-weight API proxy firewall for request and response validation by OpenAPI specs.
https://github.com/wallarm/api-firewall
api api-firewall api-gateway api-security api-waf api-wrapper apigateway firewall openapi openapi-security openapi-spec openapi-specification proxy rest-security security security-tools swagger waf web-application-firewall web-application-security
Last synced: 10 months ago
JSON representation
Fast and light-weight API proxy firewall for request and response validation by OpenAPI specs.
- Host: GitHub
- URL: https://github.com/wallarm/api-firewall
- Owner: wallarm
- License: mpl-2.0
- Created: 2021-05-14T02:08:36.000Z (almost 5 years ago)
- Default Branch: main
- Last Pushed: 2025-04-01T11:11:58.000Z (11 months ago)
- Last Synced: 2025-04-03T20:48:02.029Z (11 months ago)
- Topics: api, api-firewall, api-gateway, api-security, api-waf, api-wrapper, apigateway, firewall, openapi, openapi-security, openapi-spec, openapi-specification, proxy, rest-security, security, security-tools, swagger, waf, web-application-firewall, web-application-security
- Language: Go
- Homepage: https://wallarm.github.io/api-firewall/
- Size: 1.5 MB
- Stars: 606
- Watchers: 24
- Forks: 58
- Open Issues: 5
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-api-security - Wallarm Free API Firewall - weight API proxy firewall for request and response validation by OpenAPI specs. | (Firewalls)
README
# Open Source API Firewall by Wallarm [](https://www.blackhat.com/us-22/arsenal/schedule/index.html#open-source-api-firewall-new-features--functionalities-28038)
API Firewall is a high-performance proxy with API request and response validation based on [OpenAPI](https://wallarm.github.io/api-firewall/installation-guides/docker-container/) and [GraphQL](https://wallarm.github.io/api-firewall/installation-guides/graphql/docker-container/) schemas. It is designed to protect REST and GraphQL API endpoints in cloud-native environments. API Firewall provides API hardening with the use of a positive security model allowing calls that match a predefined API specification for requests and responses, while rejecting everything else.
The **key features** of API Firewall are:
* Secure REST and GraphQL API endpoints by blocking malicious requests
* Stop API data breaches by blocking malformed API responses
* Discover Shadow API endpoints
* Validate JWT access tokens for OAuth 2.0 protocol-based authentication
* Denylist compromised API tokens, keys, and Cookies
* AllowIPList - Restrict access to endpoints by defining a list of allowed IP addresses
* Wide Range Attacks Protection: The API Firewall supports ModSecurity Rules and OWASP ModSecurity Core Rule Set
The product is **open source**, available at DockerHub and already got 1 billion (!!!) pulls. To support this project, you can star the [repository](https://hub.docker.com/r/wallarm/api-firewall).
## Operating modes
Wallarm API Firewall offers several operating modes:
* [`PROXY`](https://wallarm.github.io/api-firewall/installation-guides/docker-container/): validates HTTP requests and responses against OpenAPI 3.0 and proxies matching requests to the backend.
* [`API`](https://wallarm.github.io/api-firewall/installation-guides/api-mode/): validates individual requests against OpenAPI 3.0 without further proxying.
* [`graphql`](https://wallarm.github.io/api-firewall/installation-guides/graphql/docker-container/): validates HTTP and WebSocket requests against GraphQL schema and proxies matching requests to the backend.
## Use cases
### Running in blocking mode
* Block malicious requests that do not match the specification
* Block malformed API responses to stop data breaches and sensitive information exposure
### Running in monitoring mode
* Discover Shadow APIs and undocumented API endpoints
* Log malformed requests and responses that do not match the specification
## API schema validation and positive security model
When starting API Firewall, you should provide the REST or GraphQL API specification of the application to be protected with API Firewall. The started API Firewall will operate as a reverse proxy and validate whether requests and responses match the schema defined in the specification.
