https://github.com/xy3/v-password-validator
Validate the Strength of a Password in V
https://github.com/xy3/v-password-validator
password password-strength password-validator security vlang vlang-library vlang-module
Last synced: 8 months ago
JSON representation
Validate the Strength of a Password in V
- Host: GitHub
- URL: https://github.com/xy3/v-password-validator
- Owner: xy3
- License: mit
- Created: 2022-02-04T11:45:06.000Z (over 3 years ago)
- Default Branch: main
- Last Pushed: 2023-05-11T17:13:48.000Z (over 2 years ago)
- Last Synced: 2025-01-08T04:53:43.289Z (9 months ago)
- Topics: password, password-strength, password-validator, security, vlang, vlang-library, vlang-module
- Language: V
- Homepage: https://vpm.vlang.io/packages/xy3.passvalid
- Size: 18.6 KB
- Stars: 8
- Watchers: 1
- Forks: 0
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
README
:space_invader: V password validator
Simple password validator using raw entropy values, written in V.
⭐ If you like this project please give it a star! ⭐
---
Heavily influenced by [go-password-validator](https://github.com/wagslane/go-password-validator)
## Installation:
Install using `V`'s builtin `vpm`:
```bash
v install xy3.passvalid
```
Install using `git`:
```bash
cd path/to/your/project
git clone https://github.com/xy3/v-password-validator
```
Then in the wherever you want to use it:
```v
import xy3.passvalid
```
And that's it!
## Usage
## 🚀 Quick Start
```v
import xy3.passvalid
fn main(){
entropy := passvalid.get_entropy("a longer password")
// entropy is a f64, representing the strength in base 2 (bits)
min_entropy_bits := 60
passvalid.validate("some password", min_entropy_bits) or { panic(err) }
// if the password has enough entropy, nothing is returned
// otherwise, a formatted error message is provided explaining
// how to increase the strength of the password
// (safe to show to the client)
}
```
## What Entropy Value Should I Use?
It's up to you. That said, here is a graph that shows some common timings for different values, somewhere in the 50-70 range seems "reasonable".
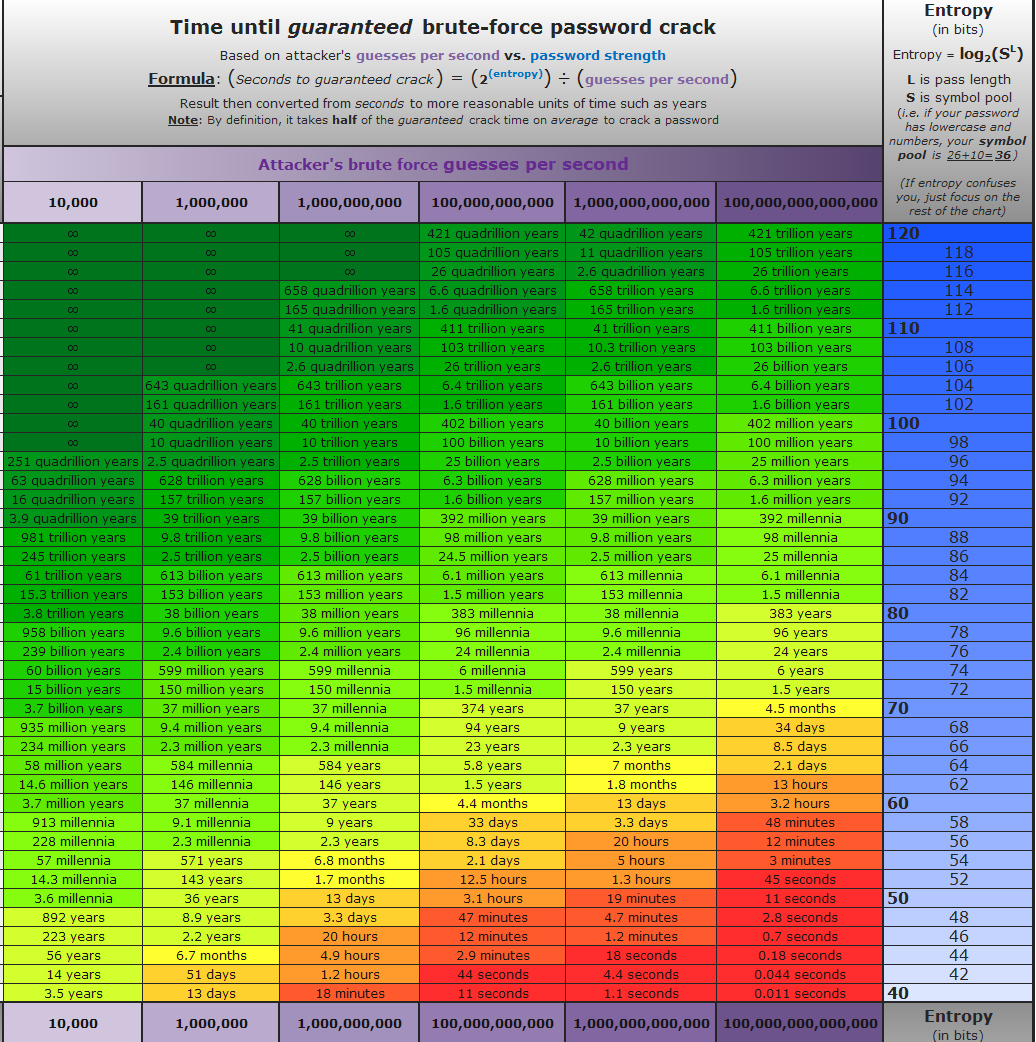
Keep in mind that attackers likely aren't just brute-forcing passwords, if you want protection against common passwords or [PWNed passwords](https://haveibeenpwned.com/) you'll need to do additional work. This library is lightweight, doesn't load large datasets, and doesn't contact external services.