The traffic that does not match the schema will be logged using the [`STDOUT` and `STDERR` Docker services](https://docs.docker.com/config/containers/logging/) or blocked (depending on the configured API Firewall operation mode). When operating in the logging mode on REST API, API Firewall also logs so-called shadow API endpoints, those that are not covered in API specification but respond to requests (except for endpoints returning the code `404`).
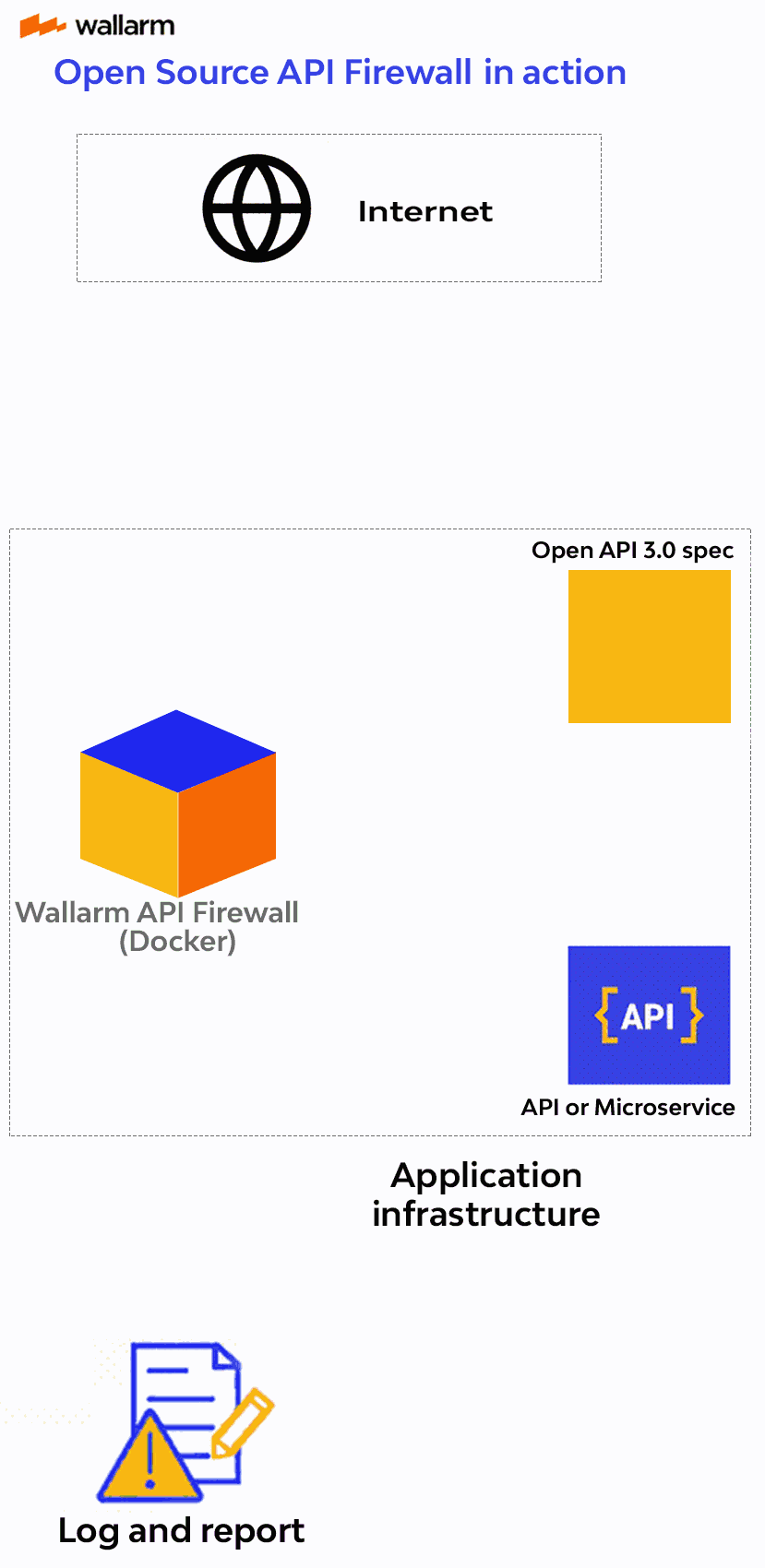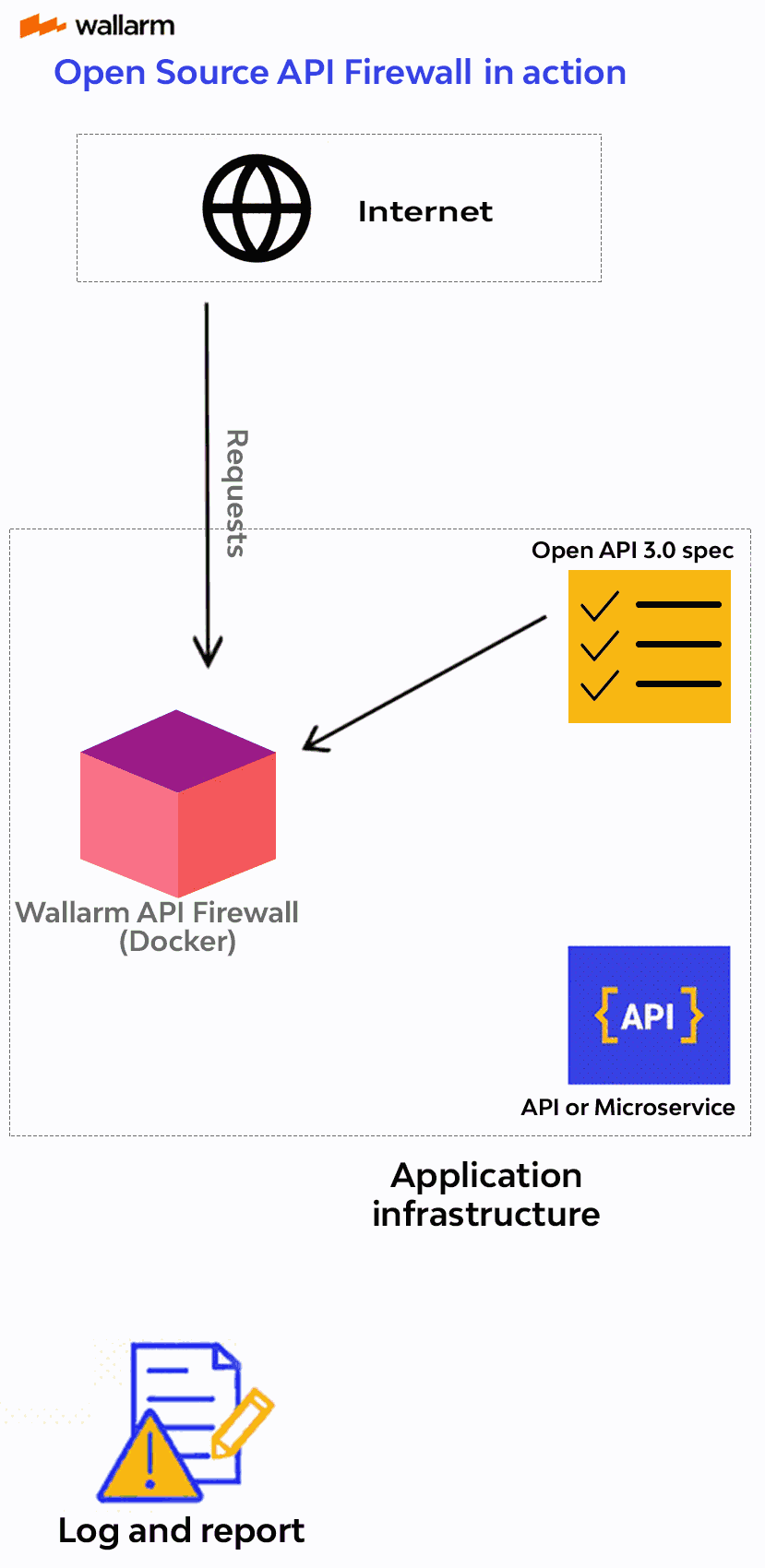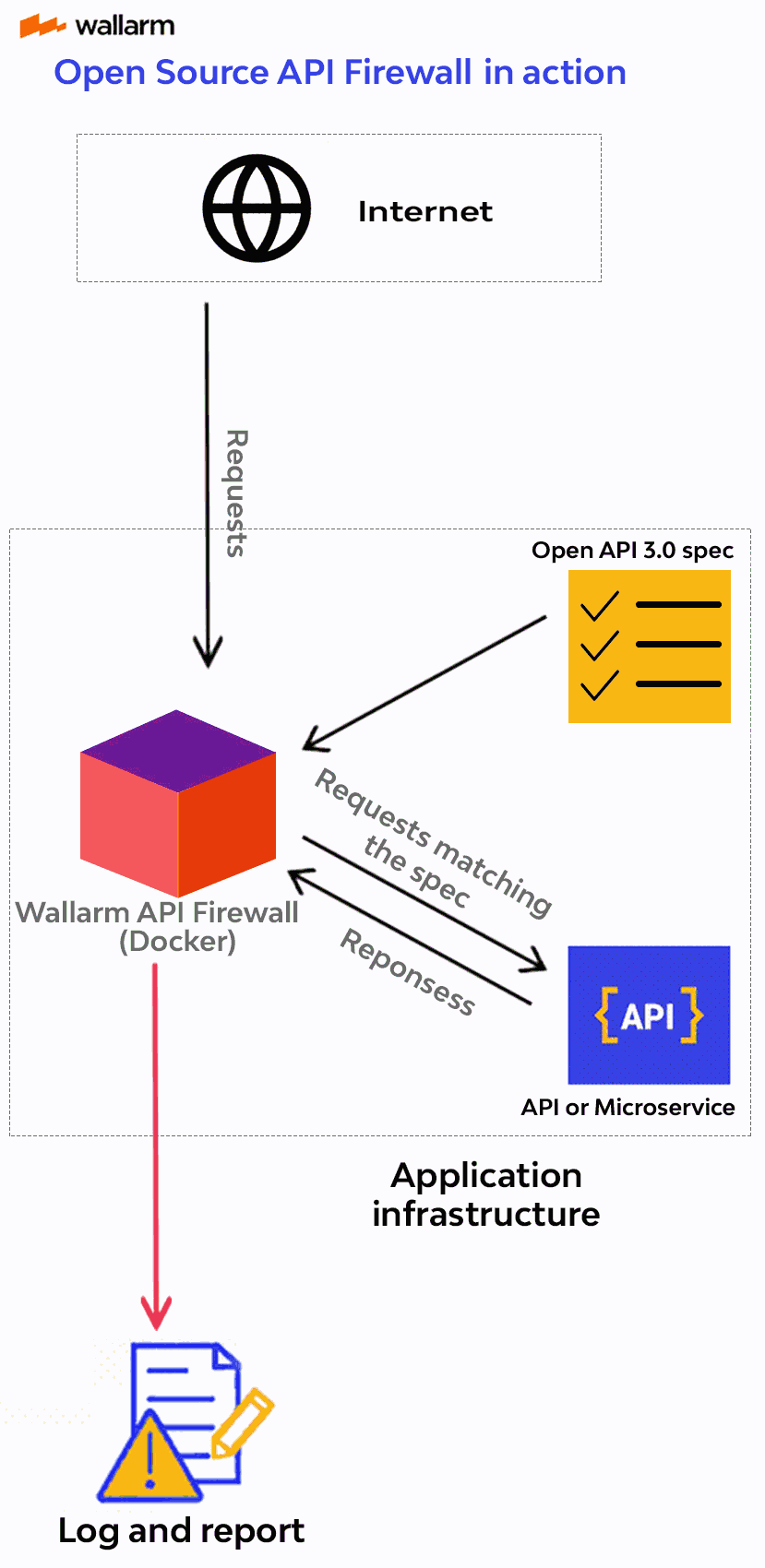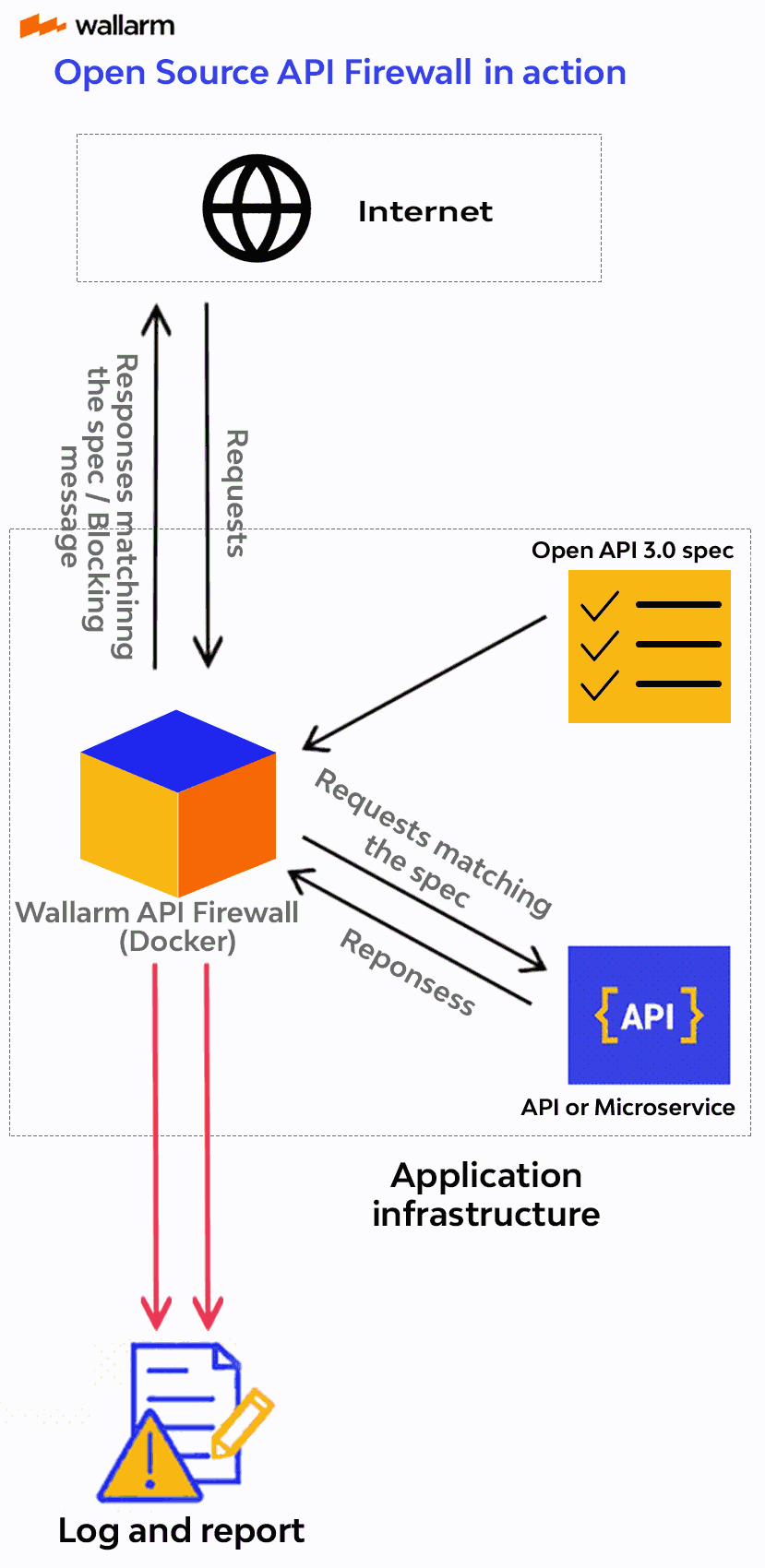
By allowing you to set the traffic requirements with the API specification, API Firewall relies on a positive security model.
## Technical data
[API Firewall works](https://www.wallarm.com/what/the-concept-of-a-firewall) as a reverse proxy with a built-in OpenAPI 3.0 or GraphQL request and response validator. It is written in Golang and using fasthttp proxy. The project is optimized for extreme performance and near-zero added latency.
During the processing of incoming requests, the API Firewall recognizes a range of `Content-Type` header values, including:
* `application/json`
* `application/xml`
* `application/octet-stream`
* `application/x-www-form-urlencoded`
* `application/x-yaml`
* `application/yaml`
* `application/zip`
* `multipart/form-data`
* `text/csv`
* `text/plain`
* `+json` structured syntax suffixes
* `+xml` structured syntax suffixes
* `+yaml` structured syntax suffixes
* `+csv` structured syntax suffixes
## Starting API Firewall
To download, install, and start API Firewall on Docker, refer to:
* [REST API guide](https://wallarm.github.io/api-firewall/installation-guides/docker-container/)
* [GraphQL API guide](https://wallarm.github.io/api-firewall/installation-guides/graphql/docker-container/)
## Demos
You can try API Firewall by running the demo environment that deploys an example application protected with API Firewall. There are two available demo environments:
* [API Firewall demo with Docker Compose](https://github.com/wallarm/api-firewall/tree/main/demo/docker-compose)
* [API Firewall demo with Kubernetes](https://github.com/wallarm/api-firewall/tree/main/demo/kubernetes)
## Wallarm's blog articles related to API Firewall
* [Discovering Shadow APIs with API Firewall](https://lab.wallarm.com/discovering-shadow-apis-with-a-api-firewall/)
* [Wallarm API Firewall outperforms NGINX in a production environment](https://lab.wallarm.com/wallarm-api-firewall-outperforms-nginx-in-a-production-environment/)
* [Securing REST APIs for free with OSS APIFW](https://lab.wallarm.com/securing-rest-with-free-api-firewall-how-to-guide/)
## Performance
When creating API Firewall, we prioritized speed and efficiency to ensure that our customers would have the fastest APIs possible. Our latest tests demonstrate that the average time required for API Firewall to process one request is 1.339 ms which is 66% faster than Nginx:
```
API Firewall 0.6.2 with JSON validation
$ ab -c 200 -n 10000 -p ./large.json -T application/json http://127.0.0.1:8282/test/signup
Requests per second: 13005.81 [#/sec] (mean)
Time per request: 15.378 [ms] (mean)
Time per request: 0.077 [ms] (mean, across all concurrent requests)
NGINX 1.18.0 without JSON validation
$ ab -c 200 -n 10000 -p ./large.json -T application/json http://127.0.0.1/test/signup
Requests per second: 7887.76 [#/sec] (mean)
Time per request: 25.356 [ms] (mean)
Time per request: 0.127 [ms] (mean, across all concurrent requests)
```
These performance results are not the only ones we have got during API Firewall testing. Other results along with the methods used to improve API Firewall performance are described in this [Wallarm's blog article](https://lab.wallarm.com/wallarm-api-firewall-outperforms-nginx-in-a-production-environment/).